MortalKombat ransomware found punching targets in US, UK, Turkey, Philippines
Over the last month, organizations in the United States, United Kingdom, Turkey and the Philippines have been hit with a new ransomware that cybersecurity researchers are calling MortalKombat.
Researchers from Cisco’s Talos security team said they have been tracking a ransomware group that has been deploying MortalKombat and also developed new malware called Laplas Clipper that steals cryptocurrency from victims.
Most of the victims have been in the U.S., while a smaller percentage come from the other countries listed.
“MortalKombat is a novel ransomware, first observed by threat researchers in January 2023, with little known about its developers and operating model,” Cisco Talos said. “The name of the ransomware and the wallpaper it drops on the victim system are almost certainly a reference to the Mortal Kombat media franchise, which encompasses a series of popular video games and films.”

The ransomware “encrypts various files on the victim machine’s filesystem, such as system, application, database, backup, and virtual machine files, as well as files on the remote locations mapped as logical drives in the victim’s machine,” the researchers said.
Their report also said the ransomware group has been observed scanning the internet for organizations that have left remote desktop protocols (RDP) exposed to the internet.
The scanning allowed the hackers to target individuals, small businesses and large organizations.
Other attacks in the campaign begin with phishing emails that come with a ZIP file attached. When opened, the Laplas Clipper malware or MortalKombat ransomware deploys before deleting itself as a way to cover its tracks and make analysis more difficult.
One email seen by Cisco Talos attempted to impersonate CoinPayments, a legitimate global cryptocurrency payment gateway. The ZIP file purported to be about a specific transaction, ticking victims into opening it.
The ransomware changes the wallpaper of a victim’s machine, corrupts Windows Explorer and removes some applications.
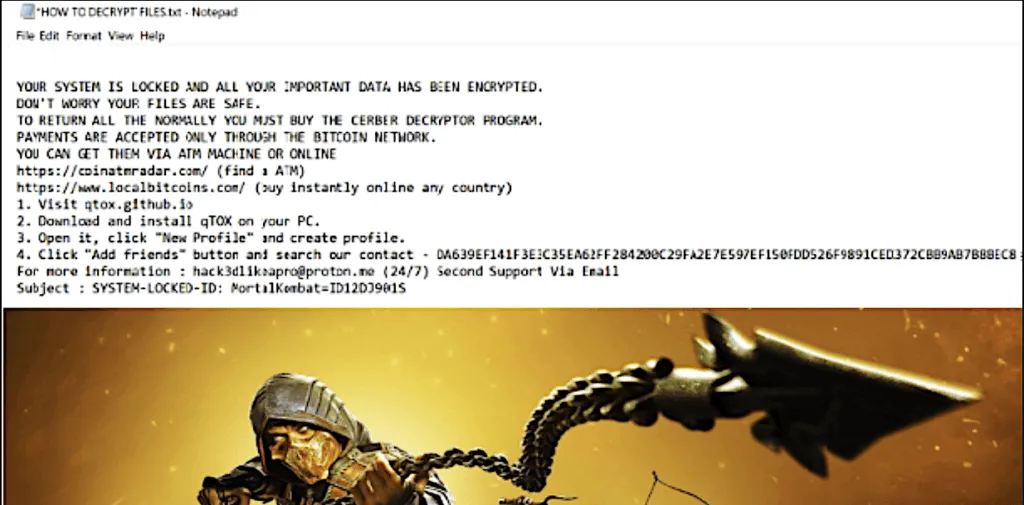
The attackers typically use instant messaging application qTOX to communicate with victims as well as an email address: “hack3dlikeapro[at]proton[.]me.”
The researchers said similarities in code and more indicate that the ransomware belongs to the Xorist family, which they said has existed in various forms since 2010.
“The ease with which the Xorist variants can be customized allows threat actors to build new variants with different names, encryption file extensions, and custom ransom notes,” the researchers said.
“Talos found a leaked version of the Xorist builder where the builder interface options closely resembled an actual Xorist ransomware builder interface, as shown in a report by PCrisk. The builder generates a ransomware executable file that the attackers can further customize.”

Alongside MortalKombat, the researchers have seen the Laplas Clipper malware – which they previously identified in attack in November 2022.
The malware monitors a user’s device for when a cryptocurrency wallet address is added to their cryptocurrency wallet address, according to Cisco, which said that once the malware finds the address, “it sends it to the attacker-controlled Clipper bot, which will generate a lookalike wallet address and overwrite it to the victim’s machine’s clipboard.”
The malware can be purchased online for $49 per week or $839 per year. The developers behind both said on Telegram that they are making new variants of the Laplas Clipper and plan to release updates in the coming months.
Cisco researchers tied two URLs to the campaign, one of which reaches a server based in Poland.
Jonathan Greig
is a Breaking News Reporter at Recorded Future News. Jonathan has worked across the globe as a journalist since 2014. Before moving back to New York City, he worked for news outlets in South Africa, Jordan and Cambodia. He previously covered cybersecurity at ZDNet and TechRepublic.



