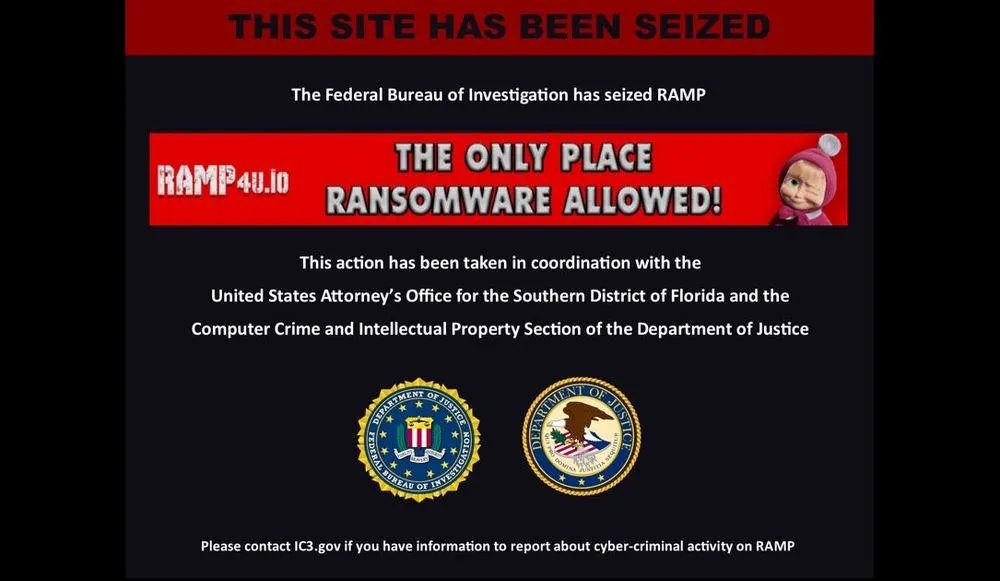
Notorious Russia-based RAMP cybercrime forum apparently seized by FBI
Websites for the RAMP cybercrime forum, a notorious Russian marketplace widely used by ransomware groups and initial access brokers, have been replaced with a splash page declaring they have been seized by the FBI.
The U.S. Department of Justice has not yet made a public statement about any actions targeting the Russian marketplace. Questions have been raised about the authenticity of the seizure. Back in 2024, the AlphV/BlackCat group claimed to have been shuttered by U.S. law enforcement in an elaborate exit scam intended to defraud its criminal affiliates.
Domain name server (DNS) records reportedly initially showed RAMP’s clearnet site redirecting to an FBI domain regularly used in takedowns.
The seizure notice does not feature the logos of any other international law enforcement agencies, as is typical for similar operations. It states: “This action has been taken in coordination with the United States Attorney’s Office for the Southern District of Florida and the Computer Crime and Intellectual Property Section of the Department of Justice.”
RAMP was used by Russian, Chinese and English-speaking cybercriminals and particularly catered to ransomware groups and their affiliates.
Among its administrators was a man called Mikhail Matveev, who was interviewed by Recorded Future’s Dmitry Smilyanets in 2022. At the time, Matveev said ownership of the forum would be transferred to a hacker known as Stallman.
In a post on the XSS hacking forum this week, Stallman announced that law enforcement had “taken control of the RAMP forum.”
“This event has destroyed years of my work creating the freest forum in the world, and although I hoped that this day would never come, deep down I always understood that it was possible. This is the risk we all take,” stated Stallman.
They added they would not be creating a new forum from scratch, but would continue to operate as a cybercriminal by purchasing access to the networks of potential victims.
One of many
Laura Galante, the former director of the cyberthreat intelligence integration center at the Office of the Director of National Intelligence (ODNI), told journalists in 2024 that disruption operations such as domain seizures were part of a strategy to reshape the cybercrime ecosystem.
“There is no one operation that’s going to disrupt ransomware permanently. Instead, we have to increase the frequency and increase the breadth of these operations by taking down infrastructure regularly, designating the exchanges that are facilitating money laundering and ransomware activity regularly,” she added.
Galante explained the intention was to prevent the emergence and success of a single, dominant group. The “disruption operations, especially the frequent cadence, does help keep any one group or any one specialization of toolsets from really holding on.”
This lack of market dominance “is one of the ways that this [the ransomware ecosystem] has remained decentralized,” said Galante.
“Disruption operations have been really key to making this harder for certain groups to really get deeper and more specialized and mature, and makes the organizations a little bit more chaotic, which ends up being helpful because it takes more time for them to reconstitute and have successful operations in the future.”
Alexander Martin
is the UK Editor for Recorded Future News. He was previously a technology reporter for Sky News and a fellow at the European Cyber Conflict Research Initiative, now Virtual Routes. He can be reached securely using Signal on: AlexanderMartin.79