LV ransomware gang hijacks REvil's binary
In what can be described as a case of piracy among cybercrime gangs, the LV ransomware gang appears to have hijacked and modified the binary payload of the more infamous REvil group.
According to security researchers from Secureworks, the LV gang seems to have gotten its hands on the binary file that performs the actual encryption on infected networks during a REvil attack.
Researchers say the LV gang appears to have used a hex editor to modify this binary and its configuration file.
The result of their modifications is a REvil ransomware variant that security firms have been detecting since the start of the year as the LV ransomware.
In a report published on Tuesday, Secureworks says the connections between LV and the original REvil binary were obvious when they analyzed the LV code in greater detail.
For example, the LV strain even contains leftovers of a REvil code block where the REvil gang had insulted two prominent malware analysts.
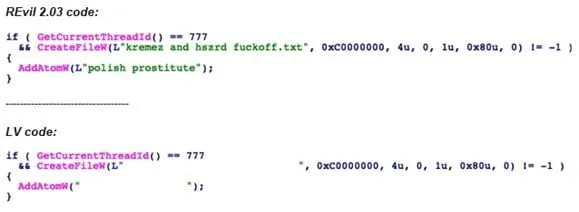
Based on this and other connections they found, Secureworks said the LV gang appears to have modified a REvil v2.03 beta version, which eventually became the official LV ransomware.
However, despite their blatant copy-paste job that allowed them to gain access to a top-tier ransomware payload with almost zero development costs, Secureworks said the LV gang is not on par with the REvil gang in terms of its backend infrastructure.
For example, the LV gang removed command and control (C&C) servers that the REvil gang was using to track infections. However, rather than replace them with their own servers, the LV gang left this section empty.
Secureworks says this suggests that the LV group "may not be capable of maintaining C2 infrastructure or developing the backend automation required to process and track victims' data."
This theory was also reinforced after Secureworks analysts discovered that the dark web portals where LV victims were told to go pay their ransoms were often down or returning errors when victims and analysts tried to access them.
Secureworks believes this may indicate that the LV gang is "struggling to maintain resilient infrastructure due to lack of skill or insufficient resources."
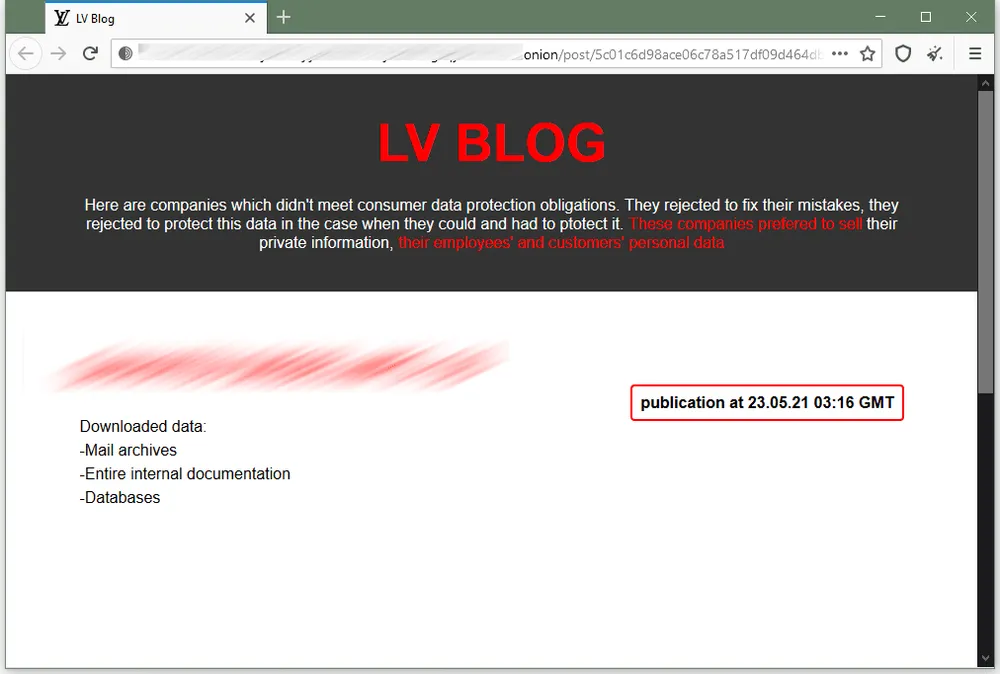
In addition, the LV gang also tried to mimic the REvil gang by setting up "leak sites" on the dark web, where they threaten victims to leak their data if they do not pay.
However, Secureworks said they noticed something strange because the group never leaked data for any victims they listed on their leak portal. This suggests that the group might not have the storage capability to store data stolen from their victims.
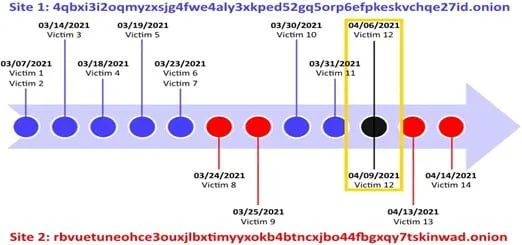
Furthermore, Secureworks also noticed that the LV gang also ran two separate but identical leak sites in the first half of 2021, each listing different victims, with the exception of one entry. The reasoning for this remains unclear.
Prior to hacking forums enforcing a ban on ransomware ads, the LV gang was never seen advertising their ransomware to other groups, but Secureworks says it has recently spotted different partner and campaign IDs in LV configuration files, suggesting the gang is either already collaborating with other cybercrime gangs or is at least preparing to launch a ransomware-as-a-service (RaaS) offering in the near future.
As for the REvil gang, Secureworks believes that the RV pirating incident might lead the group to improve its code complexity and security in order to prevent such modifications of its configuration files for future binaries, something that will also make the life of security analysts much harder at the same time.
How long the LV operation will survive remains unclear, but Secureworks said that while the group does not yet have access to large resources to run a ransomware operation at scale, they, at least, have the technical skills, based on their pretty complext job of hijacking the REvil payload binary.
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.