Microsoft says Warlock ransomware deployed in SharePoint attacks as governments scramble
Chinese hackers are exploiting a new vulnerability in Microsoft SharePoint products to deploy ransomware, increasing the pressure on governments around the world as they race to assess any damage done to their systems.
In an update on Wednesday night, Microsoft said a China-based actor it identifies as Storm-2603 is now deploying Warlock ransomware after exploiting CVE-2025-49706.
The ransomware has only been around since June after advertisements for it — which were titled “if you want a lamborghini, please call me” — emerged on Russian cybercrime forum RAMP. Recorded Future ransomware expert Allan Liska said the group behind Warlock is a ransomware-as-a-service operation with at least 11 victims so far.
Storm-2603 has no ties to the other Chinese state-backed groups Microsoft previously said were targeting unpatched on-premises SharePoint systems exposed to the internet. The tech giant explained that it had previously seen Storm-2603 use the Warlock ransomware and at times deploy the LockBit ransomware strain.
The group began using ransomware during this campaign on July 18 and investigators saw the threat actors take a number of actions after gaining initial access — including disabling Microsoft Defender protections. Compromised environments are then encrypted with the Warlock ransomware.
While the group is based in China, Microsoft previously said it is “unable to confidently assess the threat actor’s objectives.” The two other Chinese groups identified with the so-called “ToolShell” campaign — Linen Typhoon and Violet Typhoon — are confirmed state-backed actors known for more than a decade of espionage and intellectual property theft.
Federal compromises
The concerns raised by the cybersecurity community about CVE-2025-49706 and its related vulnerabilities were realized this week when prominent victims were notified.
Netherlands-based cybersecurity firm Eye Security told Reuters and Bloomberg that hackers have successfully breached at least 400 governments and businesses around the world.
A Cybersecurity and Infrastructure Security Agency (CISA) official told Recorded Future News that it is aware of federal agencies as well as state entities that may be affected by the campaign.
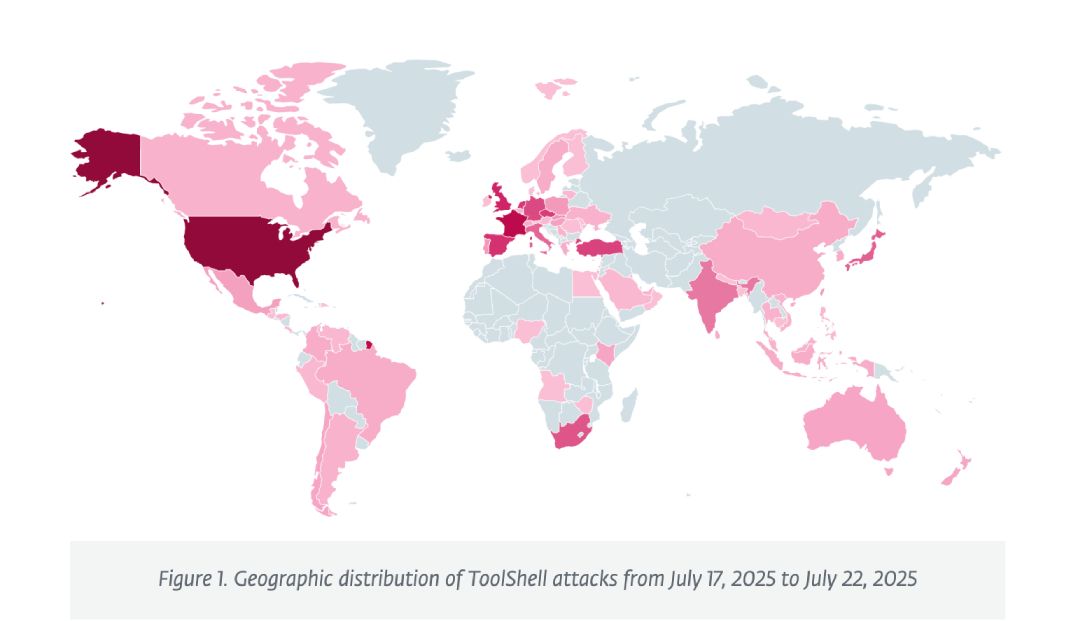
Image: ESET
CISA Acting Executive Assistant Director for Cybersecurity Chris Butera said they are working with Microsoft and other federal partners to address the ToolShell campaign.
Butera added that the Muli-State Information Sharing and Analysis Center (MS-ISAC) has been instrumental in helping them notify potentially impacted state and local partners.
“We are still early in the incident response and we are continually assessing the scope and impact,” he told Recorded Future News.
Bloomberg first reported on Tuesday that the National Nuclear Security Administration was breached through the vulnerability. It is in charge of running the U.S. nuclear weapons supply.
A spokesperson confirmed that “the Department of Energy, including the NNSA” was breached on July 18.
“The Department was minimally impacted due to its widespread use of the Microsoft M365 cloud and very capable cybersecurity systems,” the spokesperson said. “A very small number of systems were impacted. NNSA is taking the appropriate action to mitigate risk and transition to other offerings as appropriate.”
The spokesperson added that they do not know of any sensitive or classified information that was compromised.
By Wednesday, the Washington Post obtained a letter saying the National Institutes of Health was breached through the vulnerability and NextGov reported that the Department of Homeland Security was impacted as well.
A DHS official said their investigation into potential exposure remains ongoing.
“However, there is no evidence of data exfiltration at DHS or any of its components at this time,” a spokesperson claimed.
DHS explained that CISA has been “working around the clock with Microsoft, impacted agencies, and critical infrastructure partners to share actionable information, apply mitigation efforts, implement protective measures, and assess preventative measures to shield from future attacks.”
The State Department told Recorded Future News that it is working with CISA and other federal agencies to investigate its exposure.
Experts at ESET said of all the active ToolShell exploitations across the world, the U.S. accounted for 13% of attacks and was the most targeted country, according to their data. The company first saw exploitation in Germany on July 17 before seeing another on July 18 in Italy.
ESET researchers confirmed Microsoft’s assessment that Chinese government-backed groups are seizing on the bug and the company’s telemetry showed “the victims of the ToolShell attacks include several high-value government organizations that have been long-standing targets of these groups.”
Jonathan Greig
is a Breaking News Reporter at Recorded Future News. Jonathan has worked across the globe as a journalist since 2014. Before moving back to New York City, he worked for news outlets in South Africa, Jordan and Cambodia. He previously covered cybersecurity at ZDNet and TechRepublic.



