Kaseya zero-day involved in ransomware attack, patches coming
Remote management software vendor Kaseya said it identified and is currently mitigating a vulnerability that was abused in a recent incident that saw ransomware deployed on the networks of thousands of companies worldwide.
The incident took place on Friday, July 2, right as most IT teams in the US were preparing to log off for the extended July 4 US weekend.
Initial reports claimed that a ransomware gang might have gained access to Kaseya's backend infrastructure and abused it to deploy a malicious update to VSA servers running on client premises.
The malicious update was used to install a version of the REvil ransomware from the VSA server to all connected workstations, effectively infecting the networks of other third-party companies that were connected to attacked VSA systems.
How did the attackers learn of the vulnerability?
But in a blog post today, DIVD, a Dutch cybersecurity organization, said the attackers were using a vulnerability in the Kaseya VSA servers that one of its researchers identified weeks before.
Wietse Boonstra, a DIVD researcher, has previously identified a number of the zero-day vulnerabilities [CVE-2021-30116] which are currently being used in the ransomware attacks. And yes, we have reported these vulnerabilities to Kaseya under responsible disclosure guidelines (aka coordinated vulnerability disclosure).
Victor Gevers, DIVD Chair
DIVD Chair Victor Gevers said that Kaseya was in the process of fixing the vulnerability when the July 2 attacks took place.
Gevers couldn't say how details about the VSA vulnerability reached the ransomware gang.
After this crisis, there will be the question of who is to blame. From our side, we would like to mention Kaseya has been very cooperative. [...] They showed a genuine commitment to do the right thing. Unfortunately, we were beaten by REvil in the final sprint, as they could exploit the vulnerabilities before customers could even patch.
Victor Gevers, DIVD Chair
When asked by The Record, Gevers refused to share details about the nature of the vulnerability the ransomware gang exploited on Friday, but in a Reddit comment, security firm Huntress Labs, which was one of the first security firms to spot the attacks, said that most signs point to an authentication bypass vulnerability in the VSA web interface.
The vulnerability appears to have been used to bypass authentication on the VSA web panel and then run SQL commands on the VSA appliance and deploy ransomware to all connected clients. On customer networks, the VSA appliance deployed a "VSA agent hotfix" package that bypassed antivirus solutions using an older and vulnerable versions of the Microsoft Defender app, which it used to encrypt local workstations.
A Kaseya spokesperson told The Record they can't comment on an ongoing criminal investigation; however, in an update on Saturday, the company said they have now identified the vulnerability used in the attack and were preparing mitigations.
The company also said it hired security firm FireEye to help with its investigation into the hacks, along with several other security firms. It also released a new tool called the "Compromise Detection Tool" to all customers owning an on-premises VSA server to help owners identify if their server has been hacked during Friday's attacks.
Most VSA servers have been taken offline
The Friday attack could have been much worse if Kaseya did not intervene to shut down its own cloud-based infrastructure and also urge all VSA owners to take servers offline.
DIVD, which has scanned the internet for all VSA servers, said that less than 140 servers are still connected online today from the 2,200 servers it initially saw before the attacks.
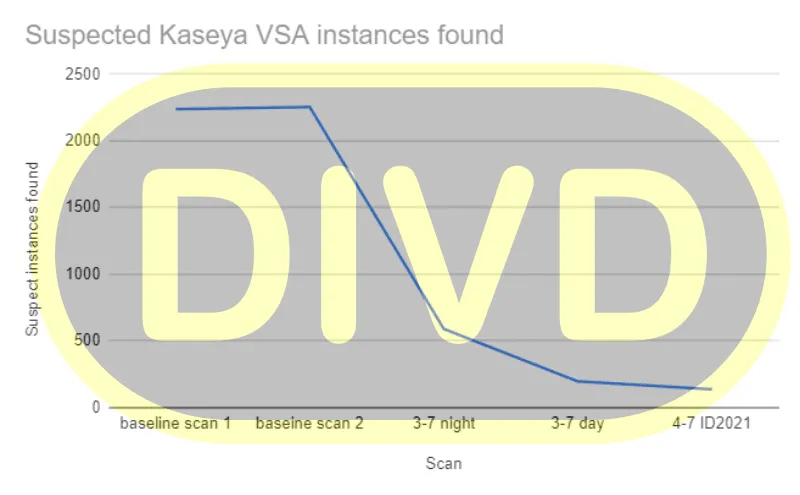
The breadth of the Friday attack on Kaseya VSA servers will take a few days to come to light.
On Friday, Kaseya CEO Fred Voccola told The Record that only less than 40 of its thousands of customers had VSA servers hacked and abused to deploy ransomware.
However, most of these VSA servers were used by managed service providers (MSPs), which are companies that manage the infrastructure of other customers; meaning the attackers most likely deployed ransomware to thousands of enterprise networks even if they only hacked less than 40 VSA servers.
MSPs that have admitted to being impacted during the Friday attacks include Visma EssCom, Synnex, and Avtex.
On Saturday, antivirus vendor ESET said it detected a spike of REvil ransomware infections, which they linked to the ongoing Kaseya incident.
"First wave happened at 18:30, second between 20:45 and 21:55 CEST," an ESET spokesperson told The Record.
According to the company's telemetry, most of the infections came from systems located in the UK, followed by South Africa, Germany, and the US.
Based on #ESET’s telemetry, we have identified victims in the UK, South Africa, Canada, Germany, USA, Colombia, Sweden, Kenya, Argentina, Mexico, the Netherlands, Indonesia, Japan, Mauritius, New Zealand, Spain and Turkey so far. 2/3 pic.twitter.com/CSzOai0uwq
— ESET research (@ESETresearch) July 4, 2021
The Kaseya/REvil incident is currently considered the largest ransomware outbreak carried out by a cybercrime gang. While the three 2017 ransomware outbreaks (WannaCry, NotPetya, and Bad Rabbit) were larger, they were linked to nation-state actors, and not a financially-focused threat actor like REvil, considered today's most advanced Ransomware-as-a-Service operator.
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.



