Okta ‘identifying and contacting’ customers potentially affected by Lapsus$ breach
Okta’s chief security officer David Bradbury released a statement on Tuesday afternoon saying Okta “has not been breached and remains fully operational.”
Extortion group Lapsus$ claimed this weekend on its Telegram channel that it had access to Okta’s systems, and the company said on Monday night that it was investigating the claims.
While Bradbury denied that the company was affected by the Lapsus$ hack, it said there was a five-day window of time between January 16 and 21 where an attacker “had access to an Okta support engineer’s laptop,” noting that this “is consistent with the screenshots” that Lapsus$ shared on Telegram.
“The Okta service has not been breached and remains fully operational. There are no corrective actions that need to be taken by our customers. In January 2022, Okta detected an unsuccessful attempt to compromise the account of a customer support engineer working for a third-party provider,” Bradbury said.
“As part of our regular procedures, we alerted the provider to the situation, while simultaneously terminating the user’s active Okta sessions and suspending the individual’s account. Following those actions, we shared pertinent information (including suspicious IP addresses) to supplement their investigation, which was supported by a third-party forensics firm.”
Bradbury said the impact on Okta customers “is limited to the access that support engineers have.”
He explained that these engineers are not able to create and delete users or download customer databases but they do have access to data like Jira tickets and lists of users – which were seen in the Lapsus$ screenshots.
“Support engineers are also able to facilitate the resetting of passwords and multi-factor authentication factors for users, but are unable to obtain those passwords,” Bradbury said.
“We are actively continuing our investigation, including identifying and contacting those customers that may have been impacted. There is no impact to Auth0 customers, and there is no impact to HIPAA and FedRAMP customers.”
Lapsus$ issues a response
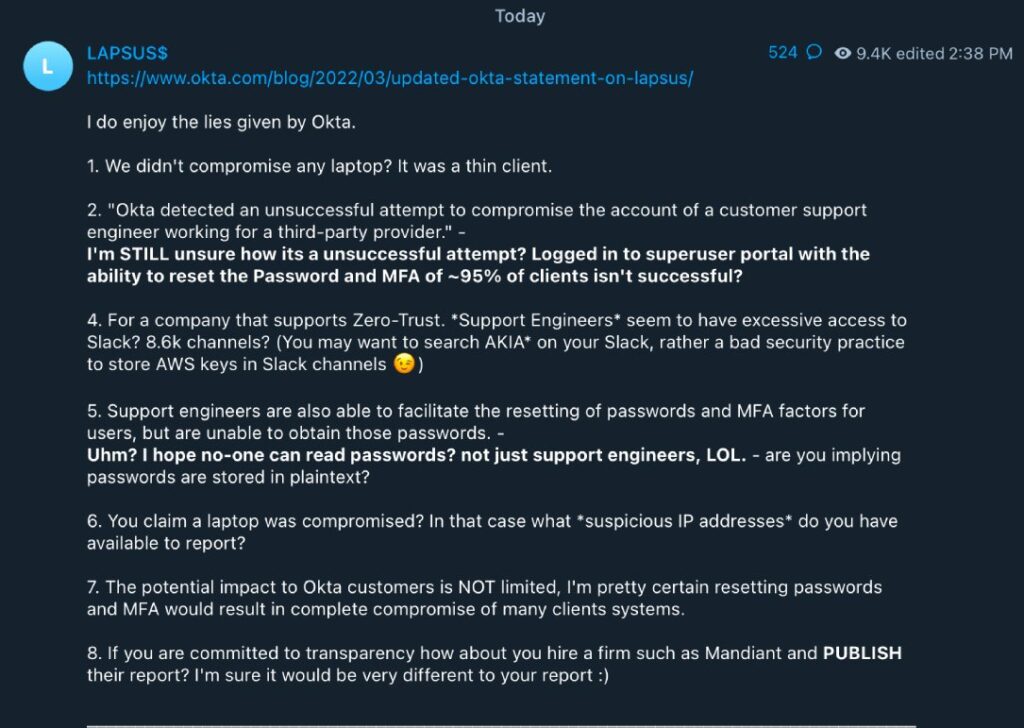
Minutes after the Okta statement was released, members of Lapsus$ took to Telegram to respond to Bradbury. They released a 10-point response to the statement, criticizing Okta for allegedly downplaying the incident.
The group called the statement “lies,” claiming they were able to log into a “superuser portal with the ability to reset the password and MFA of ~95% of clients.” The group made a number of charged claims about Okta’s internal functions, criticizing the company for allegedly providing support engineers with access to more than 8,000 channels on Slack and for storing AWS keys in certain Slack channels.
“The potential impact to Okta customers is NOT limited, I'm pretty certain resetting passwords and MFA would result in complete compromise of many clients systems,” the group claimed before taunting Okta and urging them to hire a security firm to do an assessment of the incident.
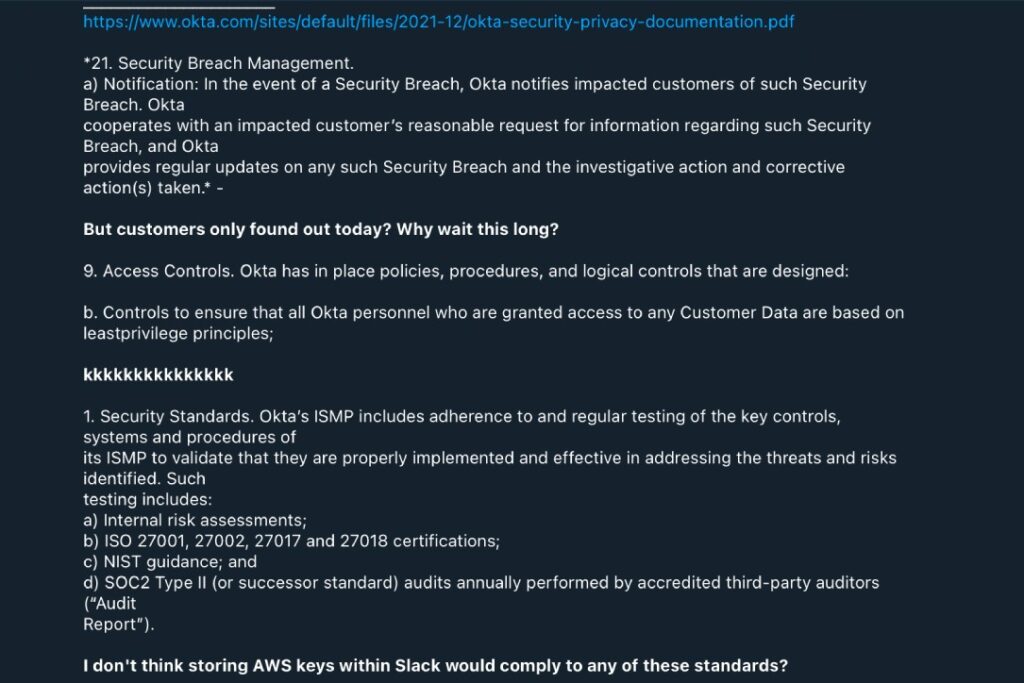
The group also went on to slam Okta for admitting that the breach happened in January but only notifying the public today. Okta did not immediately respond to a request for comment.
Lapsus$ has caused concern in recent months with a string of high-profile attacks. Right before the attack on Okta, the group shared stolen data from Microsoft related to Bing and Cortana products.
The group, which experts believe is based in South America, also drew headlines for previous attacks on NVIDIA, Samsung, Vodafone, Ubisoft and others.
While the group was initially labeled a ransomware gang for its initial attacks on Brazil’s Ministry of Health, two South American telecommunication providers and others, its most recent attacks have involved exploiting public-facing Remote Desktop Protocol (RDP) protocols and phishing emails, according to Digital Shadows.
“The group started out targeting entities in South America but usually attackers that focus on this region tend not to expand. That being said, there is no better training to become an advanced attacker than to start out as a script kiddie,” Netenrich principal threat hunter John Bambenek told The Record.
“There are people who have run booter services or other low rent hacking groups who have gone on to do more sophisticated things. It looks like Lapsus$ is doing something similar.”
Jonathan Greig
is a Breaking News Reporter at Recorded Future News. Jonathan has worked across the globe as a journalist since 2014. Before moving back to New York City, he worked for news outlets in South Africa, Jordan and Cambodia. He previously covered cybersecurity at ZDNet and TechRepublic.



