Malware uses underground call centers to trick users into infecting themselves
The operators of the BazarLoader malware are working together with underground call centers to trick the victims of their spam campaigns into opening malicious Office documents and infecting themselves with malware.
While this is not the first time when cybercrime gangs have worked together with underground call centers, this is the first time when we see a major malware distributor, such as the BazarLoader gang, use this tactic on a large scale.
The attacks are so strange and different from anything else seen on the malware scene today that they have their own name and are usually referred to as BazarCall or BazaCall, due to the fact they rely on a phone call to finish the infection process.
How a BazarCall attack works
Currently, these attacks follow a simple yet very effective pattern. It all starts with the BazarLoader gang sending out email spam campaigns to selected victims.
To get the targets' attention, the emails usually use lures related to offers, free trials, or subscriptions to medical, IT, or other financial services. The emails also contain instructions for recipients to call a phone number for additional details about their offer.
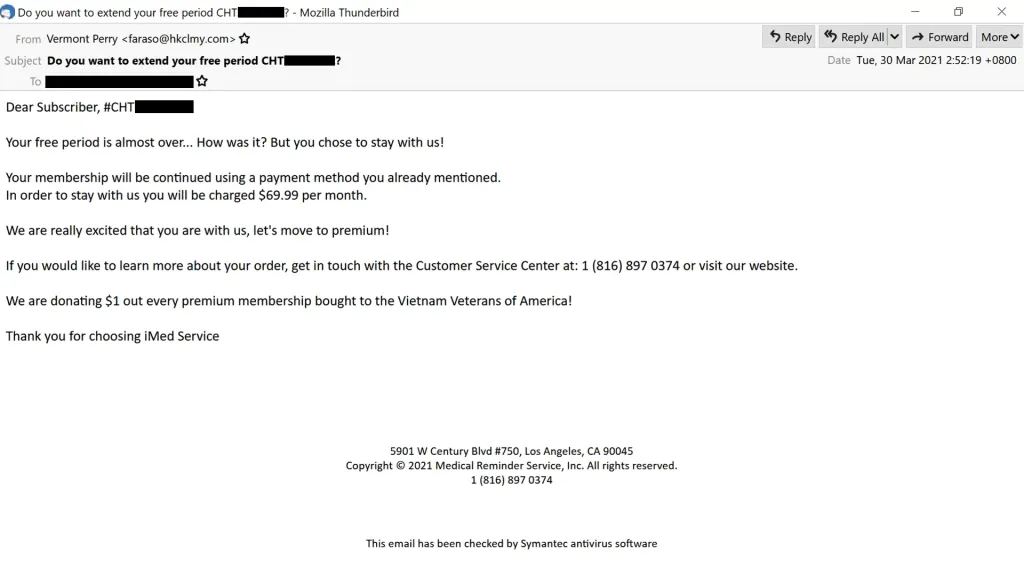
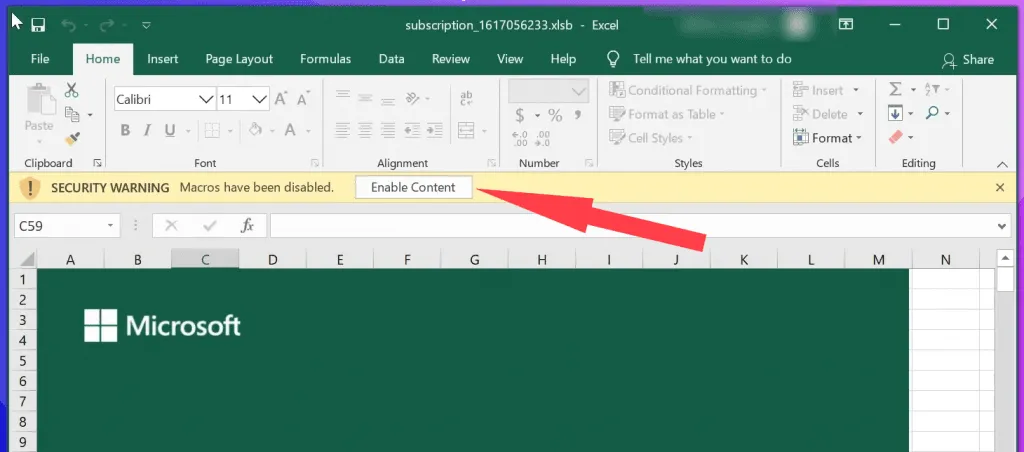
If users call the number, they are connected to a call center where an English-speaking operator guides the victim through downloading an Office file, disabling Office security features and allowing the document, usually an Excel or Word file, to run automated scripts called "macros," which download and infect the target's computer with malware.
A recorded phone call to one of these call centers involved in the BazarCall scheme is also available below, courtesy of security researcher Brad Duncan.
BazarCall attacks target high-profile targets
In an interview with The Record today, a malware researcher going on Twitter as TheAnalyst, said BazarCall spam campaigns have been taking place since January 2021.
The Analyst, who is also the person who coined the BazarCall term, told The Record that most of these spam campaigns target users with corporate or .edu email addresses and almost never go after home users that use freemail services like Gmail, Hotmail, or Yahoo.
I'm dubbing the recent #BazaLoader #BazarLoader campaigns involving social engineering and call centers as #BazarCall
— TheAnalyst (@ffforward) February 2, 2021
Next one up: "TopTips Office" xls dl domains:
/ttoffice.us
/toptoffice.us
/tt-office.us
/toptipsoffice.us
/ttoffices.us
cc @James_inthe_box @JAMESWT_MHT @jfslowik pic.twitter.com/M02Tzr8eQe
The security researcher says the classic endgame for these attacks is to infect corporate networks, where the BazarLoader malware can then turn around and rent access to ransomware gangs, such as the Ryuk crew, with which they've collaborated before [1, 2, 3].
Furthermore, TheAnalyst also told The Record that some of the malicious documents seen in BazarCall call center schemes have also been seen installing the TrickBot trojan instead of BazarLoader.
However, this is no surprise, as it is generally believed that the BazarLoader malware was created by the same group behind the TrickBot malware.
TheAnalyst says that any security researcher interested in following this campaign's evolution can follow the #BazarCall and #BazaCall Twitter hashtags, which several security researchers use today to share indicators of compromise (IOCs) related to these attacks.
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.



