LockBit adds a bug bounty program in its revamped ransomware-as-a-service operation
The highly active LockBit ransomware group released what it is calling “LockBit 3.0” over the weekend, and announced a bug bounty program that offers rewards for ways to improve the ransomware operation.
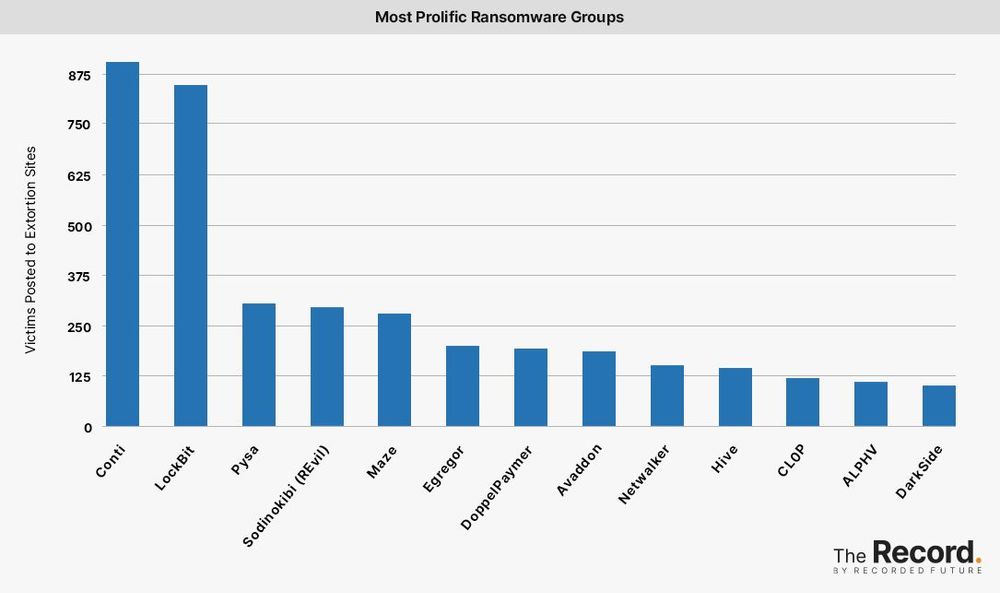
Cybersecurity researchers have tracked a surge in LockBit activity over the last several months, and the group is poised to overtake Conti as the most prolific ransomware group in terms of publicly identified victims. Recent incidents attributed to the group include attacks on a Foxconn factory, a Canadian fighter jet training company, and a popular German library service.
Although few details were provided about technical changes to the ransomware-as-a-service operation, the group said it was inviting all security researchers and hackers to participate in its bug bounty program, which allegedly offers rewards ranging from $1,000 to $1 million. The group is seeking website bugs, locker errors, and ideas to improve the group’s software, among other things. A $1 million bounty is reserved for discovering the true name of the affiliate program manager, known as LockBitSupp.
Lockbit ransomware group announced today Lockbit 3.0 is officially released with the message: "Make Ransomware Great Again!"
— vx-underground (@vxunderground) June 26, 2022
Additionally, Lockbit has launched their own Bug Bounty program paying for PII on high-profile individuals, web security exploits, and more... pic.twitter.com/ByNFdWe4Ys
Several cybersecurity researchers dismissed the effectiveness of LockBit’s bug bounty program.
“Since Lockbit 3.0's bug bounty program essentially invites people to add a felony in exchange for a reward, they may end up finding that the $1,000 low reward is a little light given the risks involved for those who might decide to help them,” said Casey Ellis, founder and chief technology officer at Bugcrowd, which operates a popular crowdsourced bug bounty platform.
“I doubt they will get many takers. I know that if I find a vulnerability, I’m using it to put them in prison,” said John Bambenek, principal threat hunter at cybersecurity firm Netenrich. “If a criminal finds one, it’ll be to steal from them because there is no honor among ransomware operators.”
However, the establishment of a bug bounty program highlights how ransomware groups operate with impunity, and in some cases have grown to resemble professional businesses.
“They have taken a page straight from a mature organization’s development playbook,” said Mike Parkin, senior technical engineer at Vulcan Cyber. “If it works for a major player like Microsoft, Google, or Apple, why wouldn’t it work for a criminal gang if they have both the maturity and the resources to do it?”
“Malware gangs have reached a level of maturity that they are, literally, professionally run businesses,” Parkin added. “They've caught up with ‘conventional’ organized crime syndicates at this point, and it's going to take an international effort to stop them.”
Researchers have linked more than 850 attacks to LockBit since the group began its operation in 2019. The group was considered a marginal player until it launched LockBit 2.0, a new version of its ransomware-as-a-service platform, in 2021.
In addition to the bug bounty program, LockBit 3.0 also introduces Zcash as a payment option for its ransomware victims. The cryptocurrency, which is based on Bitcoin’s codebase, provides enhanced privacy for its users — making it a logical choice for cybercriminals.
Additional reporting provided by Jonathan Greig.
Adam Janofsky
is the founding editor-in-chief of The Record from Recorded Future News. He previously was the cybersecurity and privacy reporter for Protocol, and prior to that covered cybersecurity, AI, and other emerging technology for The Wall Street Journal.