Oakland officials say ransomware group may release personal data on Saturday
The government of Oakland acknowledged on Friday that the ransomware group responsible for the cyberattack on city systems is planning to publish the information it stole.
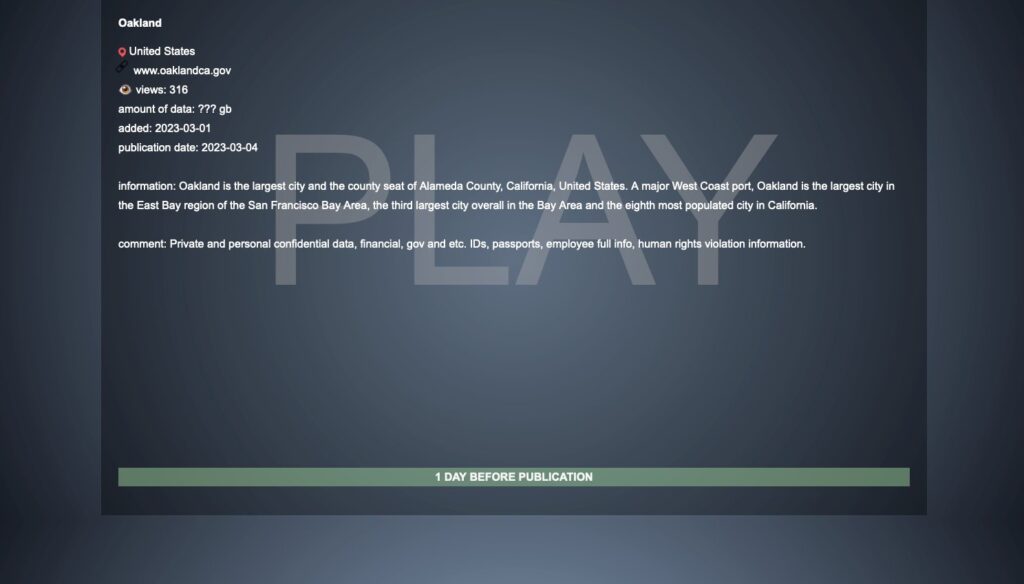
On Thursday evening, the Play ransomware group said it was behind the wide-ranging attack, writing on its leak site that it planned to publish sensitive stolen data on Saturday.
The group claims it took “private and personal confidential data, financial, gov, etc. IDs, passports, employee full info, human rights violation information.”
The City of Oakland did not respond to requests for comment about the post but released a statement on its website saying they are aware of the group’s threats.
“We are working with third-party specialists and law enforcement on this issue and are actively monitoring the unauthorized third party’s claims to investigate their validity. If we determine that any individual’s personal information is involved, we will notify those individuals in accordance with applicable law,” officials said.
“We will continue to work diligently to investigate and address this incident while working with our expert teams to enhance our security even more moving forward. We apologize for any disruptions this incident may have caused, and we thank our community for their continued support.”
Since February 10, city, state and federal officials have been dealing with the ramifications of a ransomware attack that brought down nearly all of the systems the city uses to serve its nearly 500,000 residents.
Following the state of emergency declaration issued last week, California Gov. Gavin Newsom agreed to send experts from the Office of Emergency Services alongside other civilian departments, as well as the National Guard, also known as the California Military Department.
It was only on Tuesday that the city was able to restore its 311 phone line, online permit center and city contract systems. Platforms for paying parking tickets and business taxes are still down.
Play ransomware emerging

The Play ransomware group first emerged in July 2022 targeting government entities in Latin America according to Trend Micro, which noted that some victims of this ransomware first surfaced in Bleeping Computer forums in June 2022.
Trend Micro researchers said Play ransomware actors use many tactics that follow the playbook of both the Nokoyawa Hive ransomware, including similarities in the file names and file paths of their respective tools and payloads.
The infrastructure used by the Hive ransomware group was disrupted by the FBI and other agencies in January.
The researchers also said they found evidence that “points to a possible connection between Play ransomware and Quantum ransomware, which is an offshoot of the notorious Conti ransomware group.”
Recorded Future ransomware expert Allan Liska said the ransomware group is relatively new but extremely active, accounting for about 6.5% of published victims based on data leak site victimology in 2023.
The group has taken credit for unconfirmed attacks on A10 networks, a public university in New York, Uruguay’s Ministry of Public Works and Transport as well as a government office in Nice, France.
The group’s most high-profile confirmed attacks targeted Arnold Clark, one of the United Kingdom’s largest car dealerships, the Belgian city of Antwerp and cloud computing giant Rackspace.
“They also don’t release full victim names on their extortion site, until it get close to time for the data dump, which is really unusual. So, for example when Oakland was first listed it was listed as O???a??” Liska said.
“In general, they appear to be relatively sophisticated and have managed to gain access to difficult targets, they should be a group to watch.”
Jonathan Greig
is a Breaking News Reporter at Recorded Future News. Jonathan has worked across the globe as a journalist since 2014. Before moving back to New York City, he worked for news outlets in South Africa, Jordan and Cambodia. He previously covered cybersecurity at ZDNet and TechRepublic.



