More Zero-Days Have Been Linked to Private Companies Than Any Nation State
Over the past several years, the cybersecurity community has repeatedly raised the alarm about the ever-increasing number of private companies selling offensive cyber capabilities (OCC) to foreign governments with little oversight and no regard to if their tools are misused by oppressive regimes to commit human rights abuses.
While some OCC capabilities are provided to law enforcement agencies in countries with proper controls to limit their indiscriminate use, the OCC vendor market remains highly unregulated in most countries around the globe.
A testament to this stand the reports—mostly authored by Citizen Lab— about how hacking tools developed by private companies often end up in the hands of abusive governments, which then use these tools to track down, detain, and even murder dissidents, journalists, or political rivals.
But while the cybersecurity community is well aware of these cases, it's often hard to understand the real size of a problem without palpable numbers.
The Atlantic Council report
On Monday, U.S. think tank the Atlantic Council published a 33-page report [PDF, web page] on the OCC market and the companies that sell these services, which the organization called Access-as-a-Service (AaaS) vendors, due to their full range of services they provide.
But while the report takes a broad look at this market and analyzes three AaaS providers as part of extensive case studies (the NSO Group, an AaaS provider from Israel; ENFER, an AaaS provider located in Russia; and DarkMatter, an AaaS provider located in the UAE), the report also made an important observation that can help quantify the broader role AaaS providers now play on the cybersecurity landscape.
In particular, the report looked at the entities behind cyberattacks where a zero-day vulnerability was involved.
Using data from a spreadsheet compiled by Google Project Zero researchers, the Atlantic Council research team said that of the 129 zero-days abused in real-world attacks since 2014, there was enough information to attribute 72 to a specific threat actor.
Of these 72 cases, researchers said that 14 zero-days could be linked to private companies as the creators of the zero-day exploit that was deployed in the attack.
The 14 zero-days, taken collectively, put private companies as the largest supplier of zero-days abused in the wild, larger than any single state or the cybercrime ecosystem as a whole.
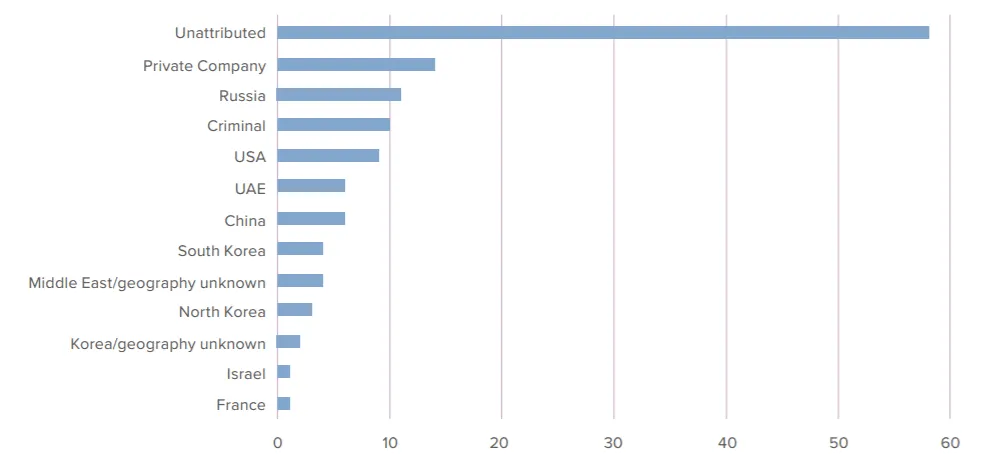
Companies responsible for the zero-days include the likes of Lench IT Solutions (the creators of commercial surveillance malware FinFisher), Exodus Intelligence, NSO Group, and Hacking Team.
"Many of the same companies mentioned above provide training at conferences (or exclusive training upon request), and have developed tailored capabilities for their customers, some of which include 0days," Atlantic Council researchers said. "Other similar groups set up their own technical command-and-control infrastructure, or assist government organizations with operational management processes."
"All of these activities fall under the broad term of OCC: a combination of technological, individual, organizational, and infrastructural elements that jointly enable operations in the cyber domain," researchers added.
"Companies offer AaaS by combining most, if not all, elements into a single service for clients. Currently, AaaS companies proliferate the full range of offensive cyber capabilities by effectively selling fully fledged services and capabilities alongside detailed training, resulting in a scale of proliferation not seen in government or criminal spaces."
Many of these AaaS vendors can barely be distinguished from legitimate cybersecurity companies that provide defensive-centered services without a very careful analysis of the services they provide.
(Un)enforceable recommendations?
Atlantic Council researchers point out that this business model is now becoming increasingly common and that the current policies that limit the export and transfer of OCC tooling across borders are becoming less efficient as AaaS vendors find new ways to go around them.
The report effectively calls for new and improved policies in regards to the AaaS market and makes some policy recommendations, such as:
- Widening the scope of vulnerabilities discovered by government intelligence agencies that need to be reported to vendors, so AaaS providers don't have a large attack surface to find their own zero-days.
- Establishing post-employment restrictions for government cybersecurity workers so they can't jump ship to AaaS providers.
- Pursuing legal actions against AaaS providers and their subcontractors that break export controls and sell to abusive governments.
- Enforcing AaaS providers to apply "technical limits" such as geofencing on malware payloads so OCC tools can't be used in certain areas or against certain victims.
But while the recommendations seem a step in the right direction, members of the cyber-security community also think they might be unenforceable.
Dave Aitel, the former CEO of Immunity Inc., a company that creates offensive security tooling, plans to hold a live stream later today, March 2, on their YouTube channel to discuss the Atlantic Council report and provide counterarguments.
I'm going to do a video live stream later today on the policy recommendations in this paper which I think are largely unworkable . https://t.co/Wd2Bkgjb4E
— Dave Aitel (@daveaitel) March 2, 2021
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.



