Internal documents show Mexican army used spyware against civilians, set up secret military intelligence unit
Two digital rights groups, Mexico's R3D and the University of Toronto’s Citizen Lab, have just released an update to their “Ejército Espía” (“Spying Government”) report from late last year. In October 2022, they revealed that the Mexican army bought spyware and deployed it against at least two Mexican journalists and a human rights advocate between 2019 and 2021. While they had compelling circumstantial evidence, there was no smoking gun. The newly-released internal classified documents appear to prove it.
Luis Fernando Garcia, a lawyer and executive director of R3D, told Click Here in an interview that a roster of freedom of information requests and internal Ministry of Defense documents – released as part of last year’s massive hack-and-leak operation by the hacktivist group Guacamaya – connect officials at the highest levels of the Mexican army to the purchase of Pegasus spyware. R3D found a 2019 acceptance letter that links the military to a company with the exclusive right to sell licenses for the NSO Group’s Pegasus spyware in Mexico.
NSO Group created Pegasus in 2011 and it has been linked to everything from the capture of the drug lord El Chapo to the murder of journalist Jamal Khashoggi. Pegasus’ super power is its ability to infect smartphones without a user knowing — the phone becomes a spy in their pocket, capturing their location, their communications, and information on their friends.
Among the new revelations are documents from the Mexican Secretariat of National Defense , or SEDENA, that discuss a previously unknown military intelligence agency in charge of the nation’s surveillance programs. The leaked files show the agency, referred to as CMI or the Military Intelligence Center, spied on a human rights advocate named Raymundo Ramos who has been investigating a suspected extrajudicial killing by the Army that occurred in July 2020 in a border town called Nuevo Laredo.
The interview has been edited for space and clarity. A fuller version of the story can be heard on the Click Here podcast.
CLICK HERE: For people who don’t know, can you explain the mission of R3D (The Digital Rights Defense Network)?
LUIS FERNANDO GARCIA: The Digital Rights Defense Network is a NGO that works on issues related to human rights and technology. Since the beginning we've been working to uncover and to investigate and pushback against the surveillance apparatus in Mexico.
CH: You started your latest investigation into government surveillance in collaboration with the University of Toronto’s Citizen Lab in early 2022. What did the initial investigation [published last October] reveal?
LG: We started checking phones of human rights defenders, journalists, trying to see if we could find forensic evidence of Pegasus in Mexico. We started to document cases of people who were infected in 2019, 2020, and 2021, which means [it was deployed] during the current government, not the previous government.
A week or maybe less from our publication date, something really important happened. The army's email system was hacked and an activist group called Guacamaya was offering access to those emails to media organizations and to human rights organizations. And this gave us like the missing key that we needed to actually point the finger at the army and say we found these Pegasus cases [and connected them to the military].
CH: Can you talk about some of the specific things you discovered in the Guacamaya documents?
LG: We were able to find a kind of acceptance letter from the army, directed to the secretary, which is the head of the army — the General Secretary of National Defense in Mexico. And here it talks about a contract with Comercializadora Antsua, the same company that we already had a strong suspicion was the intermediary company that was being used by NSO Group to commercialize Pegasus in Mexico. This was proof that the contract existed and the head of the army knew about it because this was a document created for the head of the army.

CH: And did you ever have any concerns that this might be a set-up or that the documents might be fake?
LG: Not at all. The president himself [Andrés Manuel López Obrador] has said that the hack happened, that the documents are real, and we have verified some of the documents ourselves. We found an email directed to the Secretary of the Army and we asked about that email through legal means, through an access information request, and they gave us the same email. And it hasn’t been disputed by the government or the Army that the documents [in the hack] are fake.
CH: You’d been working on surveillance issues in Mexico for years, so how did this new information help with your research?
LG: Now we have the number of the contract, the date of the contract, the amount paid for the contract — around 140 million pesos – so that solidifies our belief that the army was actively trying to hide the information related to this and lying to different authorities. [R3D had been requesting this document and they were told it didn’t exist.]
CH: Did you find anything in the documents that was surprising or presented new information entirely?
LG: Yes. We didn't know about [a military intelligence unit called] CMI. If you Google CMI, you are not going to find much of anything. The objective of the CMI, the document says, is to give to the intelligence arm of the chief of staff intelligence products generated from information obtained through closed systems. In other words, it is not open source intelligence – they are talking about communications intercepts. Legally they don't have any powers to do interception of communications of civilians at any point.
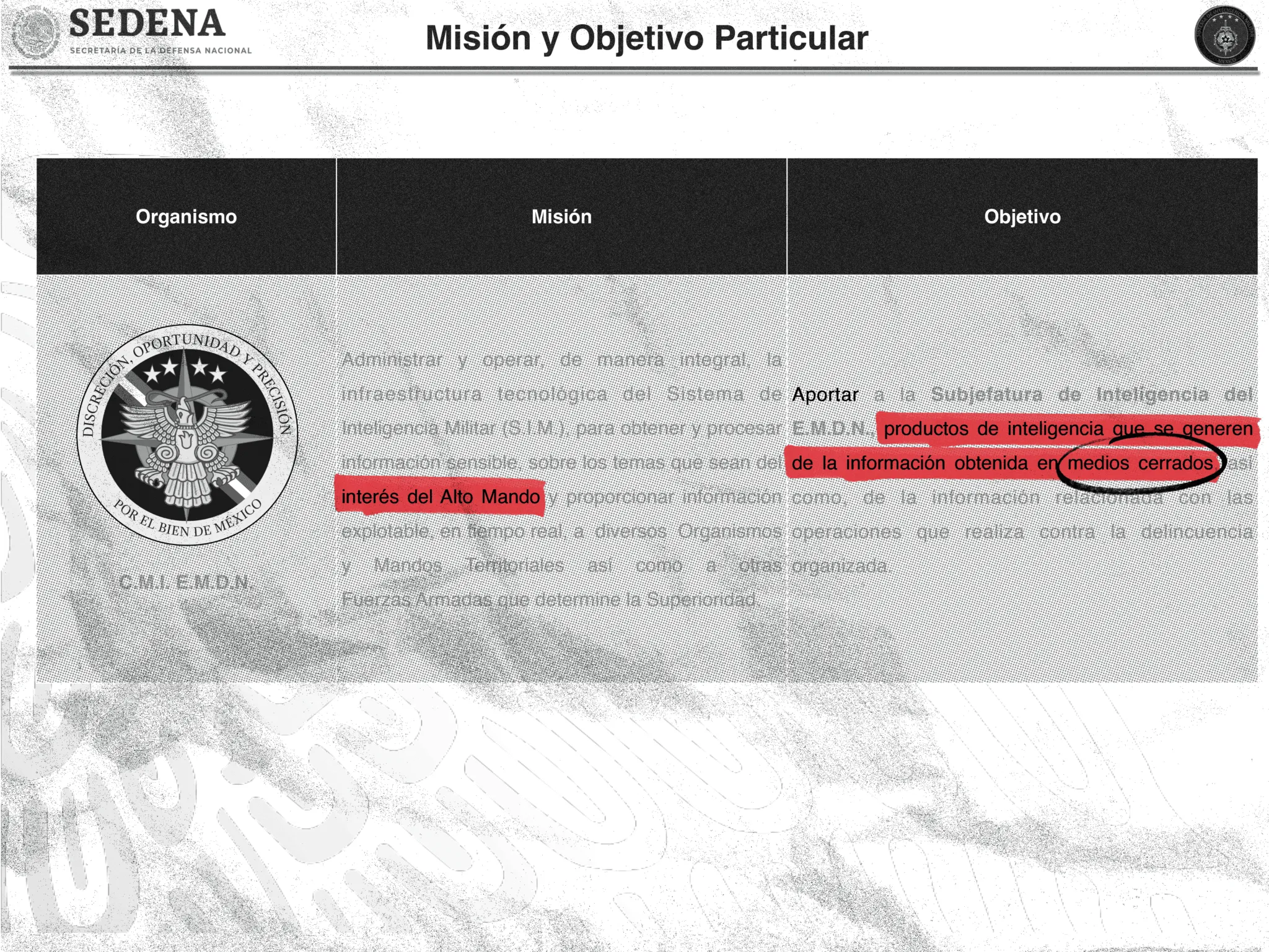
What’s more, I looked and I couldn’t find any formal, legal establishment of this institution. We did find a document that lays out an analysis of CMI’s strengths, opportunities, weaknesses, and threats. One of the threats that they specifically identify is that the activities of this [CMI] center are made public. That’s one of the main threats that they identify — that the people know that CMI exists and what it does.
CH: Meaning they don't want people to know they exist or what they do…
LG: Exactly.
CH: You found specific surveillance information on a human rights advocate named Raymundo Ramos, tell us about that?
LG: [One of the documents talks] about communications between Raymundo Ramos and journalists around the time a controversial video was released that seemed to capture an extrajudicial killing by the military in [the border town] of Nuevo Laredo.
Ramos was investigating the shooting. All his conversations with journalists at that time were on encrypted apps, so the only way they could have captured the conversations was with something like Pegasus. Espionage carried out by the Military Intelligence Center is absolutely illegal since the Army lacks the legal authority to intervene in the private communications of civilians.
The document also suggests that the military has secret information that shows Ramos had a relationship with the cartel in Nuevo Laredo. They have never proved anything, and they have never charged him of being involved with the cartels at any point.

But they repeat this accusation and in the document it says that this intelligence product is being given in a confidential manner to the military prosecutor police. So it's considered as an element of judgment in this investigation.
**CH: So connect the dots for us, why is it so important to see Ramos mentioned here? **
LG: So we determined last year [with the technical help of Citizen Lab] that Ramos’ phone was infected with Pegasus. This document proves that it was the army who was spying on him because they wanted to find out his connection or alleged involvement in the publication of the Nuevo Laredo shooting video that was creating such a headache for the army.
CH: Some people say the Guacamaya leaks were huge but haven't had the impact that some people had hoped for. Does today’s news change that?
LG: I think those assessments are premature. I think the volume of information is so great, it has posed technological challenges to those who might try to sort through the documents. It's not easy to find this information. It's not just control-f search, and you get all these results. You need to do a lot of methodic work and be strategic about what you look for and how.
And it's not only about information that comes from Guacamaya. You need to complement it with your own investigations. And here we have documents that we have obtained through freedom of information requests, forensic analysis that's been done with the help of Citizen Lab. There’s a lot of legwork above and beyond the Guacamaya leaks that are part of this story. I don't think I'm the only one. I think there's a lot of people who are taking their time.
Dina Temple-Raston
is the Host and Managing Editor of the Click Here podcast as well as a senior correspondent at Recorded Future News. She previously served on NPR’s Investigations team focusing on breaking news stories and national security, technology, and social justice and hosted and created the award-winning Audible Podcast “What Were You Thinking.”
Will Jarvis
is a podcast producer for the Click Here podcast. Before joining Recorded Future News, he produced podcasts and worked on national news magazines at National Public Radio, including Weekend Edition, All Things Considered, The National Conversation and Pop Culture Happy Hour. His work has also been published in The Chronicle of Higher Education, Ad Age and ESPN.




