More than 150 Oracle Access Management systems exposed to bug highlighted by CISA
At least 151 Oracle systems are exposed to a vulnerability that the Cybersecurity and Infrastructure Security Agency (CISA) warned this week has been actively exploited.
Security research firm Censys released a report this week on the exposed Oracle Access Management systems that are vulnerable to CVE-2021-35587, which Oracle patched in January.
CISA added the bug to its list of known exploited vulnerabilities on Monday, giving federal agencies until December 19 to patch it.
CVE-2021-35587 is a vulnerability affecting Oracle Fusion Middleware Access Management, an enterprise level Single Sign-on (SSO) tool.
Censys researcher Jill Cagliostro said the bug allows “for full take over of Oracle Access Manager.” She told The Record that CISA adding the vulnerability to its exploited list means "they have evidence that there is a critical risk to United States federal civilian agencies."
“The vulnerability allows an unauthenticated (Pre-auth) attacker with network access via HTTP to compromise Oracle Access Manager and take full control of the system to conduct Remote Code Execution (RCE),” Cagliostro said.
“Given Oracle Access Manager defined in the installation guide has an ‘enterprise-level security application that provides a full range of Web-perimeter security functions and Web single sign-on services,’ this can have severe consequences for victims of such attacks.”
Cagliostro noted that the first proof of concept (PoC) exploit was published in March 2022 and several others have been released since then, giving attackers a variety of options.
Like CISA, security research company GreyNoise has also tracked an uptick in exploitation attempts, tracking at least 10 attacks using the vulnerability since November 29.
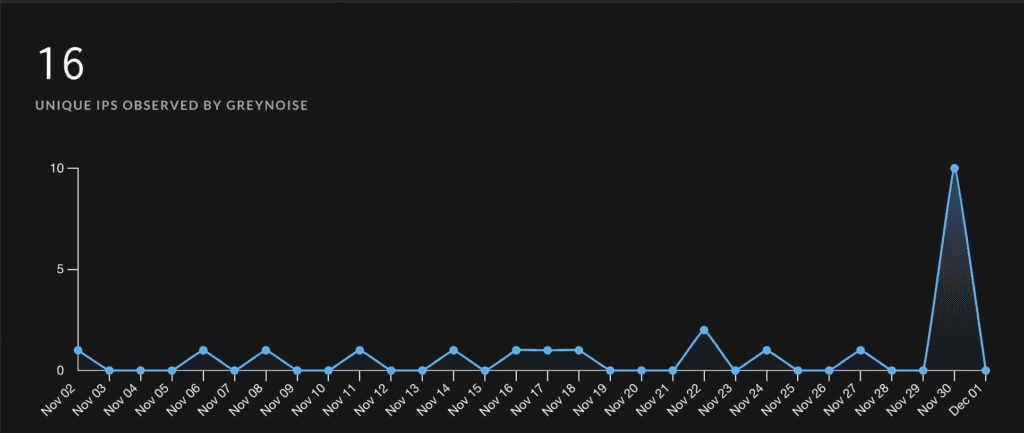
The attacks appear to originate from the United States, China, Germany, Singapore, and Canada, according to GreyNoise.
Bharat Jogi, director of vulnerability threat research at Qualys, said the bug allows for the complete control of a vulnerable system over the network without any authentication. He noted that, with exploits available, systems exposed to the internet are at highest risk as threat actors are actively scanning the internet for compromising vulnerable assets.
Netenrich’s John Bambenek added that while there are a relatively small number of such exposed servers available on the open internet, CVE-2021-35587 can be useful for lateral movement once an attacker is already on the inside.
“As Oracle often hosts critical assets, it often is slow to be patched and this is your fair warning that the time to wait on this is over,” he said.
Jonathan Greig
is a Breaking News Reporter at Recorded Future News. Jonathan has worked across the globe as a journalist since 2014. Before moving back to New York City, he worked for news outlets in South Africa, Jordan and Cambodia. He previously covered cybersecurity at ZDNet and TechRepublic.



