CISA: Ivanti hacks targeting Norway began in April
Hackers began exploiting a new vulnerability in Ivanti products to target the Norwegian government at least as early as April, according to a new joint advisory from cyber agencies in the U.S. and Norway.
Alarm has grown since Norway confirmed last week that hackers connected to an unnamed government had compromised a dozen state ministries in the country through Endpoint Manager Mobile, which is made by Ivanti and formerly known as MobileIron Core.
The software is used by governments across the world, including multiple U.S. state and federal agencies, according to a search on security platform Shodan.
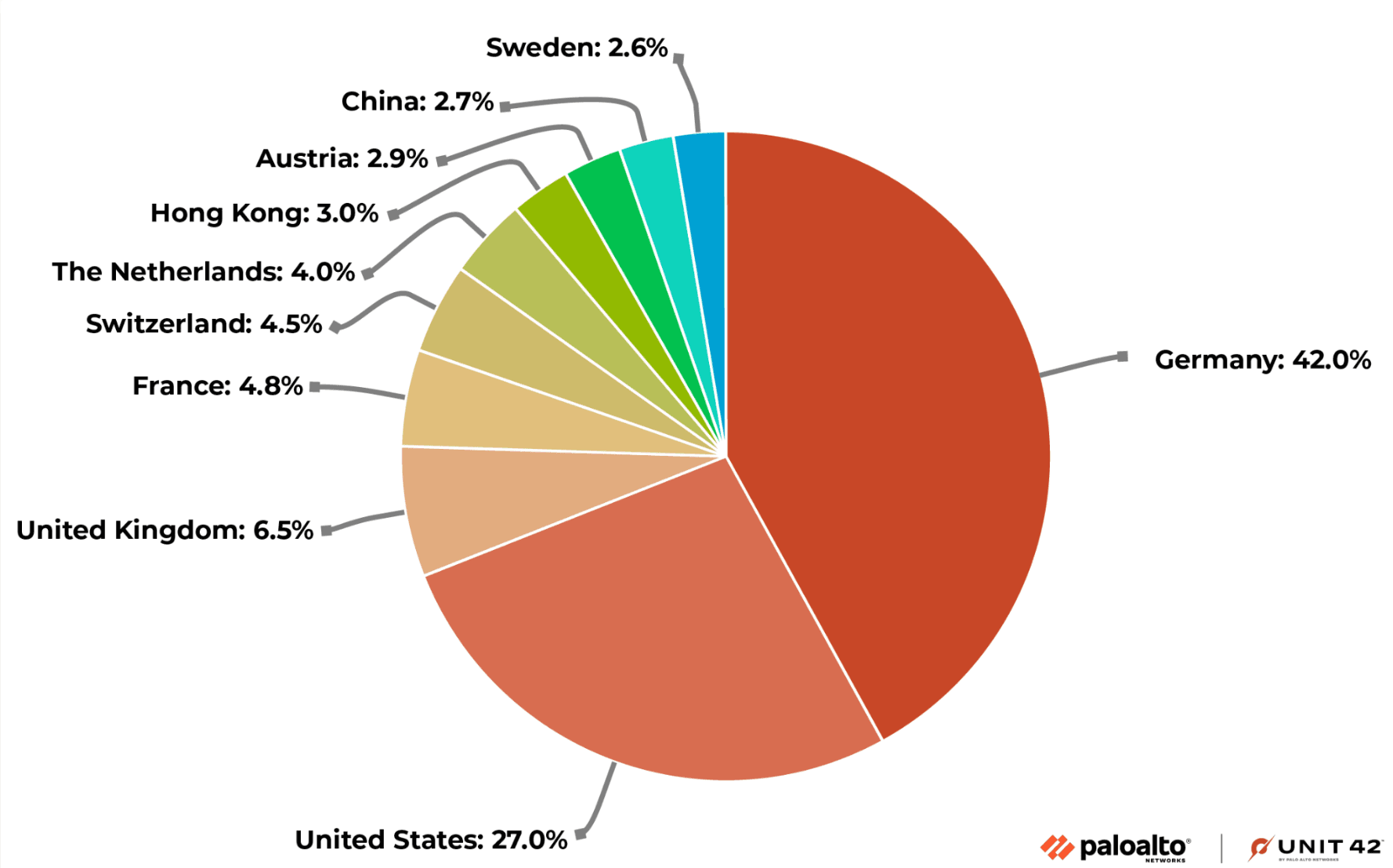 The global distribution of Ivanti Endpoint Manager Mobile servers. Credit: Palo Alto Networks
The global distribution of Ivanti Endpoint Manager Mobile servers. Credit: Palo Alto Networks
The vulnerabilities allow threat actors to access personally identifiable information, like names, phone numbers, and other mobile device details; make configuration changes to vulnerable systems; push new packages to mobile endpoints; and access Global Positioning System (GPS) data if enabled.
In an advisory on Tuesday, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) and the Norwegian National Cyber Security Centre (NCSC-NO) said that after an investigation, they confirmed that hackers began exploiting the zero-day vulnerability in April, months before the issue was discovered.
“Advanced persistent threat (APT) actors exploited CVE-2023-35078 as a zero day from at least April 2023 through July 2023 to gather information from several Norwegian organizations, as well as to gain access to and compromise a Norwegian government agency’s network,” the agencies said.
“Mobile device management (MDM) systems are attractive targets for threat actors because they provide elevated access to thousands of mobile devices, and APT actors have exploited a previous MobileIron vulnerability. Consequently, CISA and NCSC-NO are concerned about the potential for widespread exploitation in government and private sector networks.”
Ivanti, which assisted with the advisory, released its own notice on Friday explaining that hackers were exploiting a second vulnerability that, when combined with the first issue, allowed them wider access to compromised systems.
Ivanti released a patch for the first issue on July 23 and another for the second on July 28. CISA added the bug to its catalog of Known Exploited Vulnerabilities, giving federal civilian agencies until August 21 to patch it.
CISA and NCSC-NO urged agencies to use the advisory to search their systems for potential compromise and immediately report the issue to them.
While the current APT group exploiting the vulnerability was not identified, and CISA did not respond to requests for comment, the agency said in 2020 that Chinese hacking groups had exploited past vulnerabilities affecting MobileIron.
The current campaign also involved small office or home office routers, including from ASUS, used as proxies to obscure the source of the attacks.
Cybersecurity firm GreyNoise said there has been a stark increase in the number of IP addresses attempting to exploit CVE-2023-35078 since Sunday.
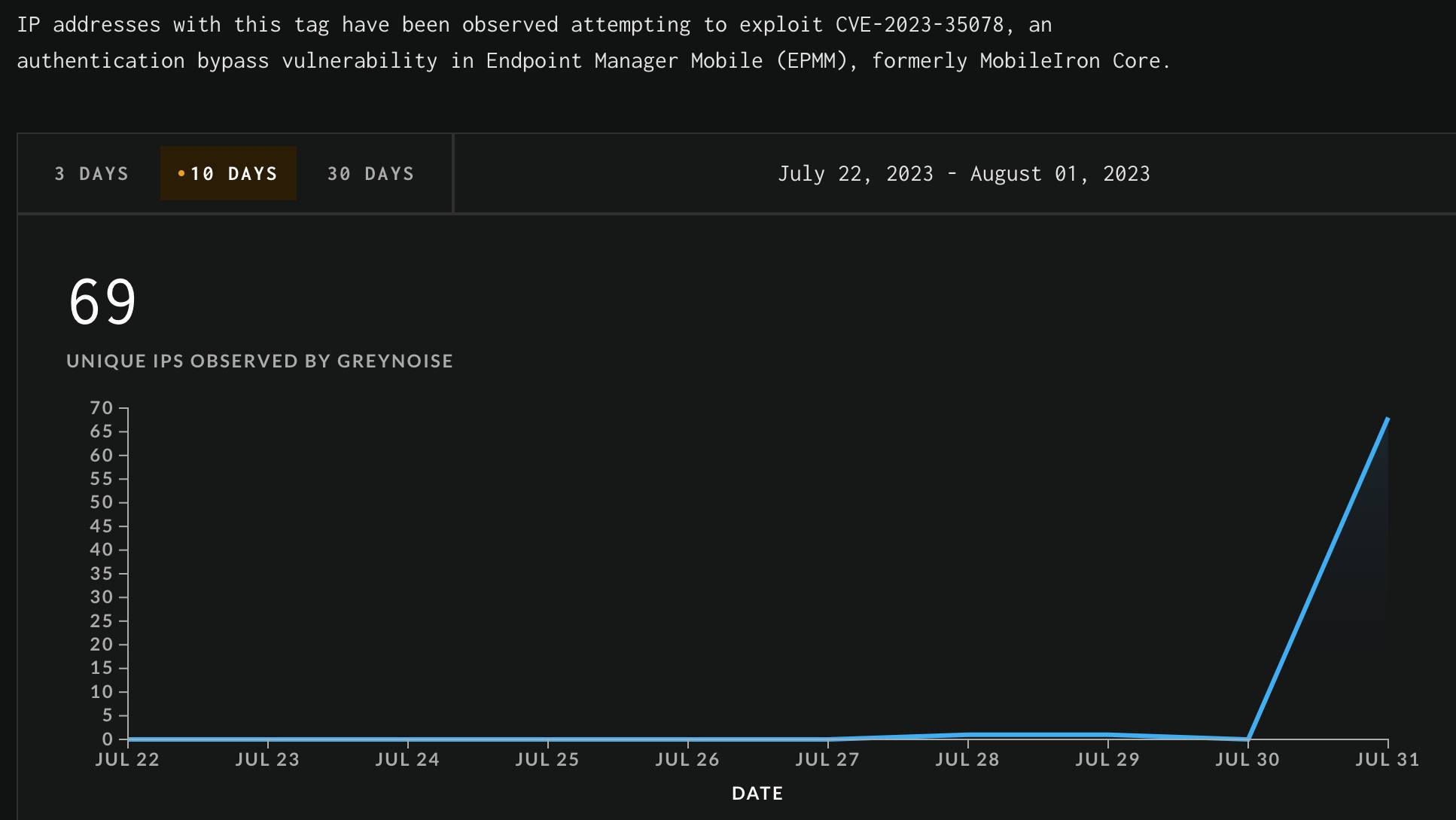 Credit: GreyNoise
Credit: GreyNoise
According to Palo Alto Networks’ Unit 42, 85 countries host 5,500 Ivanti Endpoint Manager Mobile servers, with both Germany and the U.S. having more than 1,000 servers.
After announcing that its systems were breached last Monday, Sofie Nystrøm, director of Norway’s National Security Agency, confirmed that the Ivanti vulnerability was used in the attack.
“This vulnerability was unique, and was discovered for the very first time here in Norway,” Nystrøm said. “If we had released the information about the vulnerability too early, it could have contributed to it being misused elsewhere in Norway and in the rest of the world.”
Jonathan Greig
is a Breaking News Reporter at Recorded Future News. Jonathan has worked across the globe as a journalist since 2014. Before moving back to New York City, he worked for news outlets in South Africa, Jordan and Cambodia. He previously covered cybersecurity at ZDNet and TechRepublic.



