LinkedIn denies 500 million user data breach
LinkedIn has formally denied a rumor that it suffered a devastating security breach that exposed the account details of more than 500 million of its registered users.
Rumors of a breach appeared last week after a threat actor claimed to have been in possession of a large trove of LinkedIn user data and proceeded to leak a sample of two million user records as proof.
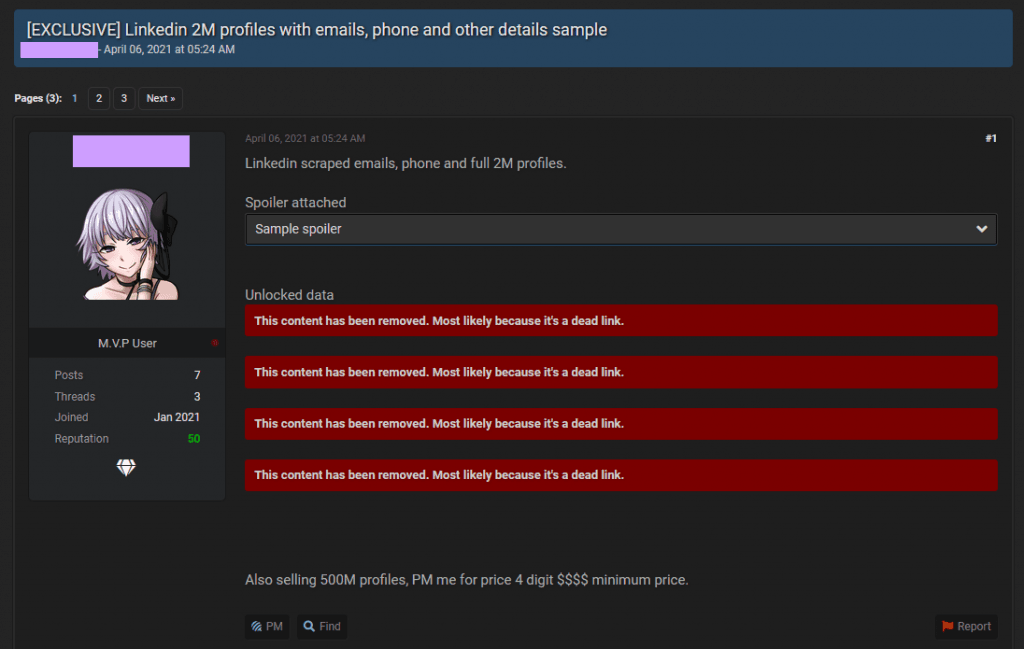
But in a message published last week, LinkedIn said it investigated the breach and concluded that the hacker's data only included public information that was scraped off LinkedIn's website and which users consciously made public on their profiles.
"This was not a LinkedIn data breach, and no private member account data from LinkedIn was included in what we've been able to review," a LinkedIn spokesperson said.
"Leaking" public data is not a data breach
The Record also investigated this so-called "leak" when the forum thread was initially posted last week. We came to the same conclusion as the LinkedIn security team — namely that the data consisted only of publicly viewable profile information.
However, numerous other news outlets did not go through the same process. Tens of publications, including some large news agencies, picked up the story and ran with it without verifying the validity of the leaker's claims, all in a rush to be on top of the news cycle and get eyeballs on their articles.
Sadly, the same news outlets caused undue damage to a second company days later when they also published strongly-worded articles claiming that audio conversations app Clubhouse also got hacked.
In reality, the LinkedIn scenario repeated once again.
A threat actor scraped publicly visible Clubhouse profiles, shared the data on a hacking forum claiming to have hacked the site, and several news outlets ran the hacker's claims as unquestionable truth without doing any kind of due diligence.
This is not a leak. Clubhouse itself says here “the data referred to is all public…which anyone can access”.
— Tarah M. Wheeler ([email protected]) (@tarah) April 11, 2021
This is the way the app was designed to work. https://t.co/tBlx4o6JVj
Reporting cybersecurity topics
But these two incidents are just the symptoms of a bigger problem with modern-day news reporting, especially on cybersecurity topics.
The first issue is that most news agencies don't have dedicated cybersecurity reporters who would normally have the training and expertise to spot fake leaks and avoid causing reputational damage to companies via misleading reports.
Second, many reporters are more than glad to defer responsibility in their articles. There is a growing trend among news outlets where they pick up stories from one another and almost never confirm the original report by themselves or through a second source.
If the news agency that broke a story makes a mistake or intentionally runs a misleading story for the sake of advertising traffic and notoriety, we have situations like the ones we've seen this week, with two major tech companies having to explain to their users that they have not been breached.
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.



