Microsoft finds Shrootless, a macOS bug that lets malware install rootkits
Apple has patched on Monday a vulnerability in the macOS Big Sur and Monterey operating systems that can be abused to bypass the SIP security feature and install kernel rootkits.
Described for the first time in a blog post published today by Jonathan Bar Or, a security researcher at Microsoft, the vulnerability is tracked under the CVE-2021-30892 identifier, but was also codenamed Shrootless.
According to Bar Or, the vulnerability resides in system_installd, the macOS software installation daemon.
"We found that the vulnerability lies in how Apple-signed packages with post-install scripts are installed," Bar Or said today.
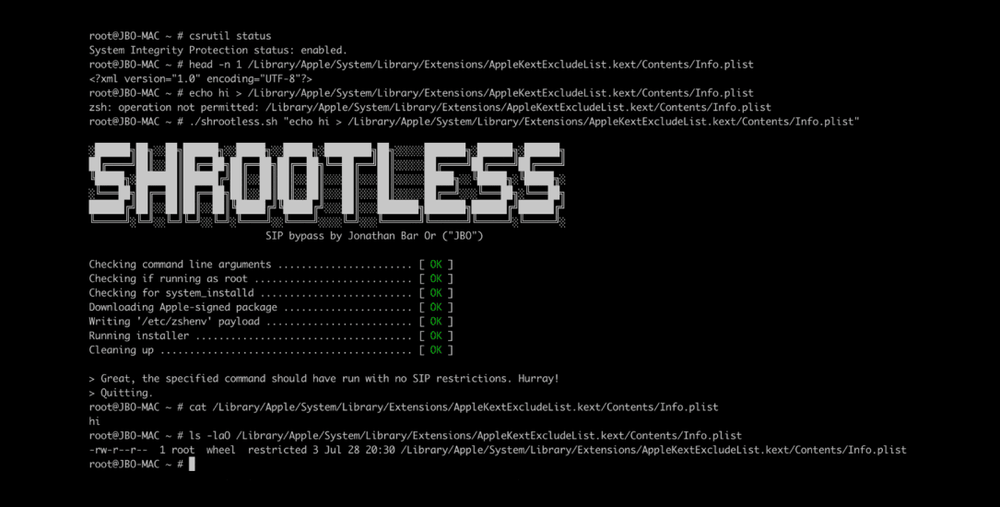
The researcher explained that during an app's installation routine, post-install scripts run inside a child process of the main installation daemon. This child process receives a special "entitlement" to deactivate the System Integrity Protection (SIP) security feature while the installation completes.
"If the package contains any post-install scripts, system_installd runs them by invoking a default shell, which is zsh on macOS," Bar Or added.
The Microsoft researcher said that by default, the macOS installation daemon looks for this shell at /etc/zshenv. As a result, Bar Or said that any attacker who can create a malicious /etc/zshenv file and then wait for system_installd to invoke zsh, can bypass SIP.
Since SIP is a technology that prevents macOS apps from changing protected folders and sensitive files—even from the root user itself—the Shrootless attack deactivates this super-powerful protection and effectively gives the attacker root access once again.
Bar Or said that Microsoft reported the Shrootless attack to Apple's security team earlier this year, together with a proof-of-concept that showed how the bug could be abused to install a malicious kernel extension (rootkit).
Apple patched the bug on Monday, with fixes shipped in macOS Big Sur 11.6.1 and macOS Monterey 12.0.1.
As Bar Or also pointed out, this is just the latest in a long list of SIP bypasses discovered in recent years [1, 2 , 3].
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.