Microsoft: Nation-state Iranian hackers exploit Log4Shell against Israel
Iranian hacker group MuddyWater, allegedly linked to the country's state intelligence service, continues to exploit the Log4j vulnerability to gain access to corporate networks in Israel amid an ongoing proxy war between the two countries, according to new research.
The threat actor, which is also known as Mercury, has targeted vulnerabilities in SysAid, a popular IT management software used by many Israeli organizations, according to a report published by Microsoft on Thursday.
U.S. Cyber Command said earlier this year that the group is affiliated with the Iranian Ministry of Intelligence and Security. In December, the group targeted telecommunication and IT service providers in the Middle East and Asia.
MuddyWater's new attack, detected by Microsoft in late July, is another example of state-sponsored operations exploiting Log4Shell, a vulnerability in the Java library Log4j used to add logging capabilities to web and desktop applications.
Earlier in December, Microsoft discovered that nation-state groups from China, Iran, North Korea, and Turkey were abusing Log4Shell to gain access to targeted networks. MuddyWater, for instance, used flaws in Log4j to exploit vulnerabilities in VMware apps, which were eventually patched.
Looking for an alternative, Iranian hackers have turned to SysAid, another attractive target as it is used by numerous organizations in Israel, according to Microsoft.
The group used Log4j flaws to gain initial access to unpatched SysAid systems and dropped an infected script, a web shell, to run malicious commands. The hackers then added a new user and elevated its privilege to a local administrator. They also added malware to startup folders to ensure access even if the victim rebooted their system.
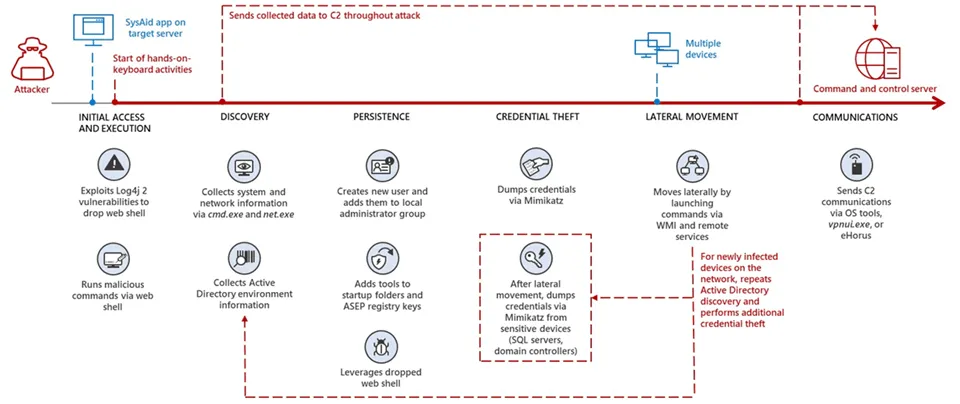
According to Microsoft, the hackers stole user credentials by leveraging the open-source application Mimikatz.
Microsoft urged organizations using SysAid to apply security patches and update affected products and services. SysAid rolled out Log4j patches for its products in January, a month after a bug was discovered by an employee of the Chinese tech giant Alibaba.
Microsoft also published indicators of compromise allowing companies to investigate whether they exist in their systems.
Log4j is present in almost all major Java-based enterprise apps and servers. Open-source projects like Redis, ElasticSearch, Elastic Logstash, and the NSA’s Ghidra use it to some extent. Among the companies whose servers may be vulnerable to Log4Shell attacks are Apple, Amazon, Twitter, Cloudflare, Steam, Tencent, and Baidu.
With a score of 10/10 on the CVSSv3 severity scale, Log4Shell opens up hundreds of millions of devices to exploitation, cybersecurity experts have warned.
Earlier in August, the U.S. Department of Homeland Security acknowledged that it will be years before Log4j is found and addressed. Researchers also call it an “endemic vulnerability.”
In December, the U.S. Cybersecurity and Infrastructure Security Agency ordered all federal civilian agencies to update their software in response to the threat.
Daryna Antoniuk
is a reporter for Recorded Future News based in Ukraine. She writes about cybersecurity startups, cyberattacks in Eastern Europe and the state of the cyberwar between Ukraine and Russia. She previously was a tech reporter for Forbes Ukraine. Her work has also been published at Sifted, The Kyiv Independent and The Kyiv Post.



