New TsuNAME bug can be used to DDoS key DNS servers
A team of security researchers has discovered a vulnerability in the domain name server (DNS) ecosystem that can be abused to amplify traffic heading to top-tier DNS nodes—known as DNS authoritative servers—and carry out a distributed denial of service (DDoS) attacks that could cripple or slow down these very important internet chokepoints.
The bug, disclosed today, was named tsuNAME.
It was discovered after operators of the New Zealand and the Dutch national domain registrars (.nz and .nl) spotted abnormalities in the DNS traffic hitting their authoritative servers.
How the tsuNAME bug works
But to understand how the TsuNAME bug works, it is important to distinguish the difference between authoritative and recursive domain name system (DNS) servers.
Most DNS servers available online today are recursive servers that take a user's DNS query and forward it to an authoritative DNS server, which works like a phone book and can return the DNS response for a specific domain name.
Under normal conditions, millions of recursive DNS servers send billions of DNS queries to authoritative DNS servers on a daily basis.
These authoritative DNS servers are usually housed and managed by large companies and organizations like content delivery networks, big tech giants, internet service providers, domain registrars, or government organizations.
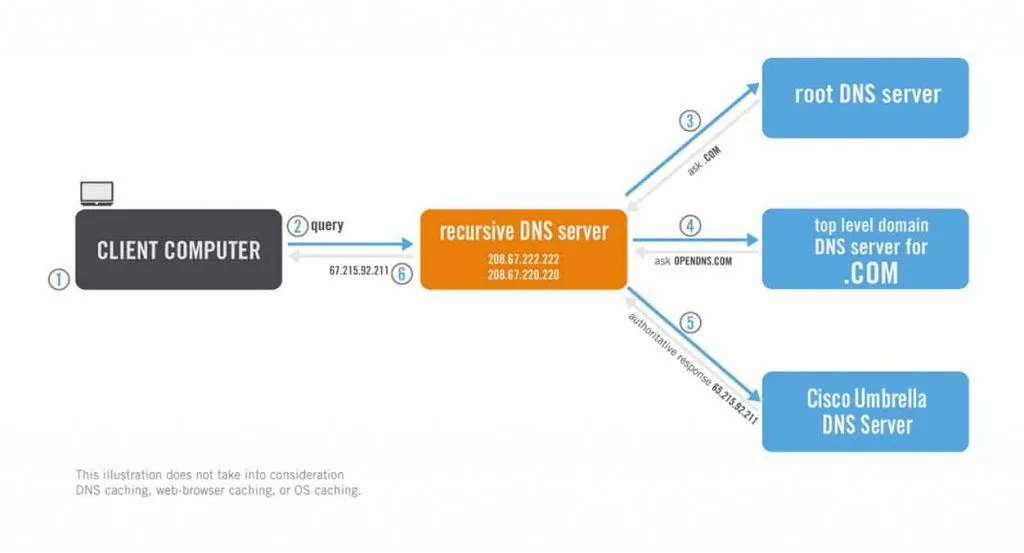
According to a research paper [PDF] published today, an attacker can craft malicious DNS queries that exploit bugs in recursive DNS software to send malformed queries in a non-stop loop to their authoritative DNS servers.
This attack, called tsuNAME, relies on both vulnerable recursive DNS software and misconfigurations at the authoritative DNS server, can be used to create traffic spikes at the upstream authoritative server. Researchers say that if a threat actor enrolls enough recursive DNS servers in their attack, they can create sufficiently large DDoS attacks that take down key internet nodes.
"We found some DNS resolvers software start to loop when the encounter domain names that are misconfigured with cyclically dependent NS records. [It] is this loop that can be used against authoritative servers," researchers said today on a website dedicated to their finding.
Mitigations available
The research team, which besides representatives from InternetNZ and SIDN Labs, also included academics from the University of Southern California, have released today a tool called CycleHunter that can be used by the operators of authoritative DNS servers to find cyclic dependencies in their DNS zone files.
Eliminating these cyclic dependencies prevents attackers from exploiting tsuNAME for DDoS attacks, even if the recursive DNS software has yet to receive patches.
Currently, researchers said they notified Google and Cisco, whose Google Public DNS (GDNS) and OpenDNS services were abused against the attacks that downed the .nz and .nl registrars last year.
Efforts are still underway to identify vulnerable DNS resolver software, but tools such as Unbound, BIND, and KnotDNS have already been ruled out as unaffected by tsuNAME exploitation.
"We thank both Google and Cisco for fixing that vulnerability, given they are among the largest DNS services on the Internet. However, there are many other resolvers that may be vulnerable to tsuNAME," researchers said.
For the time being, tsuNAME appears to be a bug that manifested by accident, and no malicious or intentional attacks have been registered so far, although, this might change in the future.
Academics said they used CycleHunter to evaluate roughly 184 million domain names in seven top-level domains (TLDs) and found 44 cyclic dependent NS records (likely from configuration errors) used by around 1,400 domain names that could be abused for future attacks.
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.