Iranian state-sponsored group APT35 linked to Memento ransomware
Security researchers have found links between APT35, one of Iran's most active cyber-espionage groups, and Memento, a ransomware strain that was deployed in attacks in the fall of 2021.
The links, discovered and detailed in a report published today by cybersecurity firm Cybereason, show, once again, the duality of Iranian cyber-espionage operations.
The report comes to reinforce recent observations from industry insiders that have seen Iranian hacking groups carry out indiscriminate attacks against a wide range of targets.
These groups, mostly operating as contractors for the Iranian government, scan the web for popular types of servers and use exploits for recently disclosed vulnerabilities to gain control over unpatched systems. If the compromised networks belong to an entity of interest to the Iranian government, the groups deploy malware that can be used to harvest information from the hacked systems and maintain persistent access for future intelligence collection.
However, if the target has no value for the attackers, access to these systems is either sold on underground forums or monetized by the threat actors themselves, who have been seen deploying ransomware to extort some of these targets.
PowerLess investigation leads to Memento attacks
Today, Cybereason said it found a new strain of malware developed by the APT35 (aka Phosphorus, Charming Kitten) group.
Named PowerLess, written in PowerShell, and deployed on hacked Microsoft Exchange servers last year, Cybereason said APT35 used this malware for its intelligence collection targets.
But, while investigating this new threat, Cybereason said it also found several clues that linked APT35's infrastructure to past attacks of the Memento ransomware gang.
This included shared IP addresses, similar file naming schemes, and similar URL directory patterns—findings that led researchers to believe that APT35 operators were also likely behind the Memento ransomware as well.
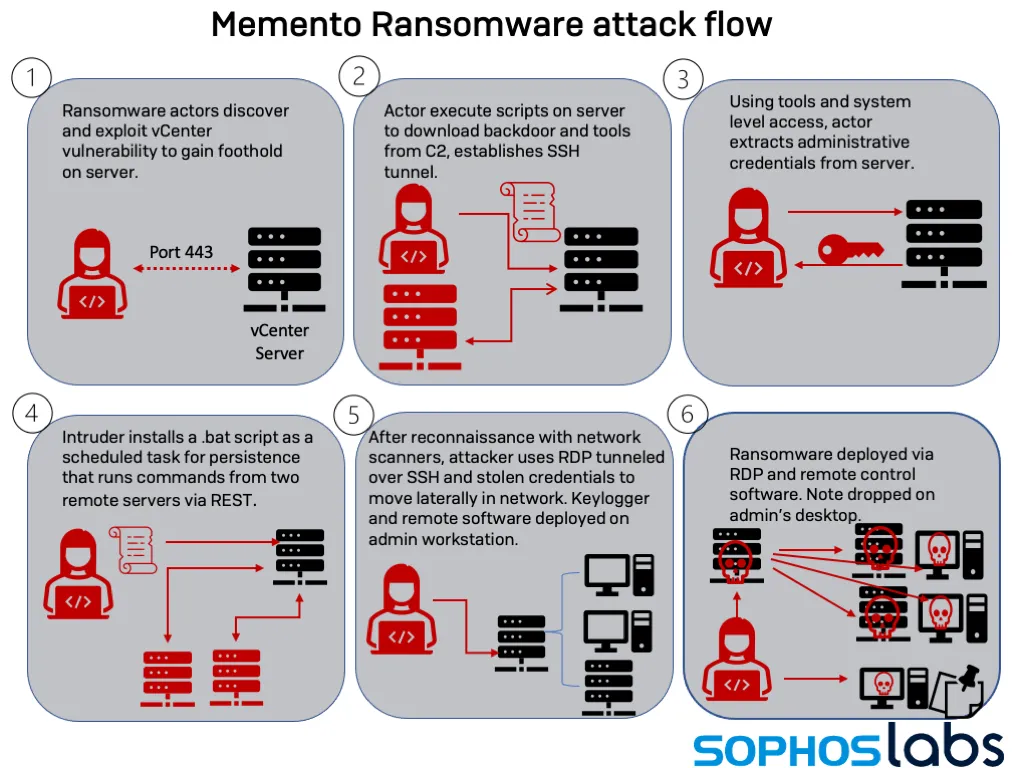
Discovered last year by Sophos, Memento was seen being deployed on corporate networks via unpatched VMWare vCenter servers towards the end of last year.
Sophos highlighted Memento attacks because the ransomware featured a unique failsafe mechanism where it locked files inside password-protected WinRAR archives in case the main file encryption operation failed.
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.



