Malware author made $560,000 just from a simple clipboard hijacker
A recent report published by antivirus maker Avast reveals how even a low-effort malware distribution campaign has managed to rack up more than half of a million US dollars worth of cryptocurrency from victims since November 2018.
The entire operation is ridiculously simple and consists of a threat actor publishing malware-laced "hacking tools" on a Telegram channel.
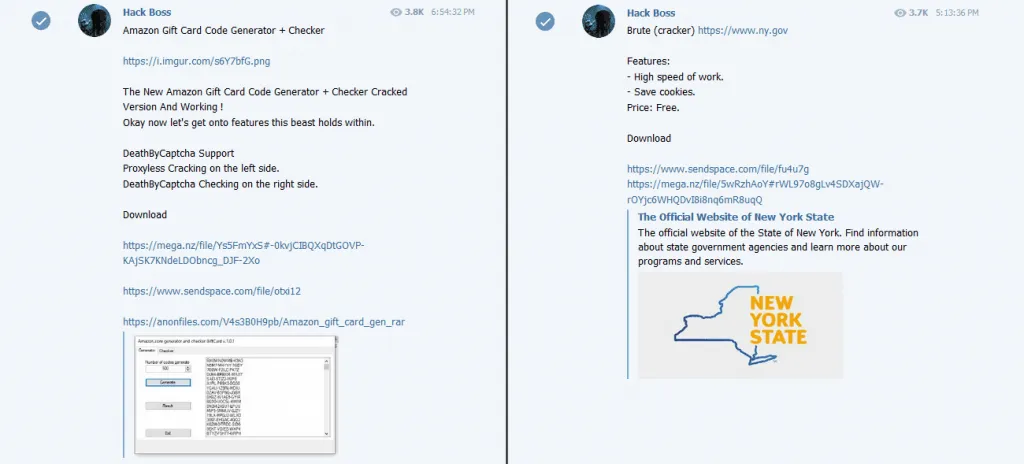
Anyone who downloads and installs the tools will get their Windows computers infected with a clipboard hijacker, a type of malware that constantly watches a computer's clipboard—the location where content is copied during copy/cut-paste operations.
In this case, the malware was configured to search for text strings in the format of known cryptocurrency addresses and replace the user's copied text with the attacker's chosen address.
The end goal was that the malware would replace cryptocurrency addresses when infected users would make transactions, and the victim would unwittingly send funds to the malware's author.
In a technical report published last week, Avast said the malware came preconfigured with more than 100 cryptocurrency addresses which it would swap out as needed.
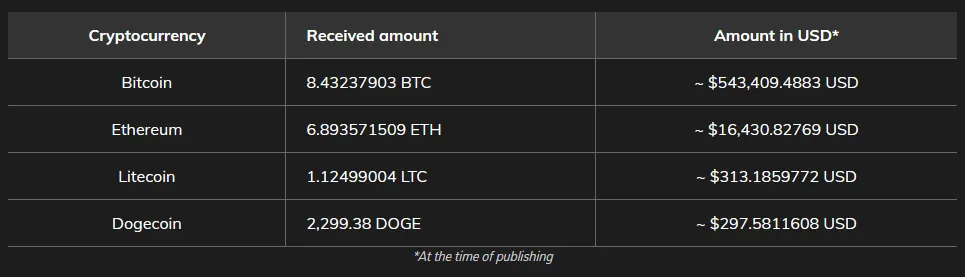
The technique appears to have worked like a charm and netted the Telegram channel owner, going by the name of Hack Boss, at least $560,000 worth of cryptocurrency, such as Bitcoin, Litecoin, Dogecoin, and Ethereum.
However, since the malware also substituted Monero addresses, Avast believes the threat actor's earnings might be even larger than this. (You currently can't check the balance of Monero wallets.)
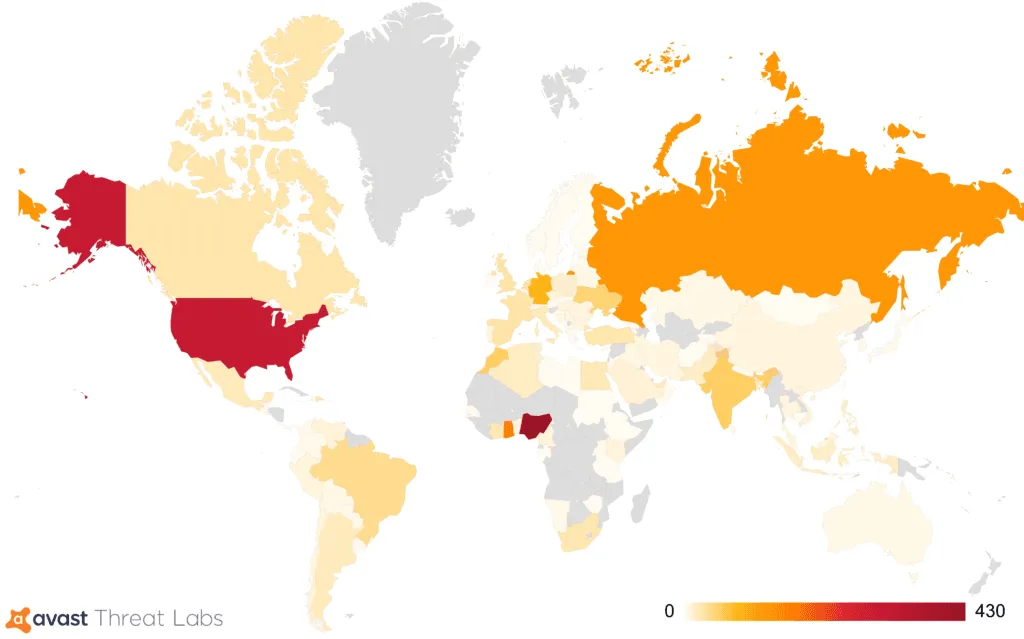
The security firm said that based on its detections, the Hack Boss malware infected users all over the world, with most victims located in Nigeria, the US, Russia, and India, which are also some of today's biggest cybercrime hotspots, and where wannabe cybercriminals would be easily lured on the Hack Boss Telegram channel for some "goodies."
Detection is crucial even if Hack Boss targeted wannabe hackers
In the cybersecurity field, clipboard hijackers are usually considered a low threat since these types of malware strains are usually focused on a very specific attack. However, it is always good to keep in mind that malware can be easily updated over the air to include additional functionality or even download other secondary payloads.
In the case reported by Avast, nobody's losing any sleep because of this threat, as it targeted wannabe criminals, but this doesn't mean the malware won't be wrapped in another social engineering lure later down the line and used against other user categories.
Because of this, detecting this threat is crucial for every security vendor. Avast has released indicators of compromise (IOCs) related to this malware campaign on GitHub.
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.



