Microsoft, Cloudflare disrupt RaccoonO365 credential stealing tool run by Nigerian national
Microsoft obtained a court order to seize 338 websites associated with a popular service called RaccoonO365 that was used by cybercriminals to steal usernames and passwords.
RaccoonO365 is a subscription phishing kit that allows cybercriminals to use Microsoft branding to create fake emails, attachments and websites that could lead victims into opening, clicking and downloading malicious links or documents.
The service was used by cybercriminals — who paid about $365 per month for a subscription — to target 9,000 email addresses each day and offered techniques to circumvent multi-factor authentication protections to steal user credentials and gain persistent access to victims’ systems.
In most cases the emails had attachments with links or a QR code that led to a page with a CAPTCHA. Once the CAPTCHA was entered, victims were taken to fake Microsoft O365 login pages that stole credentials.
Steven Masada, assistant general counsel with Microsoft’s Digital Crimes Unit (DCU), said RaccoonO365’s kits have been used to steal at least 5,000 Microsoft credentials in 94 countries.
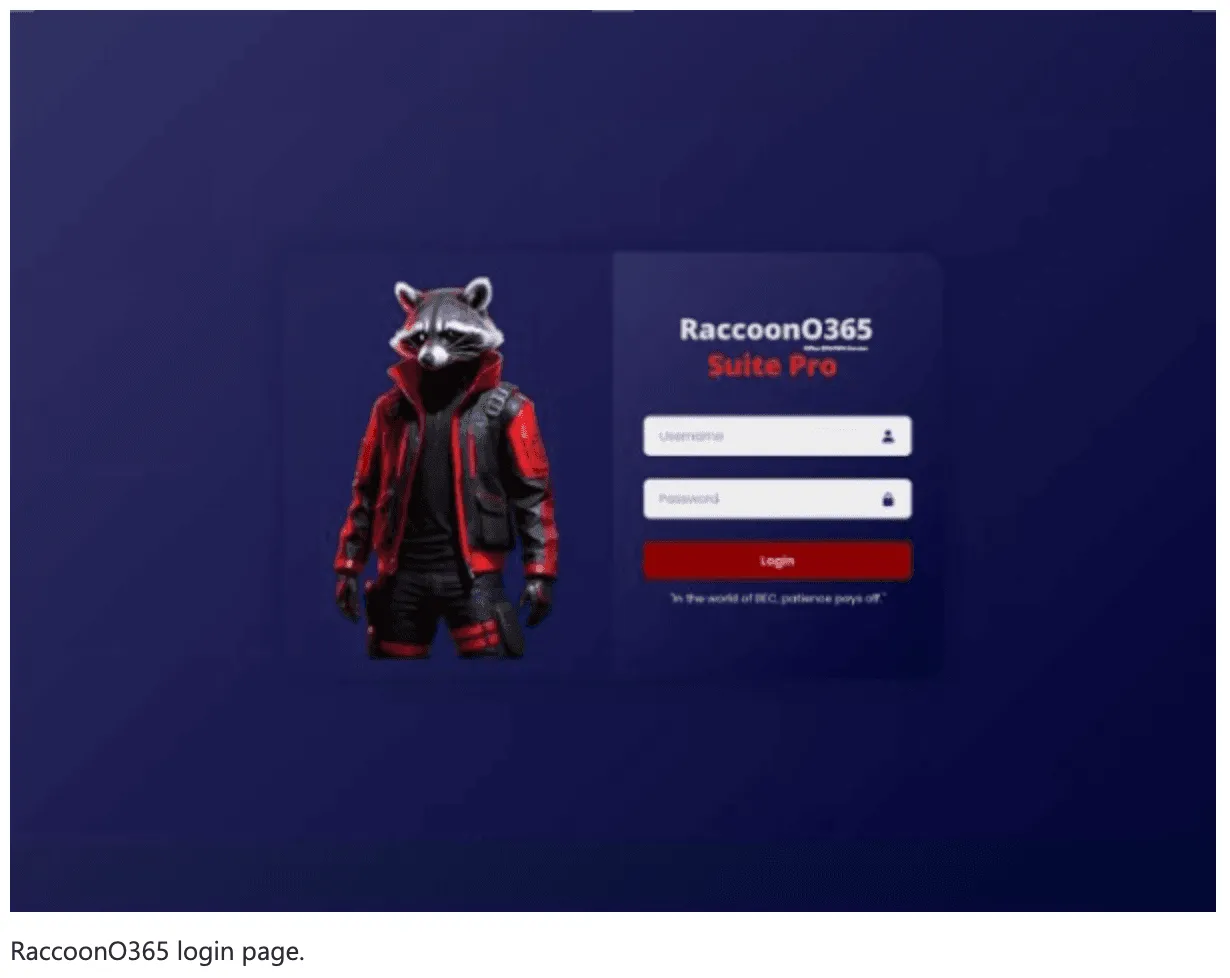
Image: Microsoft
For nearly one year, researchers at several companies have warned about the prevalence of RaccoonO365 and its increasing usage by cybercriminals to launch business email compromise attacks and more.
Masada warned that the development and scale of the RaccoonO365 shows “scams and threats are likely to multiply exponentially.” The actors behind it released updates to match demand and most recently rolled out an AI-backed service that would allow cybercriminals to scale up their campaigns.
Joshua Ogundipe
Masada noted that DCU identified Nigerian national Joshua Ogundipe as the leading force behind RaccoonO365. Ogundipe and others marketed and sold the tool on Telegram — with about 850 members of the group. The group is still active on Telegram as of Tuesday.
Microsoft found that the group behind RaccoonO365 has been paid at least $100,000 in cryptocurrency from about 100 subscriptions. This is likely only a portion of the money earned from the tool, according to Microsoft.
Microsoft officials said they believe Ogundipe wrote most of the RaccoonO365 code. They were able to uncover the operation after a secret cryptocurrency wallet was discovered.
“Ogundipe and his associates each have specialized roles within the cybercriminal organization, and together they develop, and sell the service, while providing customer support to help other cybercriminals steal information from Microsoft users,” Masada said.
“To mask their criminal enterprise and evade detection, they registered Internet domains using fictitious names and physical addresses that are purportedly located in multiple cities and countries.”
Microsoft sent a criminal referral to international law enforcement for Ogundipe. A Microsoft spokesperson declined to elaborate on whether Nigerian authorities have been notified of the campaign. A LinkedIn page allegedly tied to Ogundipe said he is based in Benin City.
Cloudflare claimed in its own blog to have seen evidence, like Russian letters in the Telegram group’s name, suggesting the group collaborated with Russian-speaking cybercriminals. Microsoft declined to confirm any Russian involvement, only writing that “both customers and victims of this service are from all over the world.”
Microsoft said it worked with Cloudflare to “swiftly seize and take down malicious infrastructure.”
In its own post-mortem on the operation, Cloudflare said the group behind RaccoonO365 “abused Cloudflare services and other infrastructure providers to try to prevent detection of their phishing kits.”
Cloudflare took down hundreds of domains and accounts associated with the group. Multiple phishing campaigns seen by Cloudflare officials spoofed brands like Adobe, Maersk, DocuSign and others.
Many of the file names were written to look like documents from finance or HR departments, contracts or invoices. Some documents had the victim’s name in the title to further entice them to click on it.
Cloudflare said while Microsoft seized hundreds of RaccoonO365 domains, it halted all RaccoonO365 operations on their own platforms and worked with U.S. law enforcement on other efforts.
Jonathan Greig
is a Breaking News Reporter at Recorded Future News. Jonathan has worked across the globe as a journalist since 2014. Before moving back to New York City, he worked for news outlets in South Africa, Jordan and Cambodia. He previously covered cybersecurity at ZDNet and TechRepublic.



