New Qlocker ransomware is hitting hundreds of QNAP NAS devices per day
A new ransomware strain named Qlocker is on a rampage and infecting hundreds of QNAP network-attached storage (NAS) devices every day, taking over hard drives, moving users' files inside password-protected 7zip archives, and asking for a $550 ransom payment.
The first cases were reported on Tuesday, April 20, and the number of infections has skyrocketed into the hundreds per day, according to statistics provided by Michael Gillespie, the creator of ransomware identification service ID-Ransomware.
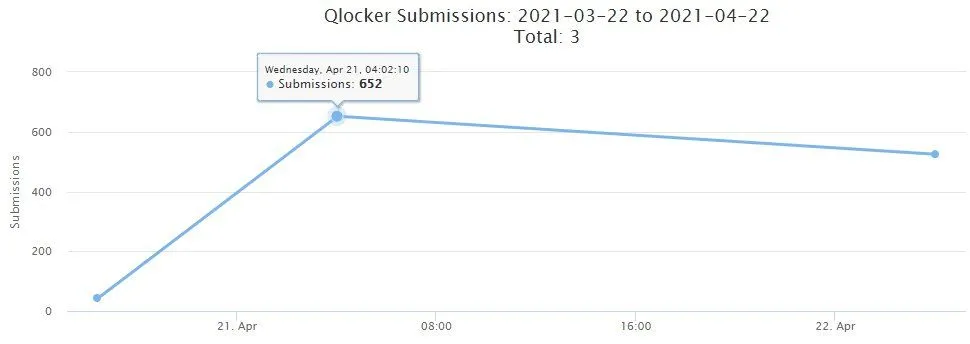
In a security advisory published on its website today, QNAP told customers to apply recent updates for three apps to secure their devices from ransomware attacks.
During the past few days, QNAP patched an SQL injection bug in the Multimedia Console and Media Streaming Add-on and also removed hardcoded credentials from the Hybrid Backup Sync app.
The Taiwanese hardware vendor did not say which of the three apps the Qlocker gang is abusing to gain access to unpatched devices.
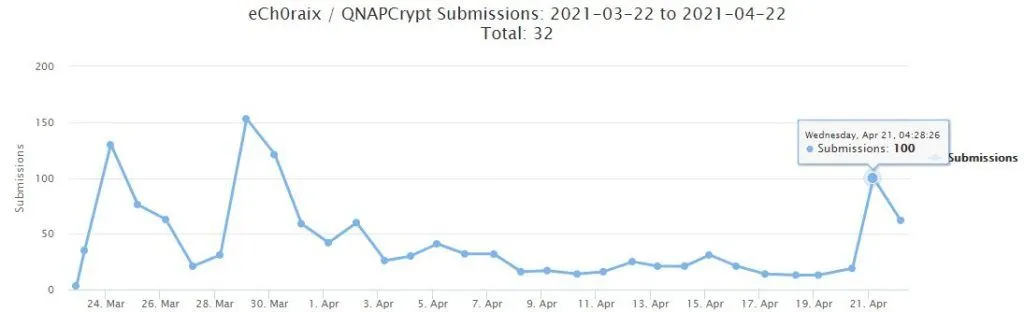
Ech0raix attacks also spiked
QNAP told users to apply updates for these apps to prevent ransomware attacks not only from the Qlocker gang but also from eCh0raix, an older ransomware operation focused on infecting QNAP systems, which has been lurking and scouring the internet for unpatched QNAP devices since last year.
While the eCh0raix gang is not currently infecting hundreds of systems per day at the same pace as Qlocker, Gillespie told The Record that the operation had also seen a spike in recent days, suggesting they might have found and weaponized the same bugs as the Qlocker gang.
Owners of QNAP devices are advised to update the apps that run on top of their NAS firmware as soon as possible. Those who don't want to take unnecessary risks are advised to take systems offline until the Qlocker attacks subside and QNAP formally confirms the ransomware intrusion vector and that patches are indeed successful in stopping attacks.
For the techies out there, a technical analysis of the Qlocker ransomware is available on Bleeping Computer; a site focused on tracking ransomware strains.
At the time of writing, there is no way of recovering the Qlocker 7zip password and decrypting files without paying.
A security researcher found a way to bypass Qlocker's ransom payment verification routine, but the Qlocker operators caught on to the trick and fixed their code within an hour. Luckily, the researcher was able to help around 50 victims recover their files for free, sparing them from paying more than $27,000 to the attackers.
Update: it looks like this may have been fixed by the ransomware operators, unfortunately. I apologize if I was not able to get to yours before it was fixed. In total decrypted around 50 keys worth $27k.
— Jack Cable (@jackhcable) April 22, 2021
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.



