New Iranian threat actor targets Israel with wipers disguised as ransomware
Cyber-security firm SentinelOne said in a report published today that it discovered a new threat actor operating out of Iran and which heavily relied on data-wiping malware to destroy its targets' IT infrastructure, and then ask for ransoms in an attempt to mask their attacks as ransomware extortions.
Named Agrius, the threat actor has been active since early 2020, and while initial attacks were aimed at targets in the Middle East region, since December 2020, the group has re-focused operations on Israel.
Agrius creates a new data wiper... erm... ransomware
For initial attacks, SentinelOne said Agrius used a data-wiping malware named DEADWOOD (aka Detbosit), a tool that has also been used by other Iranian threat actors in past attacks.
To install DEADWOOD, the group often used vulnerabilities in unpatched servers to gain a foothold on a target's network, which they used to deploy the ASPXSpy web shell, and then the IPSec Helper backdoor.
Once a target's network was ready and fully compromised, the Agrius group would deploy DEADWOOD, destroy MBR partitions and wipe files, and then ask for a ransom payment to distract the victim's IT teams from the real purpose of their attacks.
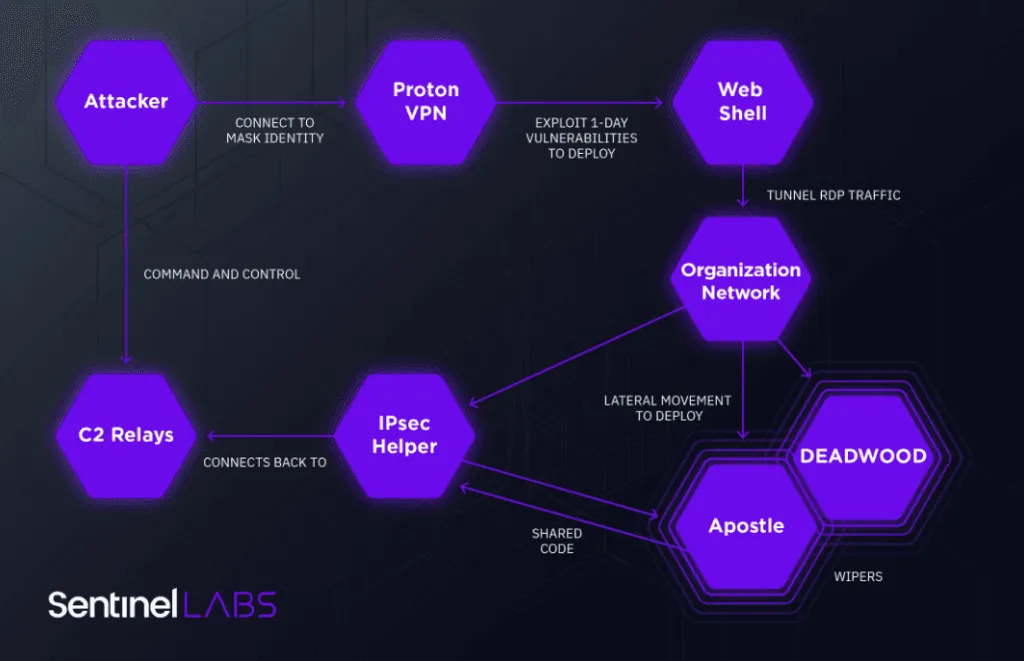
However, fearing that Deadwood would get detected since it was a known malware strain, the group also created a new tool towards the end of the year.
Named Apostle, this malware strain appears to have been developed in November 2020, but SentinelOne researchers said its initial version often failed to destroy files, forcing the group to go back to DEADWOOD to finish their intrusions.
"This early version was deployed in an attempt to wipe data but failed to do so possibly due to a logic flaw in the malware," said Amitai Ben Shushan Ehrlich, malware analyst at SentinelOne, in a report published today.
But during subsequent attacks, Ehrlich said he discovered a second version of the Apostle data wiper, which not only fixed its logic bugs that prevented the malware from wiping files but also added a file-encryption routine, turning Apostle into fully functional ransomware.
However, despite the presence of a functional file encryption routine, SentinelOne assessed the purpose of Agrius attacks was still to cripple operations rather than extort companies.
"We find it unlikely that Agrius is a financially motivated threat actor," Ehrlich said.
A strong focus on Israel
But most importantly, the SentinelOne researcher also points out that the group's sudden re-focus on Israel is significant and confirms a broader picture of escalating tensions in cyberspace between the Tel Aviv and Tehran governments.
"Our analysis of Agrius activity does not come in a vacuum," Ehrlich said.
The Agrius data-wiping/ransomware intrusions come after another Iranian threat actor used the Pay2Key ransomware to target Israel in 2020 and 2021, attacks that were then followed by another Iranian threat actor operating the n3tw0rm ransomware, which also heavily targeted Israel.
"The close proximity of the Agrius and n3tw0rm campaigns suggest they may be part of a larger, coordinated Iranian strategy," Ehrlich said. "Leaks from Lab Dookhtegan and the Project Signal ransomware operation also support this claim."
The fact that threat actors with a nexus to the Iranian government are carrying out data-wiping attacks in Israel, while shocking, it is not a surprise. Iranian-linked hacking groups have a long history of deploying data wipers and hiding data-wiping attacks as ransomware. Previous cases include the Shamoon, ZeroCleare, and Dustman malware.
Indicators of compromise (IOCs) and technical details are available in this technical report [PDF]. CERT Israel is also expected to release more details about the attacks later today.
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.



