New Cring ransomware deployed via unpatched Fortinet VPNs
Unpatched Fortinet VPN devices are being hacked to deploy a new strain of ransomware inside corporate networks, Russian security firm Kaspersky said today.
"Victims of these attacks include industrial enterprises in European countries," Kaspersky senior security researcher Vyacheslav Kopeytsev said in a report today.
"At least in one case, an attack of the ransomware resulted in a temporary shutdown of the industrial process due to servers used to control the industrial process becoming encrypted," Kopeytsev said, but without revealing the victim's name.
New Cring ransomware
All these attacks happened in Q1 2020, and they were carried out with a new strain of ransomware named Cring (other aliases include Vjiszy1lo, Ghost, Phantom) that was first discovered in January 2021.
CRING a new strain deployed by human operated ransomware actors. After the actors have established initial access, they drop a customized Mimikatz sample followed by #CobaltStrike. The #CRING #ransomware is then downloaded via certutill. ^mikehttps://t.co/v5h8eqHCPt pic.twitter.com/fkU2USEZis— Swisscom CSIRT (@swisscom_csirt) January 26, 2021
While the ransomware was initially spotted by the security team of Swiss internet service provider Swisscom, very few details were available at the time.
The Kaspersky report published today sheds some light on how these attacks take place, and, according to Kopeytsev, Cring is the latest "human-operated ransomware strain."
What this means is that infections with Cring usually happen after attackers orchestrate intrusions into corporate networks, expand their access to as many systems as possible, and only then run the ransomware during a hands-on-keyboard intrusion.
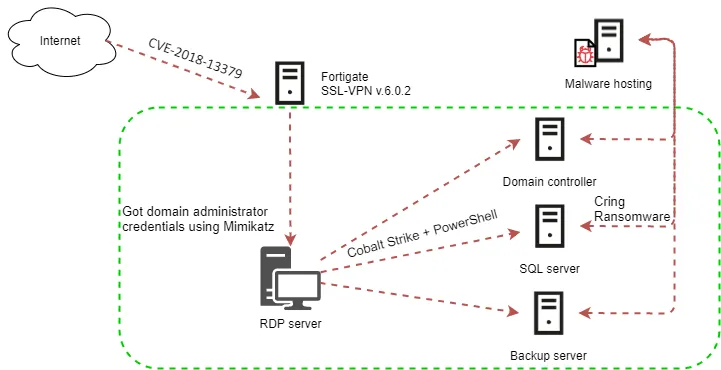
In Cring's case, the initial intrusion vector appears to be Fortinet devices that haven't been patched for the CVE-2018-13379 vulnerability.
According to Kaspersky, the intruders used exploits for this bug to access the VPN device, after which they used the Mimikatz open-source tool to dump credentials of Windows users who had previously logged in to the compromised VPN.
The attackers then used the credentials to connect to internal workstations on the victim's internal network, where they used PowerShell scripts and the Cobalt Strike intrusion simulation framework to escalate access to even more internal systems, after which, as a last step, downloaded the Cring ransomware on each system, and proceeded to encrypt local files.
Fortinet VPNs under heavy assault for two years now
But despite the severity of the Cring ransomware attacks reported today by Kaspersky, these intrusions are not surprising to most security professionals.
Ever since the disclosure of the CVE-2018-13379 vulnerability in the summer of 2019, Fortinet devices have been heavily targeted by attackers.
Past attacks included Chinese and Iranian state-sponsored threat actors but also regular cybercrime groups like initial access brokers and ransomware gangs.
Fortinet, together with Pulse Secure and Citrix systems, have been the most heavily abused systems over the past two years and a common entry point for all sorts of attackers, not just ransomware gangs.
Even if the Fortinet vulnerability exploited in these intrusions is two years old now, attacks have continued to this day.
Just last week, the Federal Bureau of Investigation (FBI) and the Cybersecurity and Infrastructure Security Agency (CISA) issued a joint security advisory warning that threat actors are continuing to exploit Fortinet vulnerabilities to gain initial access to government and corporate networks which they plan to attack in future intrusions.
For security professionals and system administrators, the Kaspersky report contains a step-by-step walkthrough of a Cring ransomware attack, along with indicators of compromise that companies would want to detect and block.
Image via Johannes Weber, CC BY 2.0
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.



