Experts warn of MOVEit Transfer tool exploitation using zero-day bug
Hackers are exploiting a new zero-day vulnerability affecting a popular file transfer tool used by thousands of major companies.
BleepingComputer was first to report that hackers were exploiting the vulnerability affecting MOVEit software, and security company Rapid7 said it is also seeing exploitation of the bug “across multiple customer environments.”
The tool was created by Progress Software, which published an advisory about the issue on Wednesday.
“Progress has discovered a vulnerability in MOVEit Transfer that could lead to escalated privileges and potential unauthorized access to the environment. If you are a MOVEit Transfer customer, it is extremely important that you take immediate action as noted below in order to help protect your MOVEit Transfer environment, while our team produces a patch,” the company said.
The company urged customers to disable all HTTP and HTTPs traffic to their MOVEit Transfer environment. They also said customers should be on the lookout for unexpected and large file downloads or the creation of unexpected files in certain folders on all of their MOVEit Transfer instances, including back-ups.
The company said patches for the bug are being tested right now and will be released as soon as possible.
In a statement provided to Recorded Future News, a spokesperson from the company said: "When we identified the issue, we took immediate action, including bringing down MOVEit Cloud, to ensure the safety of our customers, while we reviewed the severity of the situation. We also notified our customers, first providing instructions for immediate actions, followed by the release of a patch."
Rapid7 Senior Manager of Vulnerability Research Caitlin Condon said as of May 31 there were roughly 2,500 instances of MOVEit Transfer exposed to the public internet, the majority appearing to be in the United States. Cybersecurity researcher Kevin Beaumont shared images of at least one instance connected to the U.S. Department of Homeland Security.
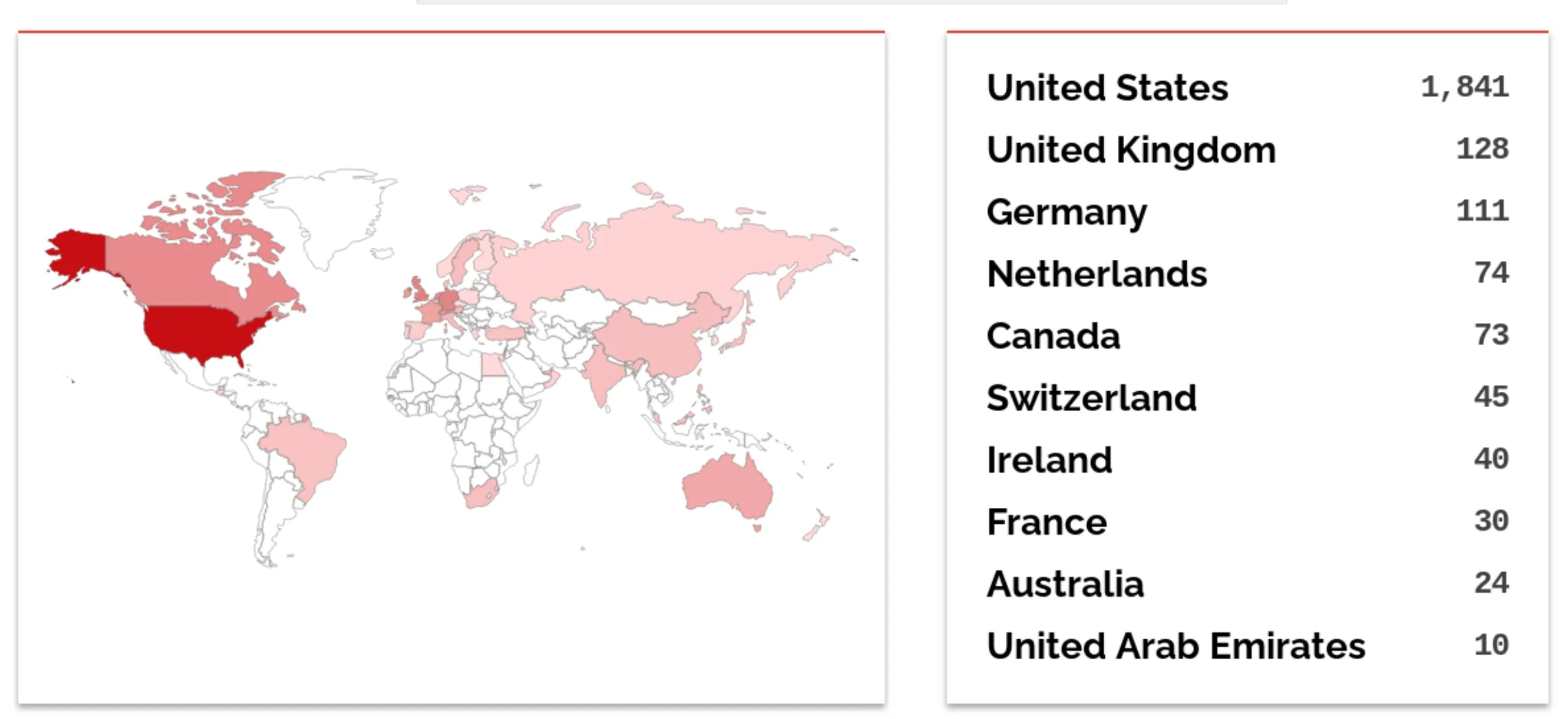
“Huge US footprint, including US government. It's quite expensive, so mostly western enterprises,” Beaumont wrote in posts on the Mastodon social media site.
“Every one online is still vulnerable. This includes some big banks etc. - Webshells started being planted a few weeks ago, multiple incidents running at multiple orgs during that timeframe who detected activity.”
Condon explained that there is evidence that hackers have already automated exploitation of the issue, and BleepingComputer reported that hackers have already begun to mass download data from affected companies.
The attack on MOVEit would be the latest involving a popular file transfer tool used by large organizations this year. In February, ransomware groups exploited a vulnerability affecting Fortra’s GoAnywhere MFT file-transfer product.
The governments of Toronto and Tasmania were affected by the incident alongside corporate giants like Proctor & Gamble, Virgin and Hitachi.
The ransomware group behind the exploitation – the Cl0p gang – was previously behind another widespread attack on another file transfer tool in 2021.
The gang targeted the Accellion file transfer tool to steal data from some of the biggest companies and schools in the world, including the University of Colorado, Kroger, Morgan Stanley and Shell.
Updated at 2:17pm to include a statement from Progress Software.
Jonathan Greig
is a Breaking News Reporter at Recorded Future News. Jonathan has worked across the globe as a journalist since 2014. Before moving back to New York City, he worked for news outlets in South Africa, Jordan and Cambodia. He previously covered cybersecurity at ZDNet and TechRepublic.



