New Android malware records smartphones via VNC to steal passwords
Security researchers have discovered a novel piece of Android malware that uses the VNC technology to record and broadcast a victim's smartphone activity, allowing threat actors to collect keyboard presses and app passwords.
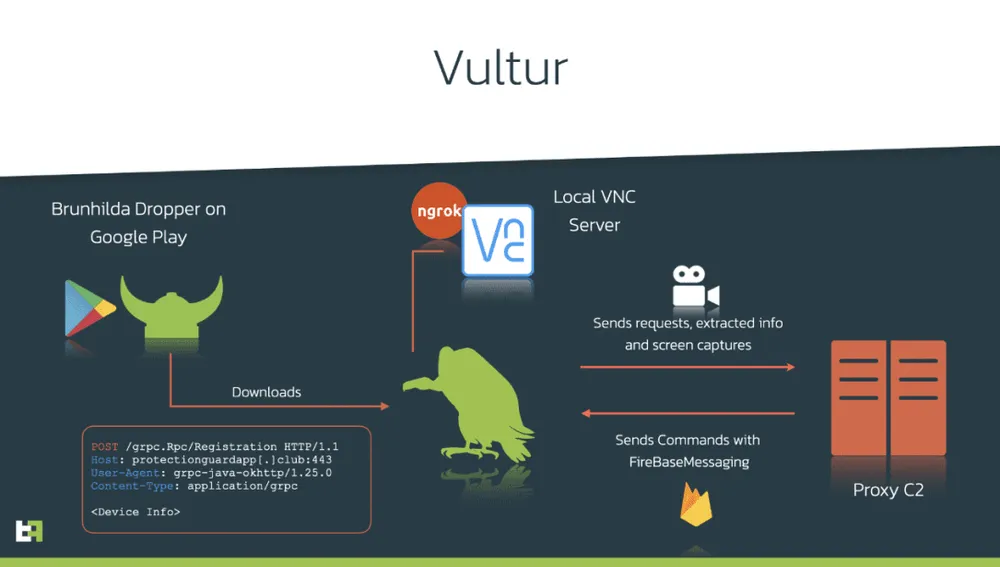
First spotted in March 2021 by Dutch security firm ThreatFabric, this new piece of malware, named Vultur, is a departure from other Android malware strains that usually rely on fake login screens floating on top of legitimate apps to collect a victim's credentials.
Instead, Vultur opens a VNC server on the infected phone, and broadcasts screen captures to an attacker command and control server, where the Vultur operator extracts passwords for desired apps.
Below is a summary of Vultur features as detailed in a ThreatFabric report shared with The Record this week:
- Although it is advertised as a banking trojan, Vultur is part of a recent trend where Android banking trojans also come with features typical to remote access trojans (RATs), allowing attackers full control over a device.
- Vultur is currently installed on devices that have been previously infected with the Brunhilda malware [PDF], known to sometimes reached the Google Play Store and serve as a "dropper" for other malware strains.
- Vultur is successful in taking full control over a device only if it manages to trick users into granting access to the Accessibility permission.
- Vultur automatically presses the "Back" button whenever users navigate to the screen where they would uninstall its parent app.
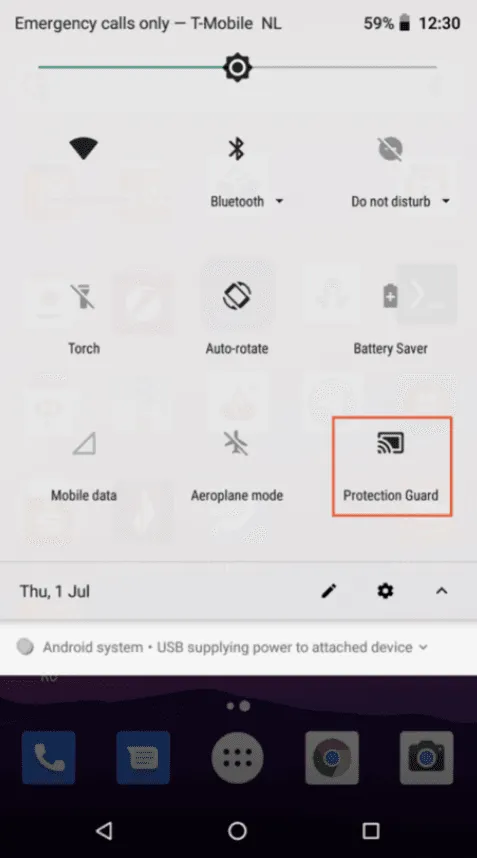
- Users can spot Vultur in operation because every time it broadcasts the victim's screen, the "Protection Guard" indicator lights up in the Android notification panel.
- Besides collecting key presses via VNC, Vultur can also send a list of installed apps to the malware operator in order to decide if the victim is a valuable asset.
- ThreatFabric estimated that Vultur has infected between 5,000 and 8,000 users so far.
- Per the malware's configuration, it currently targets mobile banking apps for banks in Italy, Australia, Spain, the Netherlands, and the UK.
- It can also target and steal credentials for cryptocurrency mobile wallets and social media apps.
- ThreatFabric said that a code-level investigation unearthed similarities and possible connections to the Brunhilda developers.
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.