Microsoft and FireEye Detail New Malware Used by SolarWinds Hackers
Cybersecurity firms Microsoft and FireEye have published separate reports today detailing new malware strains they have linked to the threat actor that compromised software firm SolarWinds and its customers in a supply chain attack in 2020.
Three new malware strains have been discovered in total, per the Microsoft report. The FireEye report details only one malware family. The three are:
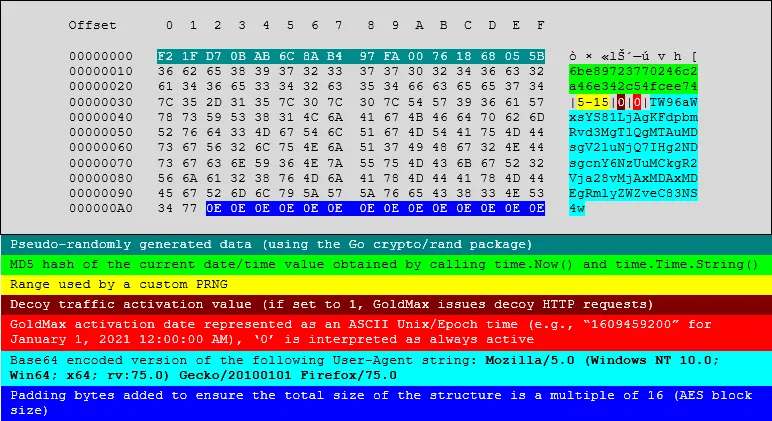
- GoldMax - a Go-based backdoor that attackers used to execute various commands on systems that have already been compromised before the malware was installed. This same malware is detailed in the FireEye report under the name of SUNSHUTTLE.
- Sibot - a VBScript malware strain designed for achieving boot persistence on infected hosts. Three different variants were discovered.
- GoldFinger - another Go-based malware strain. This one was used as an HTTP tracer tool that logs the route packets take to reach a hardcoded C2 server from an infected host.
These add to the previous malware strains used by the SolarWinds hackers, which include the likes of:
- Sunspot - the malware that hackers deployed inside SolarWinds' internal network to poison the Orion app build process.
- Solorigate (Sunburst) - the malware introduced in the SolarWinds Orion app updates between March and June 2020. The malware acted as a reconnaissance tool to help the threat actor identify companies they'd target later.
- Teardrop - the malware they deployed on selected networks via Sunburst, acting as a backdoor to execute other commands.
- Raindrop - another second-stage backdoor deployed on some networks instead of Teardrop.
The new malware was tailor-made for victim networks
As for the new discoveries today, Microsoft said it found the three malware strains on the networks of some of its customers that were compromised last year.
In some cases, the malware was planted as far back as June 2020, and in other instances, the malware was used as recently as September 2020.
In addition, the malware was also planted via different methods. Some customers were compromised via a tainted SolarWinds Orion app update, while others were infected with the same malware after the hackers obtained access to legitimate credentials to the company's internal network.
Either way, regardless of the initial access vector, Microsoft said the malware strains were linked to the same threat actor that compromised software company SolarWinds, which the OS maker formally named today for the first time using the codename of Nobelium.
"They are tailor-made for specific networks and are assessed to be introduced after the actor has gained access through compromised credentials or the SolarWinds binary and after moving laterally with TEARDROP and other hands-on-keyboard actions," Microsoft described the three malware strains today.
"These capabilities differ from previously known NOBELIUM tools and attack patterns, and reiterate the actor's sophistication," it added.
"In all stages of the attack, the actor demonstrated a deep knowledge of software tools, deployments, security software and systems common in networks, and techniques frequently used by incident response teams. This knowledge is reflected in the actor's operational decisions, from the choice of command-and-control (C2) infrastructure to the naming of scheduled tasks used to maintain persistence."
On January 5 this year, four US government agencies formally described the SolarWinds supply chain attack as "likely Russian in origin."
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.