New Xenomorph malware sneaks onto the Google Play Store
There's a bottomless pool of threats facing Android users these days, and as soon as one Android malware operation sinks to the bottom, a new one rises to give users headaches.
Discovered and detailed in a report published today by security firm ThreatFabric, the latest of these threats is named Xenomorph.
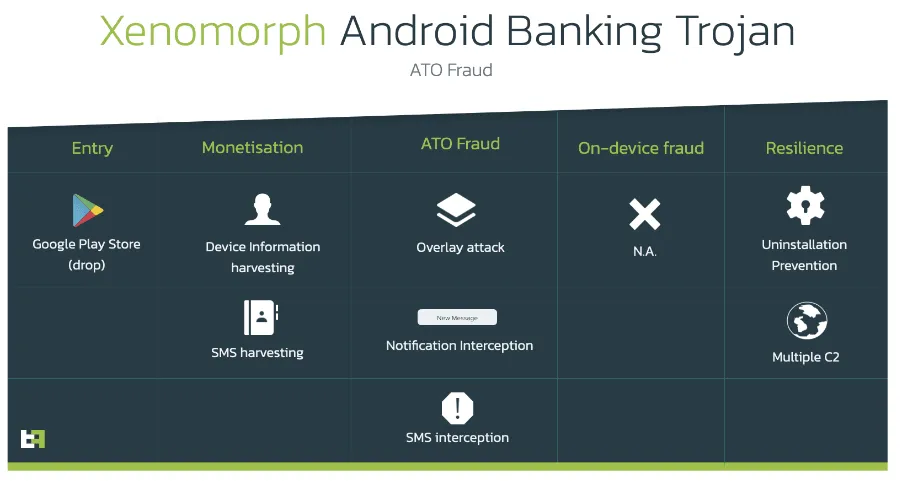
First spotted this month, the Xenomorph malware is a classic banking trojan that infects Android smartphones, requests access to the Accessibility service, and then uses this overpowered tool to show fake login screens on top of mobile banking applications.
The malware collects this info, along with other device data, and sends it to its owner's command and control (C&C) servers.
This data is later used to access bank accounts and steal funds. In case accounts are protected with two-factor authentication, Xenomorph can also intercept SMS message notifications and retrieve the code for the attackers.
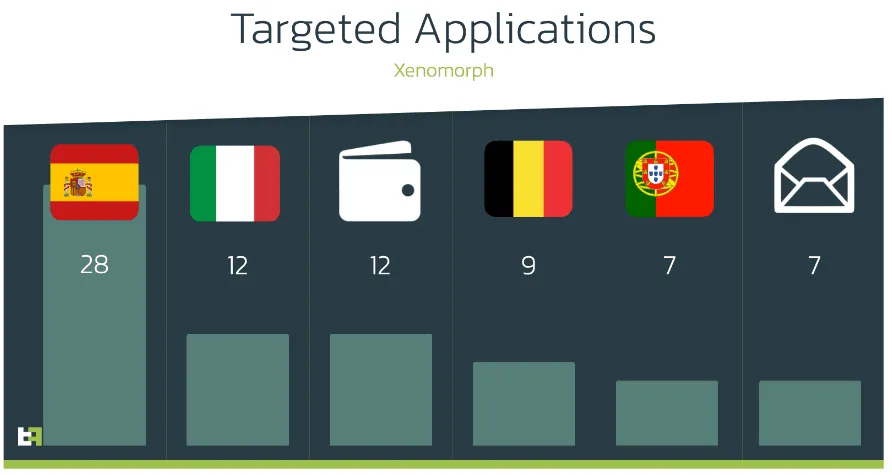
ThreatFabric said that based on the malware samples they found so far, Xenomorph could show fake login screens for 56 banks from Spain, Portugal, Italy, and Belgium.
In addition, it can also show fake login screens for 12 cryptocurrency mobile wallets and seven email apps.
But while many Android banking trojans today are being spread around using apps offered for download on third-party apps stores or via dedicated websites, Xenomorph is part of a select group of malware strains that have been distributed via the official Google Play Store.
The ThreatFabric team said Xenomorph is being offered as a second-stage payload inside malicious apps that have managed to sneak past Google's Play Store security checks.
These apps typically hide a small malware strain called a "dropper" that, once it gets past these checks, will download more potent and intrusive malware on a device.
In the attacks it spotted this month, ThreatFabric said it saw Xenomorph being dropped on users' devices via a dropper named Gymdrop.
For now, they've spotted Xenomorph infections only via the "Fast Cleaner" app, installed on more than 50,000 devices, before it was pulled from the Play Store.
While researchers said the malware still appears to be under development, it is clear that this is a new major threat that's here to stay, and they expect new attacks in the future.
ThreatFabric said it named the malware with the peculiar name of Xenomorph because it found clues in its code linking many of its features with an older Android banking trojan known as Alien and decided to go with a similar name inspired by the Alien movie series.
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.



