North Korean hackers target employees of news outlets, software vendors and more through Chrome vulnerability
Google has released a report identifying two North Korean government hacking campaigns that exploited a Google Chrome 0-day.
Google Threat Analysis Group’s Adam Weidemann explained that on February 10, the company discovered two different North Korean campaigns – which they attributed to Operation Dream Job and Operation AppleJeus – exploiting CVE-2022-0609. Researchers have been aware of Operation Dream Job since at least August 2020 and Operation AppleJeus since at least 2018.
The vulnerability was highlighted and patched by Google in February but they noted that they were aware of reports that an exploit for it existed in the wild.
Weidemann said the earliest evidence they have of an exploit kit being actively deployed for the remote code execution vulnerability is January 4. The report focuses on the campaigns targeting US organizations but they note that other organizations and countries may have been targeted.
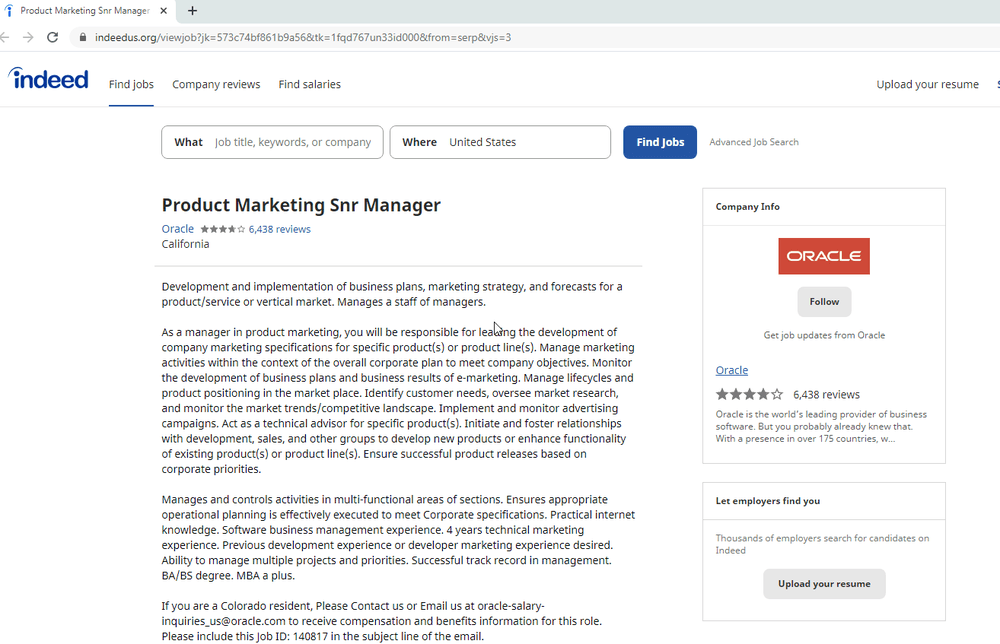
“The campaign, consistent with Operation Dream Job, targeted over 250 individuals working for 10 different news media, domain registrars, web hosting providers and software vendors. The targets received emails claiming to come from recruiters at Disney, Google and Oracle with fake potential job opportunities. The emails contained links spoofing legitimate job hunting websites like Indeed and ZipRecruiter,” Weidemann said.
“We suspect that these groups work for the same entity with a shared supply chain, hence the use of the same exploit kit, but each operate with a different mission set and deploy different techniques. It is possible that other North Korean government-backed attackers have access to the same exploit kit.”
For the Operation Dream Job campaign, anyone who clicked on the links sent in the email would be served a hidden iframe that would trigger the exploit kit, according to Weidemann.
The fake domains included disneycareers[.]net, find-dreamjob[.]com, indeedus[.]org, varietyjob[.]com, ziprecruiters[.]org. The exploitation URLs were https[:]//colasprint[.]com/about/about.asp and https[:]//varietyjob[.]com/sitemap/sitemap.asp.
The other campaign – Operation AppleJeus – involved the same exploit kit being used to target more than 85 users in the cryptocurrency and fintech industries.
“This included compromising at least two legitimate fintech company websites and hosting hidden iframes to serve the exploit kit to visitors. In other cases, we observed fake websites — already set up to distribute trojanized cryptocurrency applications — hosting iframes and pointing their visitors to the exploit kit,” Weidemann explained.
“The attackers made use of an exploit kit that contained multiple stages and components in order to exploit targeted users. The attackers placed links to the exploit kit within hidden iframes, which they embedded on both websites they owned as well as some websites they compromised.”
Weidemann noted that the kit first serves “heavily obfuscated javascript used to fingerprint the target system” before collecting data like the user-agent and sending it to the exploitation server.
Depending on whether an unknown set of requirements were met, the victim served a Chrome remote code execution exploit and some additional javascript, Weidemann explained.
“If the RCE was successful, the javascript would request the next stage referenced within the script as ‘SBX,’ a common acronym for Sandbox Escape. We unfortunately were unable to recover any of the stages that followed the initial RCE,” he said.
He added that the group managed to cover their tracks by only serving the iframe at specific times, using unique IDs to allow the exploit kit to only be served once, using Advanced Encryption Standard (AES) for each stage and not serving additional stages if previous ones failed.
Google also found evidence that the people behind the attack specifically checked for victims using Safari on MacOS or Firefox and directed them to specific links on known exploitation servers.
“The attackers made multiple attempts to use the exploit days after the vulnerability was patched on February 14, which stresses the importance of applying security updates as they become available,” Weidemann added.
Chainalysis, a company that tracks illegal blockchain transactions, said in January that hackers working for the North Korean government are believed to have stolen almost $400 million worth of cryptocurrency from seven hacked companies throughout 2021, up from the $300 million they stole from four companies in 2020.
Jonathan Greig
is a Breaking News Reporter at Recorded Future News. Jonathan has worked across the globe as a journalist since 2014. Before moving back to New York City, he worked for news outlets in South Africa, Jordan and Cambodia. He previously covered cybersecurity at ZDNet and TechRepublic.



