Kaseya: More than 1,500 downstream businesses impacted by ransomware attack
Florida-based software provider Kaseya said that fewer than 60 of its customers and fewer than 1,500 downstream businesses have been impacted by the ransomware attack that took place last Friday, on July 2.
In a message posted to its customers on Monday evening, the company updated initial stats provided on Saturday, the day after the attack, increasing the number of direct Kaseya customers from 40 to 60.
These are customers who were running an on-premises version of the company's VSA product, a web-based platform used by large companies to manage workstations and servers in remote locations.
On Friday, a group affiliated with the REvil cybercrime gang used an exploit for a VSA bug to take over VSA servers deployed across the globe and deploy a copy of the REvil ransomware to all workstations connected to the VSA platform.
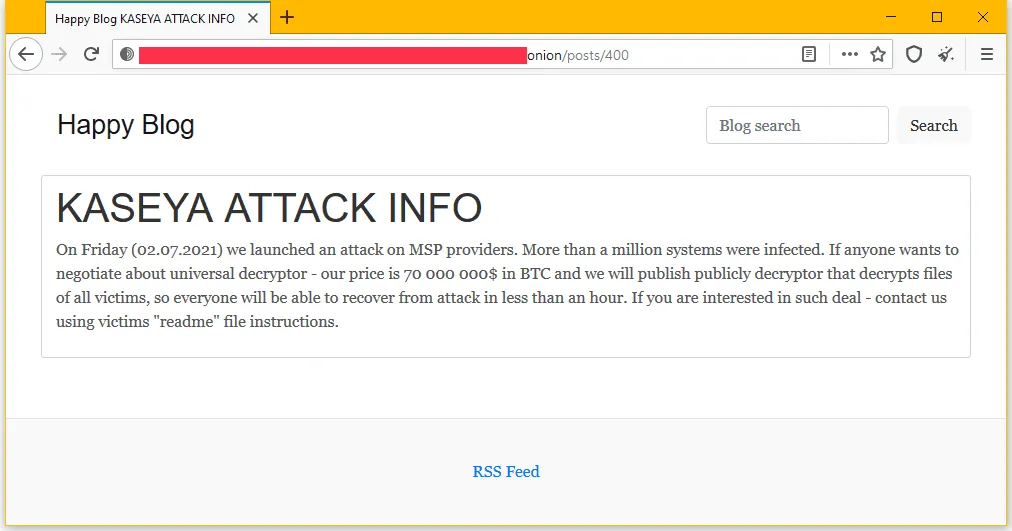
In a message posted on its dark web portal, the REvil gang claimed to have infected and encrypted files on more than one million systems during the attack and demanded a $70 million ransom payment to release a universal decrypter that can unlock all files for all Kaseya customers.
While Kaseya said that VSA servers at less than 60 of its customers were exploited to deploy ransomware, the attack is staggering in size, as most of Kaseya's customers are managed service providers (MSPS), companies paid to manage IT infrastructure, all of which have hundreds or thousands of their own customers.
REvil's attacks on Kaseya VSA servers have led to outages in unexpected places, such as supermarket chains in Sweden, kindergartens in New Zealand, and some public administration offices in Romania.
However, the true impact of these attacks is still shrouded in mystery. Only five MSPs have publicly admitted to being impacted by the REvil attacks on Kaseya servers—namely VelzArt, Hoppenbrouwers, Visma EssCom, Synnex, and Avtex.
While Kaseya has been trying to be open, the company is not viewed in a favorable light since ransomware gangs have previously targeted its software to orchestrate attacks.
Furthermore, Kaseya has also come under criticism for using an ancient technology such as ASP for the web interface of its VSA product, a decision that may weigh heavily in the class-action lawsuits that are no doubt being prepared to be filed in the coming weeks.
In the meantime, the company has released tools for MSPs to scan their systems for signs of exploitation.
Kaseya said that only on-premises VSA servers were vulnerable to the bug exploited during the attack, and that its cloud-based SaaS platform should be fine to use, once the company restores it this week.
The Florida company, however, recommended that MSPs keep their VSA servers offline until it releases a formal patch to address the vulnerability exploited on Friday.
A recorded interview was also released after this article's publication, available below:
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.

