New hacking group targets Pakistan's Navy and maritime industry
A previously unknown hacking group is using espionage tools to target Pakistan's Navy, according to new research.
Dmitry Bestuzhev, a threat Researcher at BlackBerry, told The Record that the group – which they named “NewsPenguin” – is a targeted attack group focused on militaries and the defense industry.
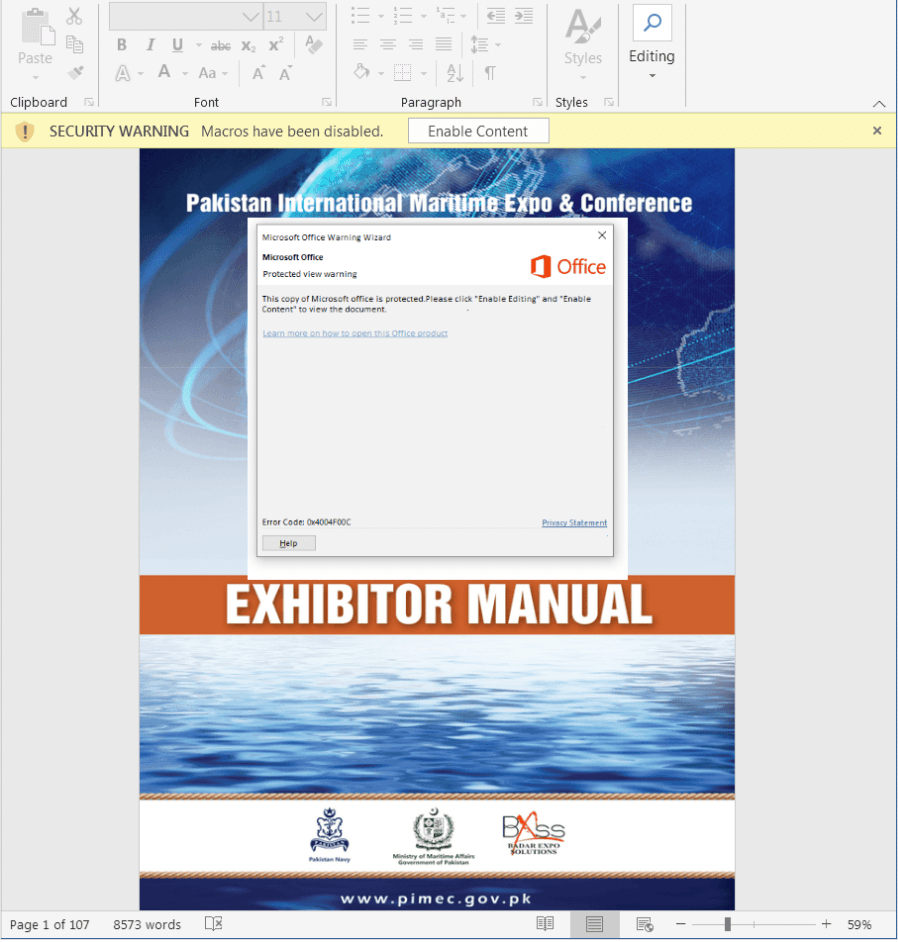
The group used the upcoming Pakistan International Maritime Expo & Conference (PIMEC-2023) as a lure to trick victims into opening phishing emails containing malware.
“The whole campaign is about cyber espionage. We discovered NewsPenguin about a month ago. We realized that based on the lure document, the nature of the target, and the code analysis, that this is a cyber espionage campaign with no financial motivation,” he said. “It appears the objective of this operation is to spy on the attendees of the conference... and its organizers.”
One aspect of the campaign that stood out to Bestuzhev was the use of network infrastructure that would only deploy parts of the malware on victim devices that had a Pakistani IP address. The feature – alongside several others – is designed to keep samples of the espionage tool out of the hands of researchers, Bestuzhev said. The malware has other novel features that allow it to bypass whitelisting – where only approved applications are allowed to run on a device – by attaching itself to legitimate components.
In a report on the malware, BlackBerry researchers said they were unable to attribute the campaign to a specific country or agency, but noted that the tool is “utilizing advanced planning and continuous improvement of infiltration tools – including the allusion to ‘fake’ news sites to imbue validity into the phishing attempts.”
The attackers sent targeted phishing emails with malicious documents purporting to be exhibitor manuals for PIMEC-2023. The researchers called the group “NewsPenguin” because of unique encryption keys and other headers that use the words “penguin” and “getlatestnews.”
PIMEC, which runs from February 10 to February 12, is organized under Pakistan's Ministry of Maritime Affairs and showcases products from the public and private sectors.
The researchers found several technical features of the campaign that show the group has done advanced planning and background hacking for a while ahead of the phishing emails.
The emails were sent to multiple Pakistani marine-related entities and likely visitors to the conference.
BlackBerry researchers said one of the domains owned by the hackers was registered on June 30, 2022 – indicating the attack has likely been in the works since then.
“Given that the final payload includes a Trojan that conducts spy activities – as well as collecting and transmitting confidential information to the threat actors – we can assume the attacker will also be planning to exfiltrate data,” the researchers said.
The Pakistani military and navy did not respond to requests for comment.
Several reports over the last two years show Pakistani government entities have been a frequent target of Chinese state-backed actors.
Last year Volexity and Recorded Future – which owns The Record – identified a campaign by a Chinese APT group targeting organizations and governments in Pakistan through a zero-day vulnerability in Sophos Firewall.
Another cybersecurity firm, SentinelOne, discovered Chinese government espionage attacks on Pakistani telecommunications companies and the Pakistan Telecommunication Authority through a potentially compromised account in the Cabinet Division of the Pakistani government.
Jonathan Greig
is a Breaking News Reporter at Recorded Future News. Jonathan has worked across the globe as a journalist since 2014. Before moving back to New York City, he worked for news outlets in South Africa, Jordan and Cambodia. He previously covered cybersecurity at ZDNet and TechRepublic.



