Microsoft to leverage Intel CPUs to detect crypto-mining malware
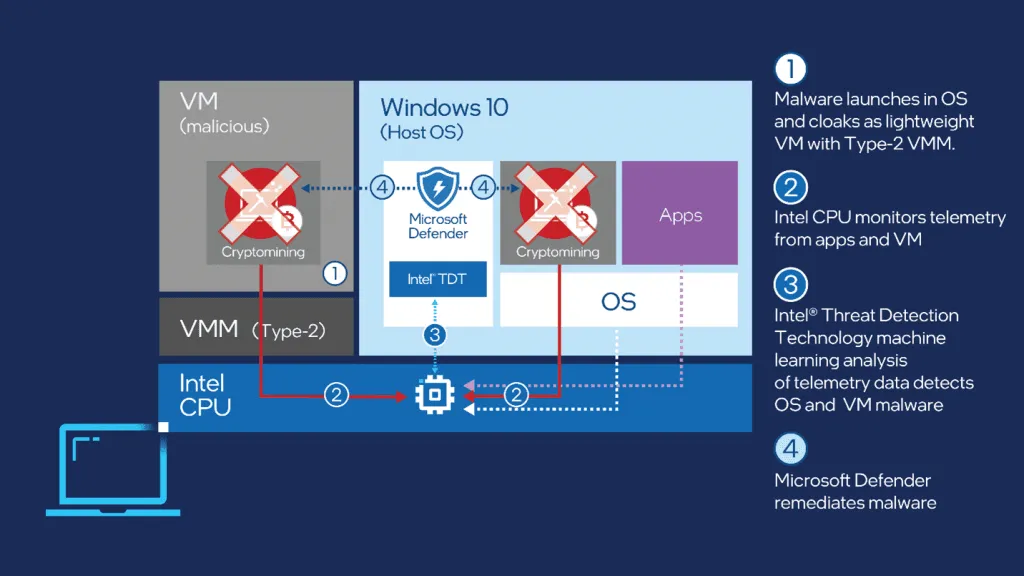
Microsoft said today that it is rolling out an update to the commercial version of the Defender antivirus that will now be capable of using a little-known Intel CPU security feature to detect crypto-mining malware at the processor level.
The technology, known as Intel TDT (Threat Detection Technology), works by exposing CPU heuristics and telemetry to security software so the data can be analyzed using machine learning for malicious code that evaded antivirus engines at the operating system level.
Microsoft explains:
This technology [the TDT] is based on telemetry signals coming directly from the PMU, the unit that records low-level information about performance and microarchitectural execution characteristics of instructions processed by the CPU. Coin miners make heavy use of repeated mathematical operations, and this activity is recorded by the PMU, which triggers a signal when a certain usage threshold is reached. The signal is processed by a layer of machine learning which can recognize the footprint generated by the specific activity of coin mining. Since the signal comes exclusively from the utilization of the CPU, caused by execution characteristics of malware, it is unaffected by common antimalware evasion techniques such as binary obfuscation or memory-only payloads.
This is the third known case where Intel TDT is deployed in a real-world security product.
TDT was used for the first time in 2018 by Microsoft and Cisco to accelerate memory scans for their Windows Defender Advanced Threat Protection (now rebranded as Microsoft Defender for Endpoint) and Tetration platforms, respectively.
Earlier this year, Boston-based security firm Cybereason used TDT to create a ransomware detection module for its antivirus engine. This module worked similarly to Microsoft's new crypto-mining detection feature—by tapping into the TDT data stream to detect ransomware-specific operations at the CPU level.
Because of its unique insight and ability to work at the CPU level rather than the OS level, Intel TDT is expected to see broader adoption in the future.
This is especially relevant as more and more malware creators are adding antivirus evasion code to their malware, and as some cybercrime groups are realizing they could evade antivirus detection by hiding malware inside virtual machines. While a virtual machine may be able to hide malicious code from its parent OS, it can't hide it from the CPU.
Furthermore, the time is also right for a broader TDT adoption. While the technology has been around for years, it took some time before CPUs made it into users' hands.
Intel said today that there are nearly a billion Intel TDT-capable PCs in the market; CPUs where security vendors can now tap into TDT to deploy next-level detection capabilities.
Currently, TDT is included with Intel Core processors and with any Intel CPU series that supports Intel vPro, a collection of enterprise-centered technologies.
Unfortunately, the new crypto-mining detection capabilities are not supported on the free version of the Defender antivirus, which ships with all Windows 10 operating systems.
It is only supported on Microsoft Defender for Endpoint, which is the paid version of Defender, comes with extra features, and is only sold to enterprise customers.
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.



