New York OAG monitors hacking forums, notifies 17 companies of security breaches
The New York Office of the Attorney General said today that it notified 17 well-known online retailers, restaurant chains, and food delivery services that have been the victims of credential stuffing attacks.
New York Attorney General Letitia James said her office discovered the breaches after spendings months monitoring several online communities dedicated to credential stuffing.
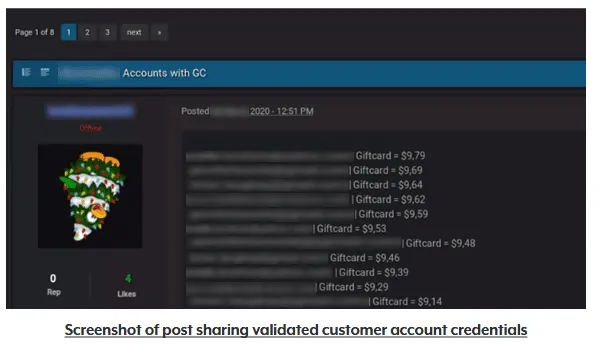
"The OAG found thousands of posts that contained customer login credentials that attackers had tested in a credential stuffing attack and confirmed could be used to access customer accounts at websites or on apps," James said in a press release today.
"In all, the OAG collected credentials for more than 1.1 million customer accounts, all of which appeared to have been compromised in credential stuffing attacks."
James said her office contacted the 17 companies whose customer accounts were hacked using credential stuffing, and all 17 took steps to notify and secure the compromised accounts.
"The OAG also worked with the companies to determine how attackers had circumvented existing safeguards and provided recommendations for strengthening their data security programs to better secure customer accounts in the future," James said.
A credential stuffing attack is when hackers take usernames and passwords leaked via data breaches at other companies and test them at other online services, hoping that users reused credentials across different sites.
Threat actors typically use credential stuffing attacks to gain access to user accounts at online services like email providers, gaming portals, social media, and online shopping sites primarily because these are the typical accounts that, when hacked, can be sold and monetized on cybercrime markets.
According to a Digital Shadows report, there are currently more than 15 billion credentials that leaked from various sources on the internet over the past decade, credentials that now serve as the base of most credential stuffing attacks.
In May 2021, Akamai said it saw more than 193 billion requests throughout 2020 that could be classified as credential stuffing attacks.
To help companies understand this phenomenon and set up basic defenses, the New York OAG has released today a 15-page PDF report with various security measures they could take to detect and block credential stuffing.
These recommendations include basic solutions such as setting up multi-factor authentication support for user accounts, the use of traffic monitoring solutions that can pick up spikes in failed login attempts, and basic user interface design tricks such as forcing users to re-authenticate before making any financial purchases. More recommendations are available in the report.
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.



