Mobile phone hackers wield 'Violence-as-a-service' for money, revenge
If you ask ‘Yuki’ why he helped found a channel on Telegram to facilitate the settling of scores in the mobile phone hacking community, he says it was about supply and demand. Lots of young SIM swappers were looking for a way to get back at enemies in the real world.
SIM swapping at its most basic level entails someone hijacking your mobile phone. They swap your SIM card and all the information on it for a SIM card they own – and just like that they have access to your passwords, your emails, and the two-factor authentication codes that protect bank accounts and cryptocurrency wallets. SIM swappers have been draining those accounts and stealing millions.
The big money has given rise to something even more troubling — a new phenomenon known as violence-as-a-service. It has become the acceptable way to settle scores in the SIM swapper community. Doxing or defacing websites, they told us, just doesn’t send enough of a message. So they are throwing Molotov cocktails or slashing tires in the real world instead.
Detective David Hale of the Westtown East Goshen Police Department investigated an apparent violence-as-a-service incident in January in West Chester, Pennsylvania, in which someone opened fire on a house. No one was injured. According to a criminal complaint first reported by Krebs on Security, a SIM swapper named Patrick McGovern-Allen, 21, was allegedly involved.
Violence-as-a-service is the next iteration of something that became a popular harassment technique among adolescents a decade ago: swatting. Young kids would call emergency services and get the police to send SWAT teams to somebody’s house, and it got people killed.
The concern is that violence-of-a-service will do the same. “I think it's fair to say that it's an issue and it's not going away anytime soon,” Detective Hale told Click Here.
To try to better understand the phenomenon, we spoke with Yuki, a SIM swapper who set up a Telegram channel to try to facilitate this SIM swapper on SIM swapper violence in the real world. His group, called BRICKSQUAD, launched in August, offering a kind of match.com for violence.
One ad asks if anyone can be in Sydney’s Hyde Park: “Anyone who can be here on Sept 8th around midday and wants to make a thousand dollars… dm me.” Another, in Houston, FL: “wanna brick a window for $500… let me know.”
The Click Here podcast interviewed Yuki and a number of other SIM swappers on tape for this week’s episode. We verified Yuki’s identity in a number of ways. He is listed as the owner of BRICKSQUAD’s encrypted Telegram channel and his voice is on a violence-for-service video, and it matches the voice of the Yuki we interviewed.
We talked with him about the world of SIM swapping, why violence-as-a-service is growing in popularity and the concern that violence in the SIM swapper community will eventually find its way into the wider world. When we asked if they have any remorse for exacting this kind of violence they said no, ‘this is just business. If you steal money, there are consequences.” The interview has been edited and condensed for clarity.
Click Here: Can you explain how SIM swapping works?
Yuki: Now, the first thing you probably wanna do is go on to whatever carrier they're using, and try to social engineer them to reset the email, connect to their ISP and get into the email, find whatever you can find.
And then what you want to do is make sure you have the tools up for the carrier like a manager login so they can do the activation. It's like a three man job, basically. You would have a guy that does social engineering, someone that holds the SIM on the phone, and then a guy that actually does the activation. Then after you have the phone number, you would be able to access all the crypto wallets like Coinbase, Binances, anything.
You would never SIM swap someone with no money. You’d first check for a Coinbase link to the email or a Binance. Sometimes it happens and you get into an account that has like zero balance.
CH: The people who are on the receiving end of a SIM swap are usually those who have Bitcoin or Ethereum or have some sort of cryptocurrency?
Y: Yes. That's what you're really going after. It's not their information so much as their cryptocurrency.
CH: And now many of these SIM swappers are going after each other. Is ‘in real life’ violence a relatively new thing in SIM swapping?
Y: Yeah, people have only been doing it since around last year, and nobody's actually made a business out of it, like a proper business. They just do it like an odd job.
CH: And do you feel remorse for all of this?
Y: A lot of it's business. If you're a scammer, there's a lot of chance that you will get a molotov thrown at your house or maybe have your house shot up. If you wanna steal someone's money, there's a lot of consequences from that. If you want to scam someone for a thousand dollars, then the person you’re scamming may spend a thousand dollars to have a brick thrown at your house. It's all business.
CH: Who is paying you to do this and who are you targeting with these jobs?
Y: They're all kind of the same people, all SIM swappers, like-minded people. They pay us to do this and also are the targets.
CH: Is it right to think of the SIM swapping community as being on the younger side?
Y: That is very accurate. A lot of SIM swappers are actually like 13 to 18.
CH: So is most of this violence directed at teenagers?
Y: Yeah, pretty much.
CH: And a few months ago you co-founded a Telegram channel that promotes these IRL violent services. Talk to me about BRICKSQUAD.
Y: I started it as a side project and it's more like a supply to demand type of thing. You know, like people [in the SIM swapping community] really want to get back at their enemies online. BRICKSQUAD is the frontlines. That's where most of the big crimes happen.
CH: Give me some examples of the kind of violence-as-a-service BRICKSQUAD is providing.
Yuki: You can order to get someone bricked, which means having a brick thrown through their house. We also get people offering to throw a Molotov cocktail at a house. It's pretty basic, but people do it and they get paid.
CH: And what does something like that cost?
Y: People pay around $1,000 for a bricking. Normally, the starting price to shoot up a house is $5,000. If you want someone actually killed or kidnapped, that would go for way more.
CH: And do you or your squad do the actual bricking or do you just say, ‘Hey, we have a job,’ and act as an intermediary?
Y: No, we do both. Sometimes we proxy people, which means you can get other people to do it and you get paid for it. Or you can just do it yourself if you’re in the area. The squad does the more serious stuff, like shootings, robberies, and even killings.
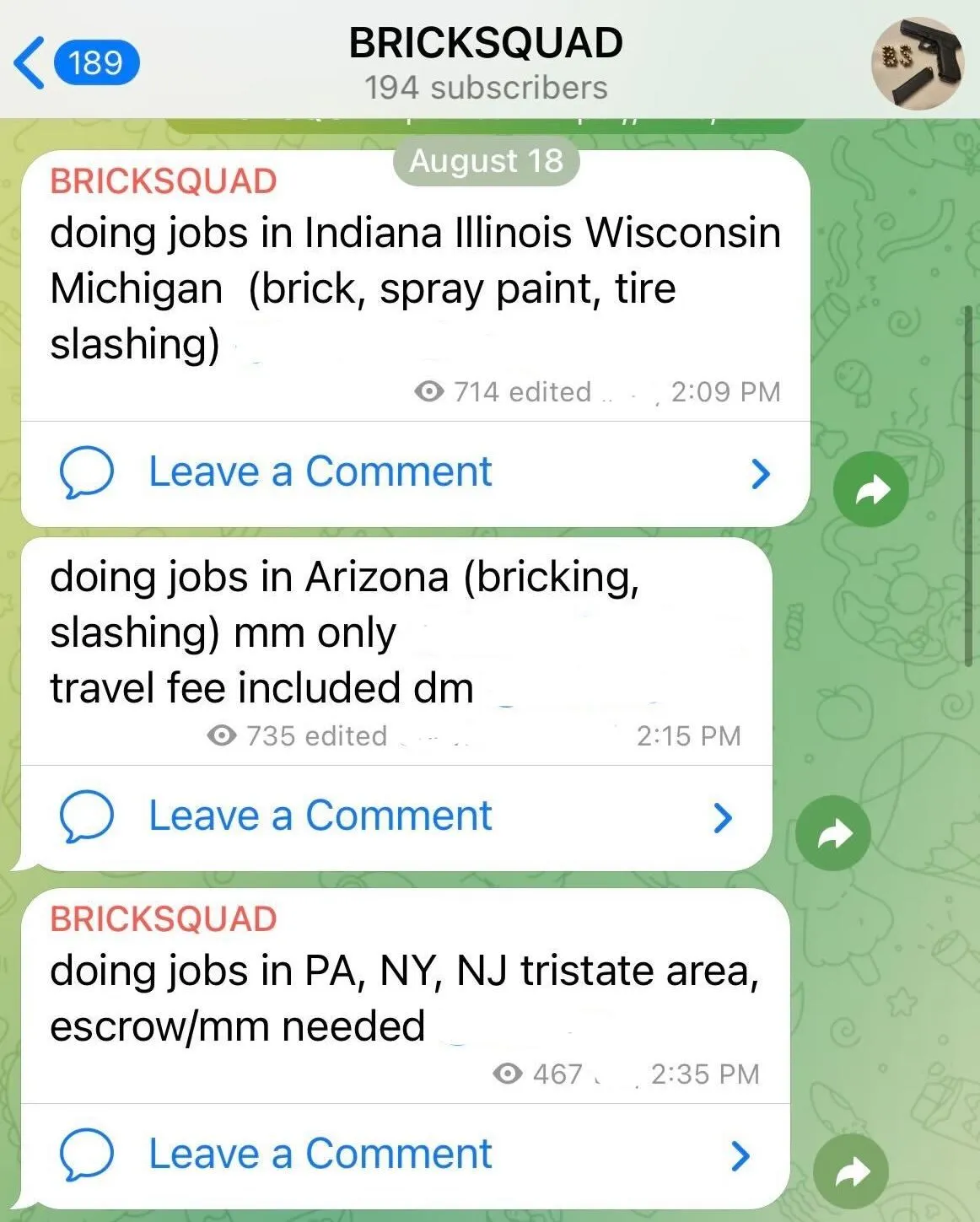
A screenshot from BRICKSQUAD’s telegram channel promoting violence-as-a-service. NOTE: Usernames in each post have been redacted.
CH: Can you give me an example of a recent bricking?
Y: Yeah, the last person that I've gotten bricked was a few days ago. They were lying about having T-Mobile tools up and tried to charge me like a thousand dollars for an activation. So I actually went to one of their ex-girlfriends and I was like, do you have information on this guy? She gave me all his information, so she got bricked.
CH: Did you film that?
Y: No comment. (pause) Okay. I didn't do it. So, I didn't film it, but there was someone that got bricked and that was because of me.
CH: And there was a video?
Y: There is a video.
CH: When people order these services, do they tell you the reason, or is it no questions asked?
Y: Normally you already know what the reasoning is because the SIM swapping community is already talking about it. But there are times where you get a random person who just wants someone bricked and then it’s no questions asked. I’ll get it done.
CH: And do you guys ever venture out of that community, like bricking someone who isn't a SIM swapper or isn't in the online community?
Y: It's definitely bleeding over to other communities, like a lot of regular communities on Discord have heard about getting people bricked and Molotov cocktails getting thrown, but nobody really knows who's doing it.
We have also bricked some employees of companies for scare tactics.
CH: Like a telephone company?
Y: Yeah, a telephone company.
CH: So, somebody who’s on the fringes of the community, but not directly involved?
Y: Yeah, exactly.
CH: What do you do to protect yourself from getting into trouble?
Y: Well, first step you don't reveal a lot of your information, like where you live. That could lead to people reporting you to the police. The second step: always use protection, like a VPN or even a residential proxy. The third step is you want to always make sure that you don't give out your phone number or anything like that.
In the SIM swapping community, having a phone number leaked, people will SIM swap you just for fun because they have the tools.
I'm going to tell you, I don't actually have a phone.
CH: Is that because you know how easy it is to SIM swap?
Y: No comment.
CH: So, recently a SIM swapper named Patrick McGovern-Allen was arrested for taking part in a pair of violence-as-a-service operations. He went by the online alias, “Tongue.” Have you considered shutting down BRICKSQUAD because of the extra attention brought on by Patrick’s arrest?
Y: I did, but instead we just launched a website for our services. Realized that there's nothing much to worry about. You can be reckless and safe at the same time. So I just thought about that and, you know, decided that I would just keep it up.
CH: Do you have a plan when you won't do this anymore, is there a certain amount of money you'll get to that?
Y: I think about $100 million, and I have a long way to go. That's a few more years at least.
CH: Do you think violence-as-service is a short-lived thing?
Y: I think it's going to grow even bigger. I think a lot of it's gonna grow outside of the community into more political employees, government officials. It's definitely gonna go into that eventually. A lot of people have connections to government officials now in the SIM swapping community with getting all their information and then blackmailing them for authentication codes and logins and stuff.
Sometimes they can't SIM swap them. So, they go to the last resort, which is extorting them. And if they don't go through with it, then they'll get the house shot up, I guess.
CH: have you actually seen that happen or do you, do you think that's just where it's trending?
Y: That's just my prediction, you know?
Dina Temple-Raston
is the Host and Managing Editor of the Click Here podcast as well as a senior correspondent at Recorded Future News. She previously served on NPR’s Investigations team focusing on breaking news stories and national security, technology, and social justice and hosted and created the award-winning Audible Podcast “What Were You Thinking.”
Sean Powers
is a Senior Supervising Producer for the Click Here podcast. He came to the Recorded Future News from the Scripps Washington Bureau, where he was the lead producer of "Verified," an investigative podcast. Previously, he was in charge of podcasting at Georgia Public Broadcasting in Atlanta, where he helped launch and produced about a dozen shows.




