Majority of DOD cyber incident reports are incomplete, GAO finds
Failures in reporting cyber incidents at the U.S. Department of Defense risks leaving commanders in the dark about the effects hackers could have on their missions, according to a new report by the Government Accountability Office.
While external information sharing around the Russian invasion of Ukraine has won the DOD and broader U.S. security and intelligence community plaudits, the lack of internal information sharing within the DOD and the defense industry is leading to “lost opportunities to identify system threats and improve system weaknesses.”
The 70-page report published on Monday warns that hackers are continuing to target the DOD itself alongside the U.S. defense industrial base.
“Until DOD assigns responsibility for ensuring complete and updated incident reporting and proper leadership notification, the department will not have assurance that its leadership has an accurate picture of its posture,” the report warns. “As a result, the department may miss opportunities to assess threats and weaknesses, gather intelligence, support commanders, and share information.”
All cyber incidents affecting the DOD are required to be reported as a ticket into a central repository known as JIMS (the Joint Incident Management System) within 6 to 24 hours of discovery, and then to be updated afterwards as more information comes to light, although the report states this rarely happened.
Critical cyber incidents — incidents “related to enemy activity, potential enemy activity, or anomalous activity on the department’s information networks” — also require significant activity reports (SIGACTs) to notify commanders at all levels.
“However, DOD has not fully implemented either of these processes,” stated the GAO report, which gave as examples of critical incidents “DODIN (Department of Defense Information Network) outages or degradations, escalation of privileges, data exfiltration, and evidence of malware.”
Problem by design?
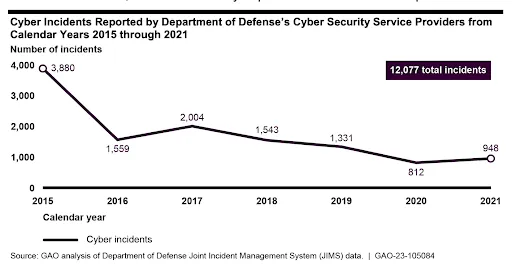
While the total number of incidents themselves are trending downwards — with 948 reported in 2021 compared to 3,880 in 2015 — the GAO report found "weaknesses" in how these incidents were reported.
The DOD's cyber incident reporting system “often contained incomplete information,” according to the report, and the department “could not always demonstrate that they had notified appropriate leadership of relevant critical incidents.”
According to the GAO report, 91% of JIMS cyber incident reports submitted between 2015 and 2021 “did not include information on the discovery date of the incident, hindering DOD’s ability to determine whether incidents were reported in JIMS in a timely manner.”
It added that 68% percent of the reports “did not include information on an incident’s delivery vector, limiting DOD’s ability to identify trends in the prevalence of various threats affecting its networks.”
Partially these issues are caused by the design of JIMS. While the DOD's official Cyber Incident Handling Program Manual requires 46 different data fields for reporting a cyber incident, JIMS only requires users to include information on 13 of the 46 fields –with the other data fields either presented as optional (such as operational impact and system weaknesses) or unavailable (such as root cause(s) and systems affected) in the system.
DOD officials "acknowledged that JIMS has limitations" according to the GAO report and "are considering implementing a new solution to address those limitations."
Alexander Martin
is the UK Editor for Recorded Future News. He was previously a technology reporter for Sky News and a fellow at the European Cyber Conflict Research Initiative, now Virtual Routes. He can be reached securely using Signal on: AlexanderMartin.79



