New Side-Channel Attack Targets the CPU Ring Bus for the First Time
In a paper published today, a team of academics from the University of Illinois at Urbana-Champaign have published details about a new side-channel attack against the internal architecture of modern CPUs.
Side-channel attacks take place when attackers are able to observe how a system operates —in this case, a computer processor—, and then infer what data the system is processing based on small variations in its parameters.
Side-channel attacks targeting modern CPUs have been disclosed on a yearly basis for the past two decades. Academics and security researchers have analyzed various parts of a processor's architecture and have looked for leaks that they could exploit to extract data that was being processed inside the CPU.
Past attacks have looked at CPU temperatures, fan noises, transfer errors, and —in the vast majority of previously published papers— the CPU's internal cache architecture.
First side-channel attack looking at the CPU bus
But in a research paper published tonight and titled "Lord of the Ring(s): Side Channel Attacks on the CPU On-Chip Ring Interconnect Are Practical," UIUC researchers looked at a part of modern multi-core CPUs that hasn't been analyzed before —namely, the ring interconnect.
Also known as the ring bus, this is essentially what its name says it is; a physical circuit in the form of a ring that connects all CPU cores and CPU components, allowing for coordination and data transfer between cores and other CPU elements.
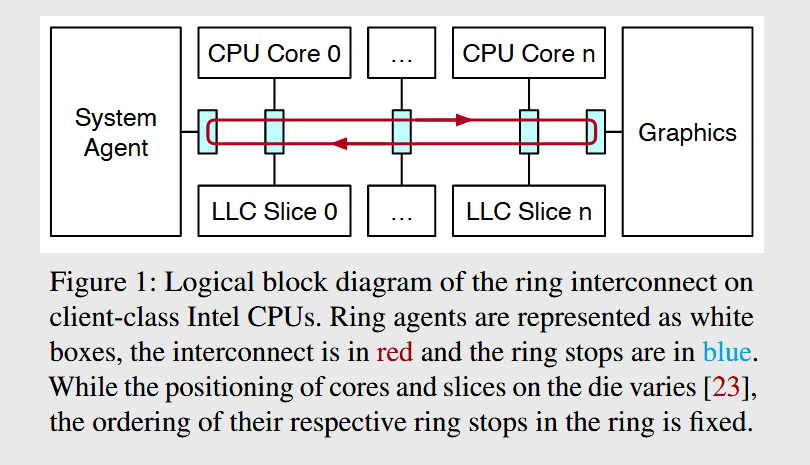
Also, see the video below for a basic explainer on the ring interconnect.
The CPU ring bus has never been analyzed for side-channel leaks before, primarily because it's been scantly documented before.
The UIUC team said that part of their research, they performed a "thorough reverse engineering of the sophisticated protocols that handle communication on the ring interconnect," and found that they could create contention between operations on the CPU ring bus, behaviors that they could later study and abuse for side-channel leakages.
In practical tests, researchers said they were able to extract "key bits from vulnerable EdDSA and RSA implementations," but also infer "precise timing of keystrokes typed by a victim user."
Intel CPUs are vulnerable
Practical tests were performed on Intel Coffee Lake and Skylake CPUs, but the attack should theoretically work on any Intel CPU with a ring bus.
The attack was not tested on AMD CPUs since they used a different proprietary technology (named Infinity Fabric) to interconnect processor cores.
Also not vulnerable are recent models of Intel server and high-grade processing (HCP) processors, which, due to the very large number of cores, have switched from a ring bus to a mesh interconnect.
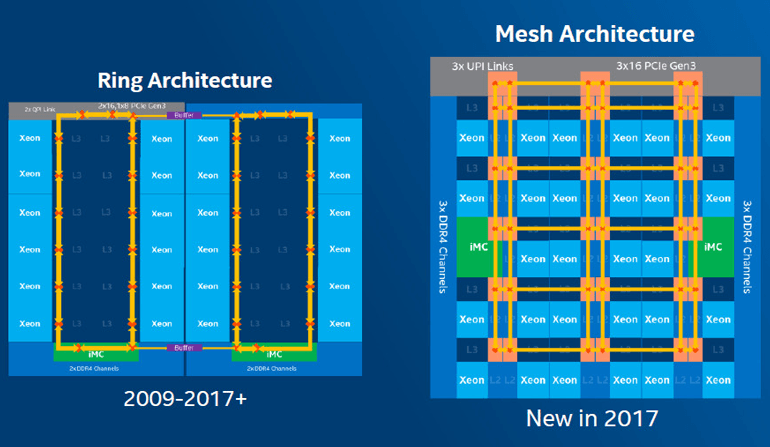
However, researchers said that "the techniques we [used] to build our contention model can be applied on these platforms too," a task they'll leave for future research on the topic.
Intel's response
But despite the novelty of this attack, Intel played down the issue.
"Intel classified our attack as a 'traditional side channel' (like TLBleed, Portsmash, etc.), and they treat this class of attacks differently than the class of 'speculative execution / transient execution attacks' (like Spectre, Meltdown, etc.)," Riccardo Paccagnella, one of the researchers, told The Record.
"That is, they do not officially consider traditional side channel attacks as significant value for an attacker and they already published guidance on how to mitigate them in software here and here."
However, the recommended defenses require that developers follow constant-time programming principles when writing their code.
"Truly constant-time code may be difficult to implement in practice," Paccagnella told The Record.
The research team's paper will be available for download later today, and its findings will also be presented in August at the USENIX Security conference.
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.