Nigeria-based group ‘Lilac Wolverine’ using COVID-19, emotional lures in BEC scams
A cybercrime group based in Nigeria is targeting businesses in the United States and Western Europe with a plethora of scam emails as part of a larger campaign of business email compromise (BEC) attacks.
Abnormal Security’s Crane Hassold told The Record that the group — named “Lilac Wolverine” — stood out to them among the thousands of BEC threat actors they see each week because of its significant volume.
“We consistently see 5-10 campaigns from them a day — and their unique combination of tactics — exploiting compromised personal accounts, setting up look-alike free webmail accounts, using emotionally-charged themes (cancer/COVID) – really stuck out as one of the more notable groups we track,” Hassold said.
“While we've seen Lilac Wolverine attacks target upwards of 50 enterprise users in a single campaign, the total number of targets is likely significantly higher since the group exploits a compromised personal accounts contact list.”

The group hides the targeted email addresses with blind carbon copy (BCC) when conducting their campaigns, making it impossible to know the exact number of targets.
Hassold noted that while it is difficult to know how successful their attacks are, the target population is substantially larger than in other types of attacks, meaning even a low success rate would get a good return-on-investment on their campaigns.
The actors are primarily based in Nigeria and most of the targets have been in the U.S. and countries in Western Europe, according to Abnormal Security research.
In May, the FBI said more than $43 billion has been lost through Business Email Compromise and Email Account Compromise scams since 2016.
BEC scams are popular attacks where hackers compromise legitimate business or personal email accounts through social engineering or computer intrusion before conducting unauthorized transfers of funds.
The FBI noted that there are now variations of the scam involving the theft of employees’ personally identifiable information, Wage and Tax Statement (W-2) forms or even cryptocurrency wallets.
Paul Abbate, deputy director of the FBI, said BEC crimes led to 19,954 complaints with an adjusted loss of nearly $2.4 billion in 2021 alone.
“The BEC scam has been reported in all 50 states and 177 countries, with over 140 countries receiving fraudulent transfers,” the FBI explained.
In a report released on Wednesday, Hassold said “Lilac Wolverine” was specifically using lures related to the pandemic and major illnesses to get people to open their scam emails.
They send out very large email campaigns targeting everyone on each compromised account’s contact list asking for help purchasing gift cards for a friend or relative.
Abnormal Security noted that the use of gift cards as a payment method in BEC attacks grew in popularity in 2017 and has now become the most common form of payment sought in attacks.
In typical BEC attacks, scammers have to target employees on a company’s finance team or a human resources department. But gift card attacks allow them to target any employee at the company regardless of department.
“Lilac Wolverine takes advantage of this broader target pool by launching some of the largest campaigns we see from any BEC threat group out there,” they said.
“Lilac Wolverine’s extremely high attack volume makes the group one of the most prolific we track today. Rather than sending messages directly from the accounts they compromise, Lilac Wolverine copies the accounts’ contacts to use in the next stage of their attack.”
Lilac Wolverine has specialized in vendor email compromise attacks, where they compromise the email account of a high-value employee at a vendor or supplier and leverage that account to target employees at other companies.
The group targets email accounts hosted on AOL, Yahoo, BellSouth, Verizon, and Rogers webmail services.
They even set up lookalike email accounts on other free webmail services, usually Gmail, Hotmail, Outlook to then send emails to the victim’s contact list.
The emails ask for favors or seem friendly and innocuous, asking how someone is or whether they’ve done any recent shopping on Amazon. Other emails include references to medical issues a person may have or COVID-19.
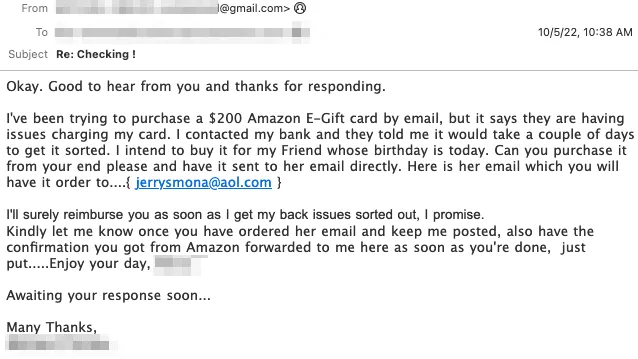
If someone responds, they shift to asking for payment, mostly by purchasing gift cards for a friend’s birthday. The emails typically contain reasons why the person cannot buy the gift cards themselves, either because they are traveling or because they having issues with their own credit cards.
Most emails include asks ranging from $100 to $500 from platforms like Amazon, Apple, and Google Play.
The FBI found that there were 116,401 BEC scams targeting U.S. citizens that were reported in complaints to the Internet Crime Complaint Center between October 2013 and December 2021 resulting in an exposed dollar loss of $14.76 billion.
The law enforcement agency got 5,260 complaints from non-U.S. victims that resulted in $1.27 billion in losses.
The FBI noted that there has been a 65% increase in identified global exposed losses between July 2019 and December 2021, attributing the stark increase to the COVID-19 pandemic.
In May, Interpol said the cybercrime unit of Nigeria’s national police arrested a 37-year-old Nigerian man suspected to be the leader of a BEC group known to cybersecurity researchers as SilverTerrier.
Jonathan Greig
is a Breaking News Reporter at Recorded Future News. Jonathan has worked across the globe as a journalist since 2014. Before moving back to New York City, he worked for news outlets in South Africa, Jordan and Cambodia. He previously covered cybersecurity at ZDNet and TechRepublic.



