New 'DragonForce' hacktivist group causes havoc in Israel
After Israeli government officials announced in early June that they were ready to establish diplomatic ties with Southeast Asia's Muslim-majority nations, a hacktivist group named DragonForce Malaysia led a series of cyberattacks against Israeli targets throughout the month of June and July.
Operating from a forum on the public internet that hosts more than 4,000 discussion threads for more than 10,000 registered users, DragonForce members orchestrated and carried out website defacements, data leaks, and DDoS attacks.
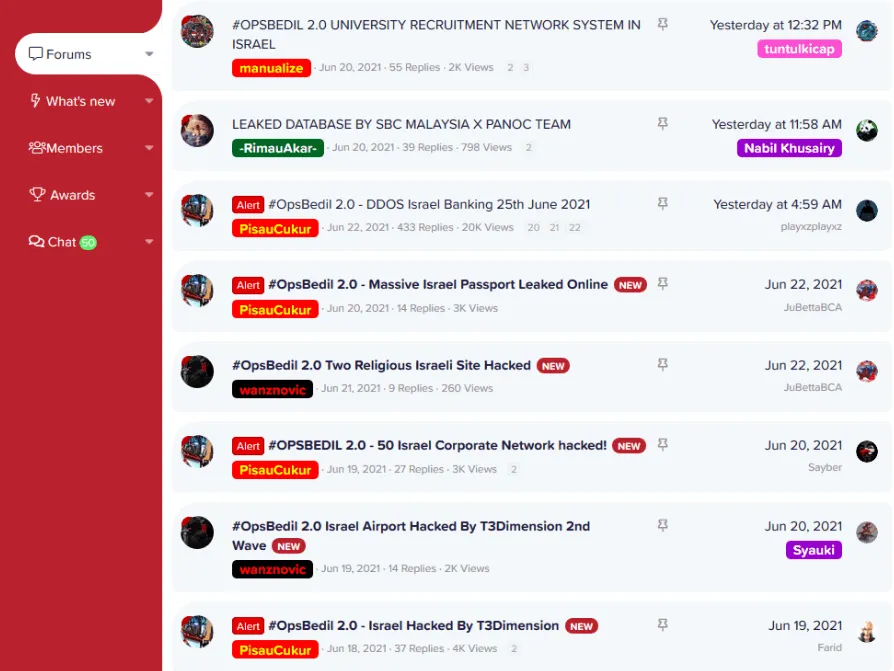
Some attacks they carried out on their own, but DragonForce also worked with other hacktivist gangs and even ran social media campaigns encouraging others to join, security firm Radware said in a report published today.
Hacktivist groups that joined DragonForce's calls included T3 Dimention Team, Syntax Brute Code (SBC) Malaysia, and the PANOC Team, mostly for a series of attacks tracked under the hashtag of #OpsBedil.
Radware said it tracked, linked, and verified DragonForce's involvement in attacks such as:
- The defacement of AcadeME, an Israeli website dedicated to helping students sign up for universities.
- The leak of the personal data of more than 280,000 AcadeME users.
- A campaign aimed at DDoSing the Israeli banking sector.
- The leak of Israeli passport data.
- The hacking of at least two Israeli religious sites.
- The leak of VPN credentials for at least 50 Israeli companies.
- The defacement of websites for the Ramon Airport and other airline-related organizations.
Radware said that most of the attacks were carried out with public and low-sophisticated tools.
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.



