Microsoft takes control of 17 domains used by West African BEC gang
Microsoft has obtained a court order on Friday allowing it to seize control of 17 domains that were being abused in a business email compromise (BEC) campaign against some of its Office 365 customers.
According to court documents obtained by The Record, the domains were intentionally registered to resemble the names and domains of legitimate businesses but with slight variations in how the domain was spelled.
The technique relied on homoglyphs, which are letters or characters that look very similar to others, and a technique that has been widely abused for years by cybercrime groups trying to pose as the company's executives or an important contractor.
The most common homoglyphs used in these types of attacks rely on replacing uppercase "I" and a lowercase "l" or the number "0" with the uppercase "O," and vice versa.
Employees receiving an email or a link to a phishing site hosted on one of these domains would have a hard time recognizing the fake domain that was using a homoglyph lookalike character from the legitimate one.
Seized domains belonged to a West African BEC gang
"This case started with a single customer complaint regarding BEC, and our investigation revealed that this criminal group had created 17 additional malicious homoglyph domains that were registered with third parties," Microsoft said.
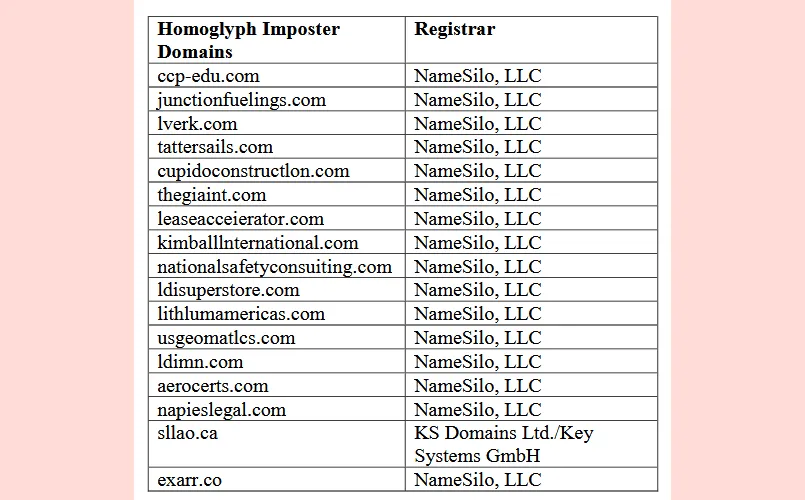
The Redmond company said the group behind these attacks appears to have been operating out of West Africa and had been using the lookalike domains to pass as employees or executives in order to trick other employees, customers, or contractors into updating financial details and sending payments to bank accounts under their control.
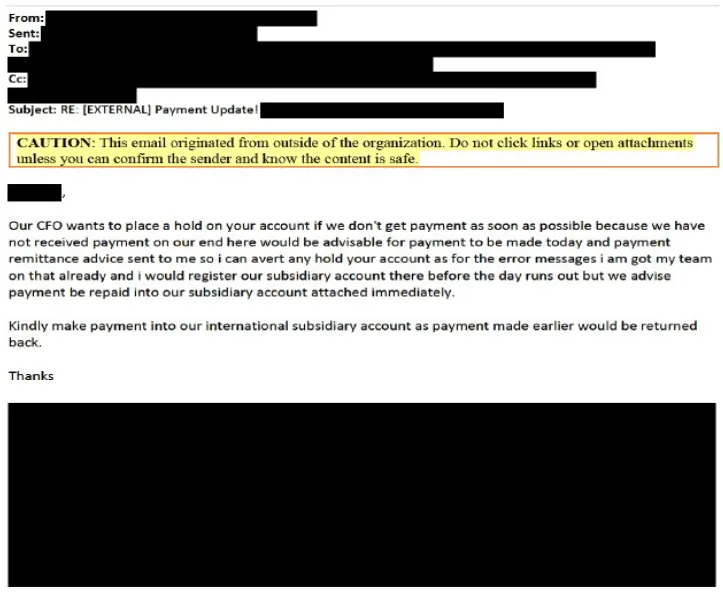
The tactic, known as email fraud or business email compromise (BEC), was the most profitable cybercrime category in 2020, according to an FBI report published in April, accounting for $1.8 billion in losses, around 43% of all of last year's total funds lost to cybercrime groups.
Microsoft said that by seizing the group's 17 domains, they hope to have disrupted ongoing attacks and prevented the group from cashing in on some of their operations.
While the domain seizures won't stop the group from registering new ones, this was a small victory the OS maker was willing to take on behalf of some of its customers.
Microsoft's 24th legal action
In total, this marks the 24th legal action Microsoft has taken against cybercrime and cyber-espionage groups, Amy Hogan-Burney, General Manager for the Microsoft Digital Crimes Unit, said today.
Prior to last week's domain seizures, Microsoft had also filed lawsuits that allowed the company to take control of domains previously owned by the SolarWinds hackers, COVID-19 scamming operations, APT35 Iranian hackers, the Necurs botnet, and Thallium, a North Korean cyber-espionage group.
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.



