Microsoft notifies UK customers affected by hackers abusing ‘verified publisher’ tag
Microsoft said it has notified customers impacted by a campaign that involved the abuse of the company’s “verified publisher” status to allow access to a victim’s cloud environments.
Accounts can gain verified publisher status when an app publisher has verified their identity using their Microsoft Partner Network (MPN) account and has associated this MPN account with their app registration, according to Microsoft.
But researchers with cybersecurity firm Proofpoint discovered a campaign that began on December 6 where hackers tricked users into granting them access to an account because they were a verified publisher.
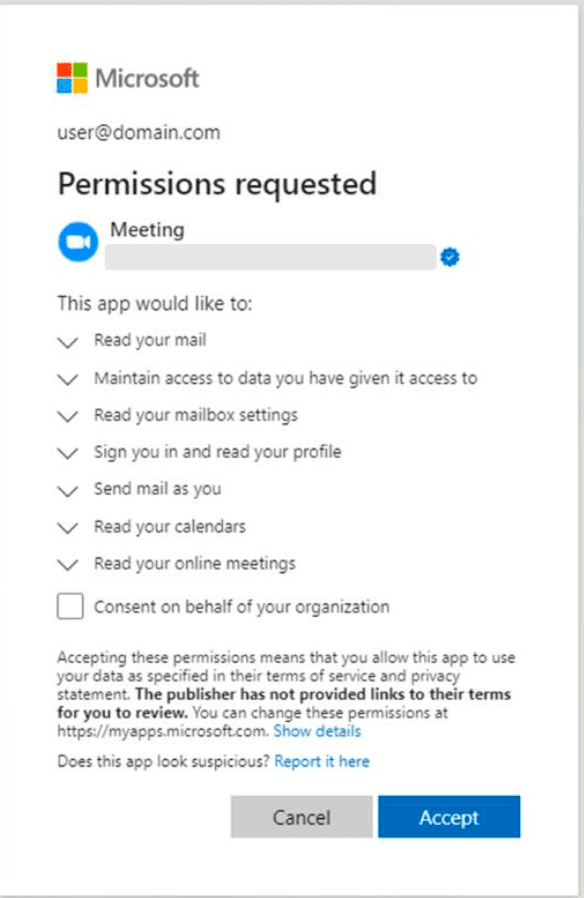
The hackers were able to gain access to users’ mailboxes, calendars, and meetings before stealing data. Microsoft told The Record that they call these attacks “consent phishing.”
“Consent phishing is an ongoing, industry-wide issue and we’re continuously monitoring for new attack patterns,” a Microsoft spokesperson said.
“We’ve disabled these malicious apps and are taking additional steps to harden our services to help keep customers secure. The limited number of customers who were impacted by the campaign described in the Proofpoint blog have been notified.”
The spokesperson noted that Microsoft has published blog posts on the topic with information and best practices to help customers avoid these kinds of issues.
Proofpoint researchers said hackers have realized the value in having verified status in the Microsoft environment, noting that attacks were less likely to be detected and stopped than traditional targeted phishing or brute force attacks.
Organizations typically have weaker defense-in-depth controls against threat actors using verified apps, the researchers explained.
Once a publisher has been verified, users will see a blue verified badge in the Azure Active Directory (Azure AD) consent prompt for the app and on other webpages.
“We identified three malicious apps created by three different malicious publishers. These apps targeted the same organizations and are associated with the same malicious infrastructure,” the researchers said.
“Multiple users were observed authorizing the malicious apps, thereby compromising their organization’s environment. According to our analysis, this campaign appeared to target mainly UK-based organizations and users. Among the affected users were financial and marketing personnel, as well as high-profile users such as managers and executives.”
In all of the cases discovered by Proofpoint, the infrastructure behind the malicious apps was established days or weeks before December 6. They informed Microsoft of the campaign on December 20 and the tech giant disabled the applications on December 27.
Proofpoint noted that Microsoft is still investigating this attack and has updated its partner vetting processes in an effort to stop future attacks.

Before the changes were made, hackers given tokens had permissions that could last more than a year while also allowing threat actors to use the compromised account in subsequent attacks.
“For such organizations, it is very difficult to identify that their brand is being abused in these attacks. There is no required interaction between the impersonated organization and the malicious verified publisher,” the researchers said, noting that they have reached out to companies to warn them about brand abuse.
The hackers used a range of tricks to boost their credibility, including using legitimate-looking names like “Acme LLC” or photos impersonating other brands like Zoom.
Proofpoint researchers told The Record that companies should be careful when granting access to third-party apps while taking proactive steps to protect their cloud environments.
“Do not trust and rely on OAuth apps based on their verified publisher status alone. Due to the sophistication of such attacks, end users are likely to fall prey to the advanced social engineering methods outlined in this blog,” they said.
Jonathan Greig
is a Breaking News Reporter at Recorded Future News. Jonathan has worked across the globe as a journalist since 2014. Before moving back to New York City, he worked for news outlets in South Africa, Jordan and Cambodia. He previously covered cybersecurity at ZDNet and TechRepublic.