Conti leaks data stolen during January attack on Oregon county
The Conti ransomware gang has published all of the data it stole during a January attack on the government servers of Linn County, Oregon.
The group — which appears to be reorganizing itself, according to cybersecurity experts — released nearly 1,500 documents Wednesday. Linn County officials said they chose not to pay a ransom after realizing that they had backups and determining that the data was not particularly sensitive.
Darrin Lane, administrative officer for Linn County, told The Record that the attack began on the morning of Jan. 24 and that the county's IT team immediately began shutting down systems in order to limit the damage.
The move was successful, and the county eventually realized that the attack was limited to two active directory domains. The attack brought down the government's website, but several departments and offices were not affected, including the Sheriff's Department or the Health Services Department.
“The attack did impact our Road Department servers and we did receive information from the attackers that they had downloaded data from a Road Department server. We were provided with what appeared to be a directory listing of the server and that enabled us to understand what data was taken,” Lane said.
Located between the cities of Eugene and Salem, the county has about 130,000 residents. Lane said the government worked with a consultant and its insurance company to figure out what happened and how to block any additional attacks. The county did not say how much the ransom demand was.
"Fortunately, we had robust backups of all affected servers and datasets," Lane said. "No data of any consequence was lost and all systems were back up and running by the end of the week with most back within three days."
After a consultant spoke with Conti actors, the county decided against paying the ransom because much of what was stolen was not sensitive data and “would likely be considered public records under Oregon Law," Lane said.
Because the county had backups, there was no need to decrypt any data, making the decision even easier. As a precaution, the county notified the FBI and the Cybersecurity and Infrastructure Security Agency, Lane said.
When provided with a sample of the documents leaked on Wednesday, Lane said it was a copy of a document that is public record and is subject to release to anyone who requests it.
“Having the benefit of several months to consider the impacts of the ransomware attack, I feel good about how we responded. Of course, we are angry about being targeted but it’s clearly not personal,” Lane said.
The county's cybersecurity is now stronger than before the attack, Lane said.
“All that being said, we understand that this is never really over, we all must continue to learn and employ appropriate systems and processes to protect our information technology infrastructure,” Lane noted.
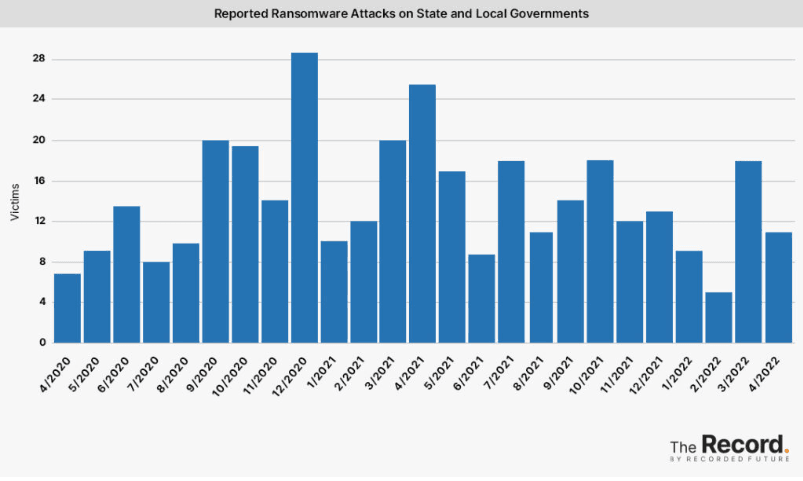
Emsisoft threat analyst Brett Callow noted that Linn County is the 17th U.S. local government to be hit by ransomware so far this year.
“While it’s hard to see that as a win, it’s nonetheless a big improvement on the 36 governments which had been hit by the end of May last year,” Callow said.
Last week, cybersecurity researchers with AdvIntel said the Conti gang officially took much of its infrastructure offline.
The analysts said key features were missing from Conti’s leak site and much of its ransom-negotiating infrastructure was either shut down or “going through a massive reset.”
But the group has still been active, leaking stolen data and still conducting negotiations with victims.
Conti is still in the middle of executing a high-profile attack on the government of Costa Rica, and Callow shared screenshots of ongoing victim negotiations with the group.
“If they were shutting down, you’d think they’d be pushing to close. The extent to which Conti is still operating is not clear. At this point, they may well simply be winding up and attempting to monetize old attacks,” Callow said. “Given previous events, it’s hard to see that the Conti brand has a future.”
Recorded Future ransomware expert Allan Liska echoed those remarks, explaining that the Linn County release is most likely part of the group’s “going out of business, so everything must go” strategy.
“I think we may see some more dumps from older attacks in the next few weeks as Conti continues to restructure,” Liska said.
Jonathan Greig
is a Breaking News Reporter at Recorded Future News. Jonathan has worked across the globe as a journalist since 2014. Before moving back to New York City, he worked for news outlets in South Africa, Jordan and Cambodia. He previously covered cybersecurity at ZDNet and TechRepublic.



