Dutch intelligence unmasks previously unknown Russian hacking group 'Laundry Bear'
A previously unknown Russian hacking group was exposed by the Dutch intelligence services on Tuesday and blamed for a series of hacks on organizations in the Netherlands last year, including one impacting the national police.
The Ministry of Defence announced that the country’s intelligence agencies — the General Intelligence and Security Service (AIVD) and the Military Intelligence and Security Service (MIVD) — were calling the group “Laundry Bear” and had submitted a technical attribution and advisory about the hacks to the Dutch parliament.
Referencing the Dutch exposure, Microsoft said it was tracking the group as Void Blizzard and assessed it had been active globally since at least 2024, albeit with a disproportionate interest in NATO member states and Ukraine.
It follows a united effort by Western intelligence agencies, including those in the Netherlands, to expose another Russian hacking campaign last week blamed on APT28, a threat cluster previously attributed to unit 26165 of the GRU, Russia’s military intelligence agency.
The Dutch services stated that attacks by Laundry Bear “overlap with the modus operandi of APT28” — also known as Fancy Bear and Blue Delta — but that it considers them to be two different threat actors.
To-date, Laundry Bear has only been identified conducting non-destructive cyberattacks “most likely for espionage purposes,” penetrating cloud email environments such as Microsoft Exchange servers, to steal “emails and information about email contacts […] on a large scale and at a high speed,” according to the Dutch.
The speed and scale of the group’s operations are likely to be driven by a degree of automation in the attack chain, state the intelligence agencies, describing it as “so efficiently designed that it results in many attacks in a short period of time.”
The advisory also warns that the group used “relatively simple techniques that can be difficult to detect” and avoids using its own malware, instead attempting to live off the land by utilising tooling already present on victims’ systems.
Microsoft said Void Blizzard had successfully compromised organizations in multiple sectors in Ukraine, including education, transportation and defense. The company said the group had been detected compromising accounts at a Ukrainian aviation organization that had previously been hacked by a group it tracks as Seashell Blizzard — a notorious sabotage group also known as APT44 and Sandworm — reflecting “Russia's long-standing interest in this organization and, more broadly, in aviation-related organizations since Russia's invasion of Ukraine in 2022.”
Early intrusion into Dutch police
Laundry Bear was uncovered following an investigation into what the Dutch intelligence services described as “an opportunistic cyber attack on the Dutch police in September 2024” that involved police officers’ work-related contact details being stolen.
In that incident, the hackers managed to gain access to a Dutch police employee’s account via a session hijacking attack where a cookie on the employee’s browser was potentially captured via infostealer malware and then purchased by the state-sponsored group via a criminal forum.
The AIVD and MIVD said they had not been able to determine whether other data had been compromised in the incident affecting the police, but believed it very likely other Dutch organizations had also been victims.
The technical investigation into the police incident established it was carried out “by a previously unknown, very likely Russian state-sponsored cyber actor” which the Dutch advisory stated had been carrying out cyber attacks against Western governments, companies and other organizations since at least last year.
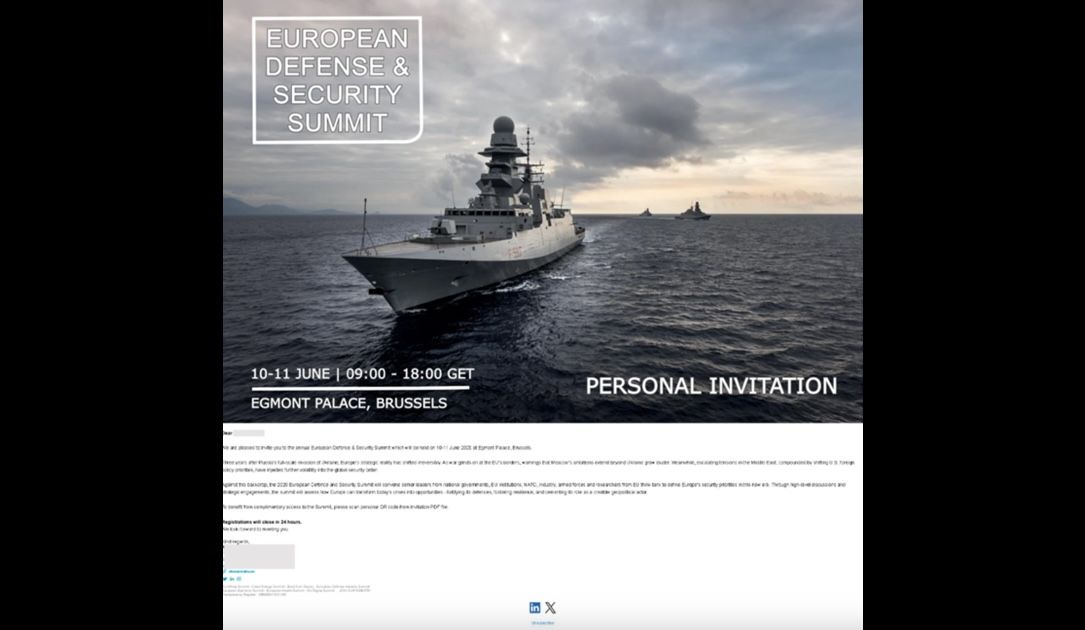
Screenshot of phishing lure used by the hacking group known as Void Blizzard or Laundry Bear. Image: Microsoft
Microsoft said it had identified Void Blizzard sending phishing emails posing as an organizer from the European Defense and Security Summit as recently as last month. The lure was a PDF attachment offering a fake invitation to a credential-stealing page.
Its targets have focused on matters “directly relevant to the Russian war effort in Ukraine” according to the Dutch advisory, including the defense ministries of NATO countries, their representatives in other organizations, military units and defense contractors. The advisory states that defense, aerospace and space technology companies that produce military equipment were targeted last year.
“Technical research carried out on [these] victims shows that Laundry Bear was very likely seeking to obtain (sensitive) information about the purchase and production of military equipment by Western governments and Western arms deliveries to Ukraine. The services see that the actor appears to have some degree of knowledge about the production and delivery of defense equipment and the subcomponents required for this.
“In addition, Laundry Bear has also carried out cyber attacks against companies that produce high-end technologies that Russia has difficulty obtaining due to current Western sanctions. The exact targets of these espionage attacks cannot be determined with the current information,” states the advisory.
Laundry Bear has also targeted civilian entities, including NGOs and organizations in the media and the education sector. The Dutch advisory stressed that its civilian targeting was particularly concentrated on entities in the IT and technology sector, where digital service providers to large organizations, for instance governments, could "also offer direct or indirect access to information or networks of their customers.”
Microsoft said it had observed Void Blizzard abusing legitimate cloud APIs, such as those for Exchange Online and Microsoft Graph, to enumerate users’ mailboxes and cloud-hosted files before automating its bulk collection of cloud-hosted data — in some cases including Microsoft Teams conversations — that the compromised user’s account can access.
Despite the decision to go public about Laundry Bear, the Dutch intelligence services said they don't have full insight into its activities and are hoping to enable other parties to document similar cyberattacks and take the right measures to protect themselves.
Alexander Martin
is the UK Editor for Recorded Future News. He was previously a technology reporter for Sky News and a fellow at the European Cyber Conflict Research Initiative, now Virtual Routes. He can be reached securely using Signal on: AlexanderMartin.79



