More than 10,000 Redline malware attacks in April targeting Internet Explorer vulnerability
Hackers deploying the Redline malware launched thousands of attacks against systems in more than 150 countries and territories in April, according to data from cybersecurity firm Bitdefender.
In a report released on Wednesday, Bitdefender said that at the start of the year, it noticed a campaign using CVE-2021-26411 exploits found in Internet Explorer to deliver the RedLine Stealer, a low-cost password stealer sold on underground forums.
RedLine allows attackers to gain access to system information like usernames, hardware, browsers installed, and anti-virus software before then exfiltrating passwords, credit cards, crypto wallets and VPN logins to a remote command and control server.
With the RedLine Stealer, hackers have the ability to extract login credentials from web browsers, FTP clients, email apps, instant messaging clients, and VPNs before selling them on underground markets.
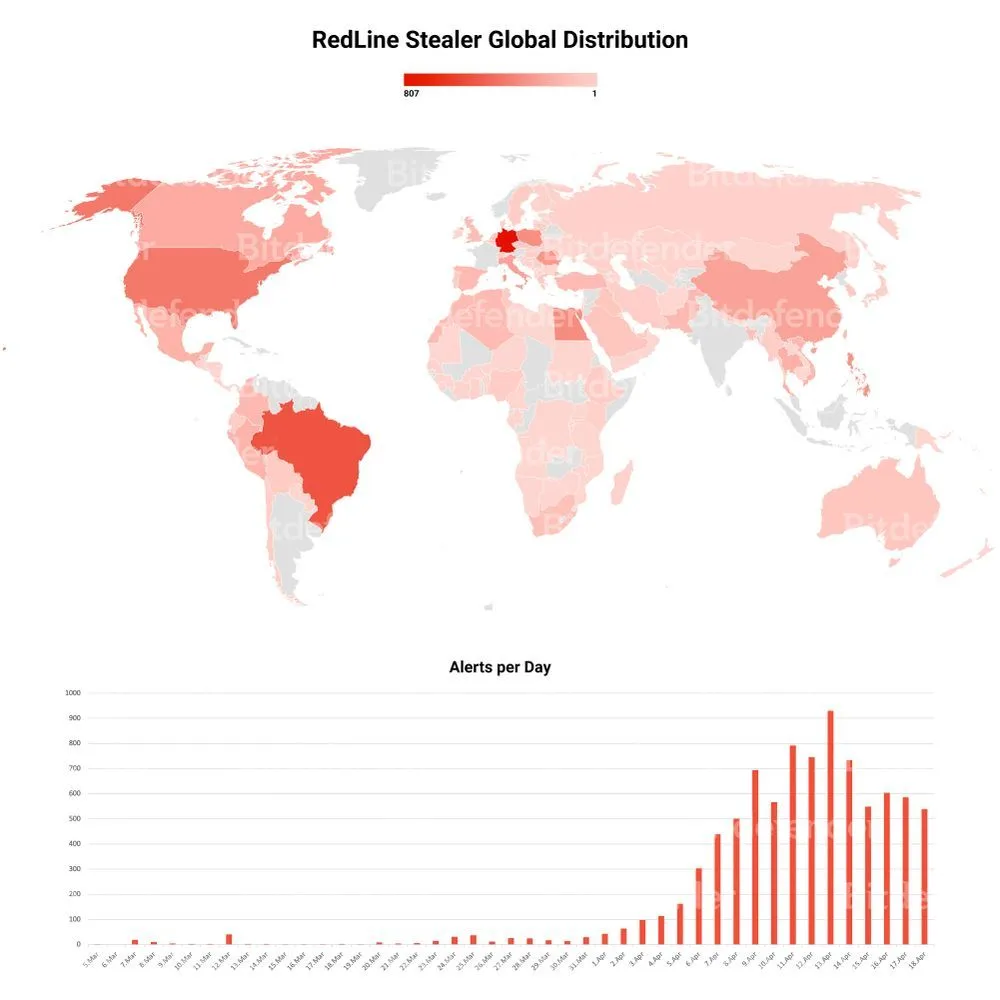
The company said it has seen a steady increase in alerts triggered by the RedLine malware in April. Bogdan Botezatu, director of threat research at Bitdefender, told The Record that they have identified over 10,000 attacks in April alone.
“And this is only as much as we can see – the real number is much higher as we can only count attacks blocked by our security solutions,” Botezatu said.
The company included a heat map showing the global distribution of the malware. Organizations in Brazil, the United States, Germany, Egypt, China and Canada all have seen hundreds of attacks involving RedLine.
“We have received reports from more than 150 countries and territories, which leads us to believe that the operation was not tailored at just a few select nations,” Botezatu added, noting that Redline is an “opportunistic stealer rather than a targeted one.”
“Preliminary information in our telemetry shows that the RedLine campaign was considerable. The diversity of stolen information, from crypto-coin wallets to various accounts allow its operators multiple opportunities for monetization.”
Recorded Future’s cybersecurity research arm Insikt Group discovered in October that the vast majority of stolen credentials currently sold on two dark web underground markets were collected using the RedLine Stealer malware. The Record is an editorially independent publication owned by Recorded Future.
Recorded Future analyst and product manager Dmitry Smilyanets corroborated Bitdefender's findings and added that the real number of compromised hosts is much higher.
"Based on the dataset from the past six weeks we can state that Brazil, Indonesia, India, and the US were the primary targets," Smilyanets said.
The malware has been sold on several underground hacking forums since March 2020 and was initially developed by a programmer named REDGlade, according to Insikt Group.
Threat actors and groups were particularly drawn to the malware because pirated versions of it were released on hacking forums.
HP released its own report in February detailing a recent campaign where hackers used a fake Windows 11 installer as a way to spread the RedLine Stealer.
Last year, a North Korean cyber-espionage group used the Internet Explorer vulnerability to breach one of the most popular North Korean-themed news sites on the internet in order to carry out a watering hole attack and infect some of the site’s visitors with malware.
Security firm Volexity said in a report that the threat actor used public proof-of-concept code posted online.
The report provides a detailed review of how the actors behind the campaign used CVE-2021-26411, a newer exploit in the Internet Explorer and legacy Edge browsers.
Jonathan Greig
is a Breaking News Reporter at Recorded Future News. Jonathan has worked across the globe as a journalist since 2014. Before moving back to New York City, he worked for news outlets in South Africa, Jordan and Cambodia. He previously covered cybersecurity at ZDNet and TechRepublic.



