Malware campaign targets server hosting software CWP
A sophisticated threat actor is targeting web hosting software in order to install backdoors and drop rootkits on Linux servers.
The attacks have targeted Control Web Panel (formerly known as CentOS Web Panel), a type of software similar to the more famous cPanel, used by web hosting companies and large enterprises to host and manage large server infrastructure.
Since at least February this year, a threat actor has been scanning the internet for CWP installations and using an exploit for an old vulnerability to gain access to the CWP admin interface and install a backdoor named Facefish.
This malware's primary functions allow it to gather device information, execute arbitrary commands, and steal SSH credentials from the infected host.
The attacks, spotted by both Juniper and Qihoo 360's Netlab, have also involved a rare rootkit component that the attacker dropped on hacked Linux servers in order to maintain persistence.
More than 185,000 CWP installations available online
But despite the months of attacks, both companies said they'd seen little activity on the hacked servers.
A big surprise was that the threat actor did not deploy a crypto-mining component, which most botnets tend to do these days.
In its report, Juniper floated the idea that the Facefish attacker was merely building a botnet and that they most likely intended to sell or rent access to the compromised systems to the highest bidders.
Since CWP is usually deployed to prop up some pretty large and important server networks, access to any of these systems would be of high value to the likes of ransomware gangs.
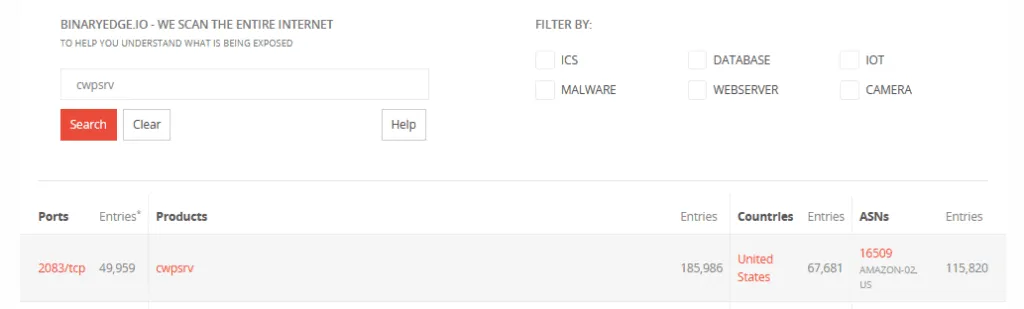
A search with the BinaryEdge engine shows there are currently more than 185,000 CWP installations running across the internet, although it is unclear how many of these systems are unpatched and vulnerable.
Neither Juniper nor Netlab published a CVE identifier for the bug exploited by the attacker. It is unclear if the bug even has a CVE. However, both their blogs list the actual exploit code, which IT teams can analyze and set up firewall rules to block incoming exploitation attempts.
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.



