Microsoft launches center for reporting malicious drivers
Microsoft has launched this week a special web portal where users and researchers can report malicious drivers to the company's security team.
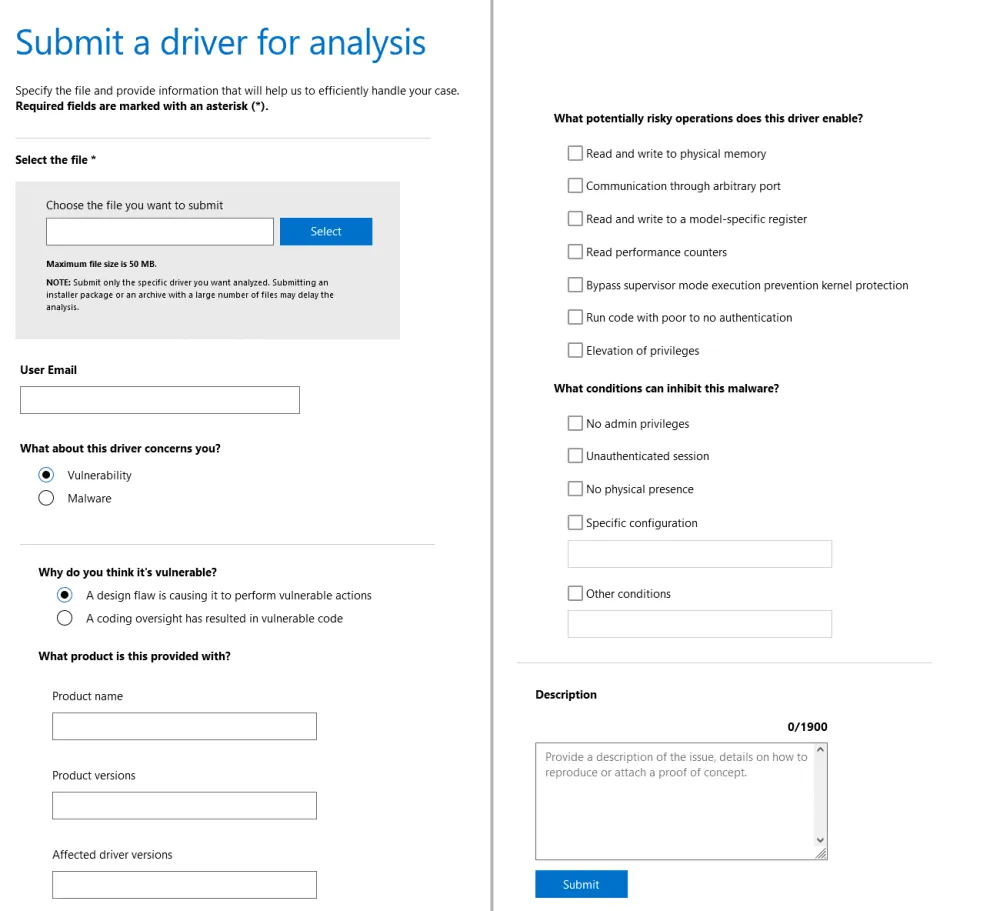
The new Vulnerable and Malicious Driver Reporting Center is basically a web form that allows users to upload a copy of a malicious driver, which gets uploaded and analyzed by a Microsoft automated scanner.
At a technical level, Microsoft says this automated scanner can identify techniques that are commonly abused by malicious drivers, such as:
- Drivers with the ability to map arbitrary kernel, physical, or device memory to user mode.
- Drivers with the ability to read or write arbitrary kernel, physical, or device memory, including Port I/O and central processing unit (CPU) registers from user mode.
- Drivers that provide access to storage that bypass Windows access control.
Positive scans are flagged and sent to a more in-depth investigation to one of Microsoft's security team members.
The OS maker said the center and its scanner can analyze drivers for both 32-bit and 64-bit architectures and encouraged users to report any driver they believe might contain malware or are benign but contain vulnerable code.
Malicious drivers will be blacklisted, while vulnerable drivers will be reported to their respective vendors.
Microsoft said it launched the portal because in recent years, drivers have been increasingly incorporated in the tooling of both nation-state and cybercrime gangs, including ransomware gangs.
In most cases, threat actors abuse vulnerabilities in old and unpatched drivers, or even intentionally downgrade and install older drivers, to gain admin privileges on a compromised host.
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.

