Just a handful of Android apps exposed the data of more than 100 million users
Almost half a decade after the first reports were published, mobile app developers are still exposing their users' personal information through abhorrently simple misconfigurations.
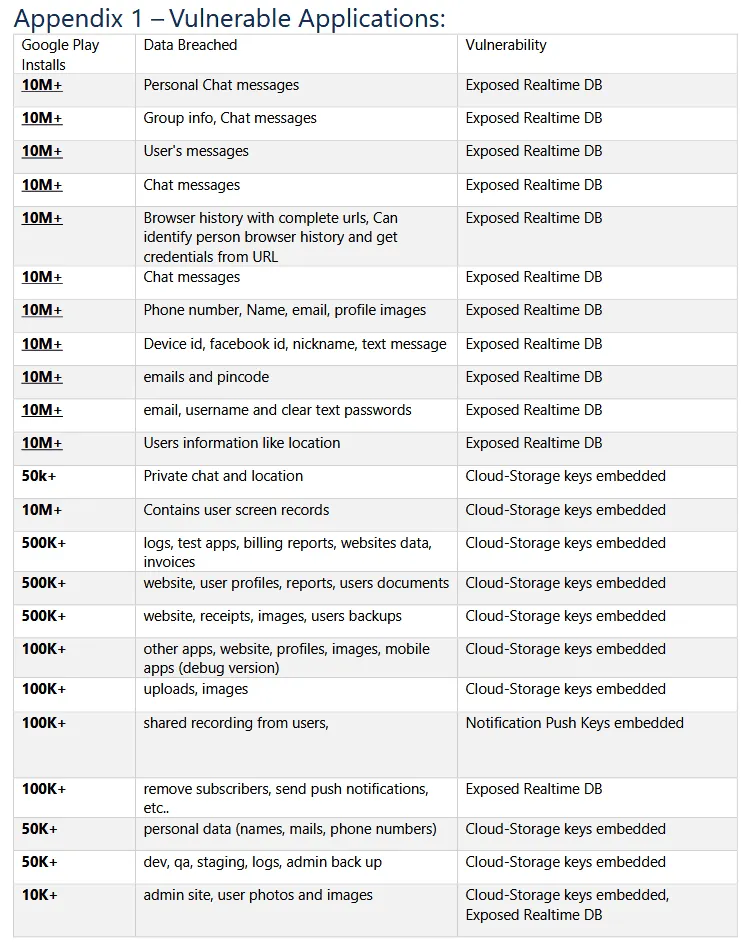
In a report published earlier today, security firm Check Point said it found 23 Android applications that exposed the personal data of more than 100 million users through a variety of misconfigurations of third-party cloud services.
This included developers who forgot to password-protect their backend databases and developers who left access tokens/keys inside their mobile application's source code for services such as cloud storage or push notifications.
The Check Point team said it was able to use the information they found through a routine examination of 23 random applications and access the backend databases of 13 apps.
In the exposed databases, researchers said they found information such as email addresses, passwords, private chats, location coordinates, user identifiers, screen recordings, social media credentials, and personal images.
"This misconfiguration of real-time databases is not new, and continues to be widely common, which affects millions of users," the researchers said.
"All CPR researchers had to do was to attempt to access the data. There was nothing in place to stop the un-authorized access from happening."
Leaving push services open—the new trend!
Furthermore, while some apps didn't expose user data directly, Check Point said these mobile apps exposed access keys that would have allowed a threat actor to send push notifications to all of the app's users—something that could be abused for very efficient phishing attacks.
"Imagine if a news-outlet application pushed a fake-news entry notification to its users that directed them to a phishing page. Since the notification originated from the official app, the users would assume the notification was legitimate and sent by the news outlet and not hackers," the security firm said.
Unfortunately, Check Point only shared the names of five of the 23 apps that exposed information through their backends—Logo Maker, Astro Guru, T'Leva, Screen Recorder, and iFax.
Nevertheless, the issues described in the company's report are not new, nor will this be the last time we hear a security firm gripe about this type of developer mistake and data exposure.
Reports about mobile apps which expose user data by leaving backend infrastructure exposed online have been published regularly since the mid-2010s, and the issue has continued to linger, primarily due to bad coding practices.
The latest of these reports came from mobile security firm Zimperium back in March this year, when the company reported finding misconfigured cloud-based backends in thousands of Android and iOS apps.
The Zimperium report contained numbers almost identical to a 2018 Appthority report, showing that literally nothing had changed over the previous three years despite repeated warnings.
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.



