Most attackers lose interest in Log4Shell
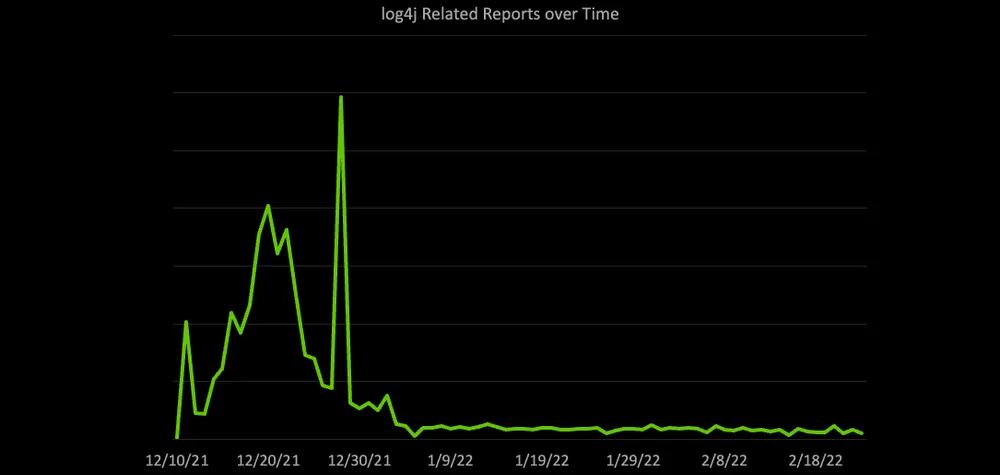
After all the hype in December last year, threat actors appear to have lost interest in exploiting the Log4Shell vulnerability, as both Sophos and the SANS Internet Storm Center are reporting dwindling numbers this year.
Tracked as CVE-2021-44228, the vulnerability is more commonly known as Log4Shell. It is a security flaw in Apache Log4j, a small library that is used to add logging capabilities to Java-coded projects.
Details about the Log4Shell vulnerability were disclosed last December and got almost everyone's attention because of the library's huge userbase and the simple one-line exploit.
"Our sensors detected exploit attempts almost immediately," Johannes Ullrich, ICS SANS fellow, said in a report this week.
Initially, Log4Shell scanning saw a huge spike in activity as threat actors began searching the internet for Java apps that might have used the Log4j library and were testing the exploit to see what was vulnerable.
But these spikes in attacks only lasted around three weeks; until the end of 2021.
"Over time, attackers and researchers lost interest in Log4j," Ullrich said.
Log4Shell exploitation numbers published by UK security firm Sophos at the end of January also confirm the downward trend and eventual plateau.
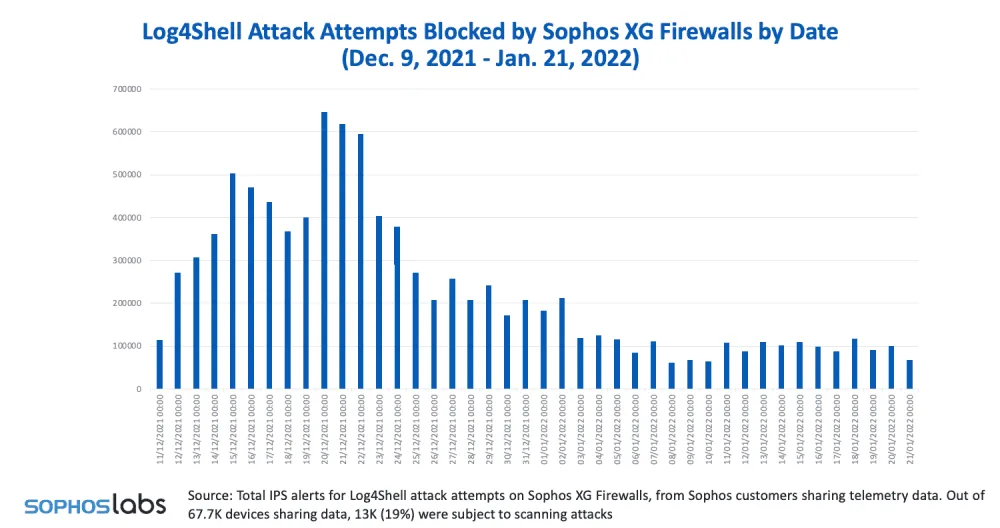
At the time, Sophos said that one of the reasons for attackers losing interest in Log4Shell was the complex nature of the Java ecosystem, where the Log4j library was implemented in different ways across Java apps.
This meant that the dead-simple universal exploit that was disclosed last year was not that universal, after all.
Threat actors had to reverse-engineer Java apps, see how and where Log4j is used, and then try different exploit variations and see what worked best. This entire process was and still is complex and time-consuming, a job that threat actors rarely bother with, especially when new vulnerabilities are disclosed each week, some of which are easier to exploit.
Since then, coordinated mass-attacks using Log4Shell have taken place, but usually only after proof-of-concept code was published somewhere online, sparing some groups from doing any of the hard work themselves.
This is how we've seen attacks only against a handful of devices, such as VMWare Horizon, VMWare vCenter, ZyXEL routers, SolarWinds Serv-U server, and Ubiquiti networking devices.
But despite the small number of Log4Shell scans and exploitation attempts today, Sophos warned defenders last month not to discount this threat.
"This doesn't mean the threat level declined too," Sophos' Chester Wisniewski said.
The researcher said that the initial spike in Log4Shell scanning in December might have been driven by security researchers monitoring the patch status of the Java ecosystem, and the current and lower number of scans may hide the real attacks.
And he was right. Four weeks later, SentinelOne put out a report about one of Iran's state-sponsored groups abusing Log4Shell to go after VMWare Horizon servers, confirming that not all attackers have lost interest in the vulnerability and the threat still remains for companies running unpatched Java systems.
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.