Microsoft: Malware gang uses website contact forms for distribution
Microsoft said today it spotted a cybercrime operation abusing contact forms on legitimate websites to target companies and their workers in attempts to infect them with the IcedID malware.
One of Microsoft's security teams highlighted the creativity and effectiveness of this campaign, which is currently seeing a spike in activity.
The technique behind these attacks is simple and relies on threat actors using automated scripts to visit the websites of legitimate businesses and filling out contact forms with bogus legal threats.
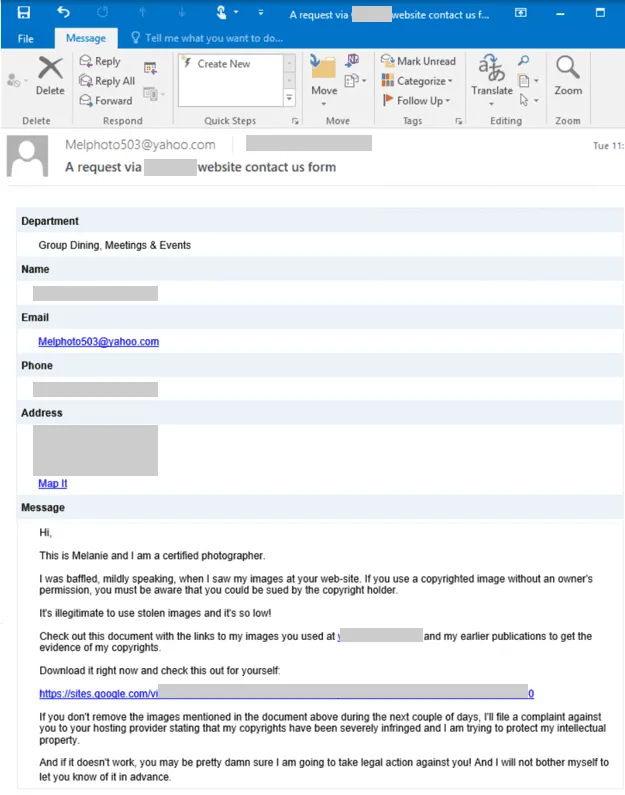
The emails, which are delivered to the site's owners, contain links to third-party sites where company employees are told to log in and inspect the legal documents.
But in a blog post today, Microsoft says these documents contain malicious code that infects victims with the IcedID malware.
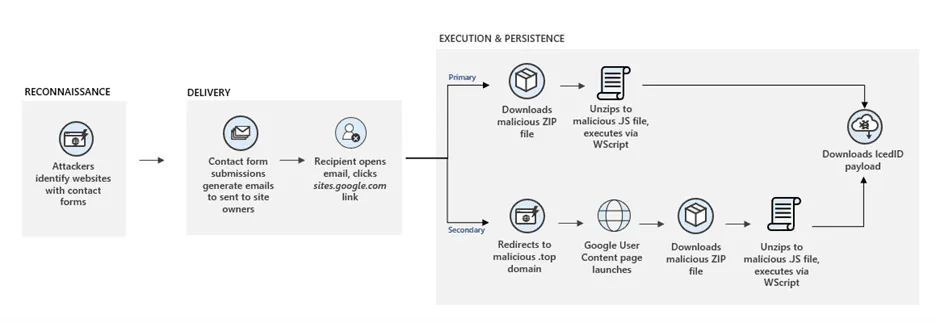
Microsoft is now warning security teams and system administrators to take note of this technique, which might dupe employees into thinking that because the emails come from their own public websites, they might not be a source of attacks.
In particular, Microsoft warns companies to stay vigilant due to the use of IcedID as a final payload. This malware, first seen in 2017, is currently used to provide access to infected networks to other cybercrime gangs.
Previous reporting has seen systems infected with IcedID being used to deploy ransomware inside corporate networks, such as Maze and Egregor payloads.
But Microsoft said that while the campaign it discovered in recent days was deploying the IcedID trojan, attackers could easily switch to any other malware threat they'd wish.
Contact form attacks have been taking place since 2020
In an email interview with The Record today, Sherrod DeGrippo, senior director of Threat Research and Detection at Proofpoint, said the technique has been gaining ground since last year.
"Proofpoint has observed this technique in use since 2020 to deliver a variety of payloads," DeGrippo said.
"The threat actor conducting these campaigns often used Buer Loader with final payloads of Ursnif and IcedID."
The Proofpoint exec says that while abusing corporate websites "may seem ultra-targeted," Proofpoint has seen indicators to suggest the attacks "are much broader in nature, hitting hundreds of orgs per campaign in an automated fashion."
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.