Iranian cloud company accused of hosting cybercriminals, nation-state hackers
An Iranian technology company is providing infrastructure services to ransomware gangs and an array of nation-state hackers, researchers have found.
A report released Tuesday by the cybersecurity firm Halcyon details how the internet service provider Cloudzy accepts cryptocurrency in exchange for the anonymous use of technological services used to carry out cyberattacks.
The company allegedly provides a range of services to prolific ransomware gangs like BlackBasta and Royal while also serving as the backbone of attacks for government hackers from North Korea, Russia, China, India, Pakistan, and Vietnam. The infrastructure is even allegedly used by controversial Israeli spyware vendor Candiru.
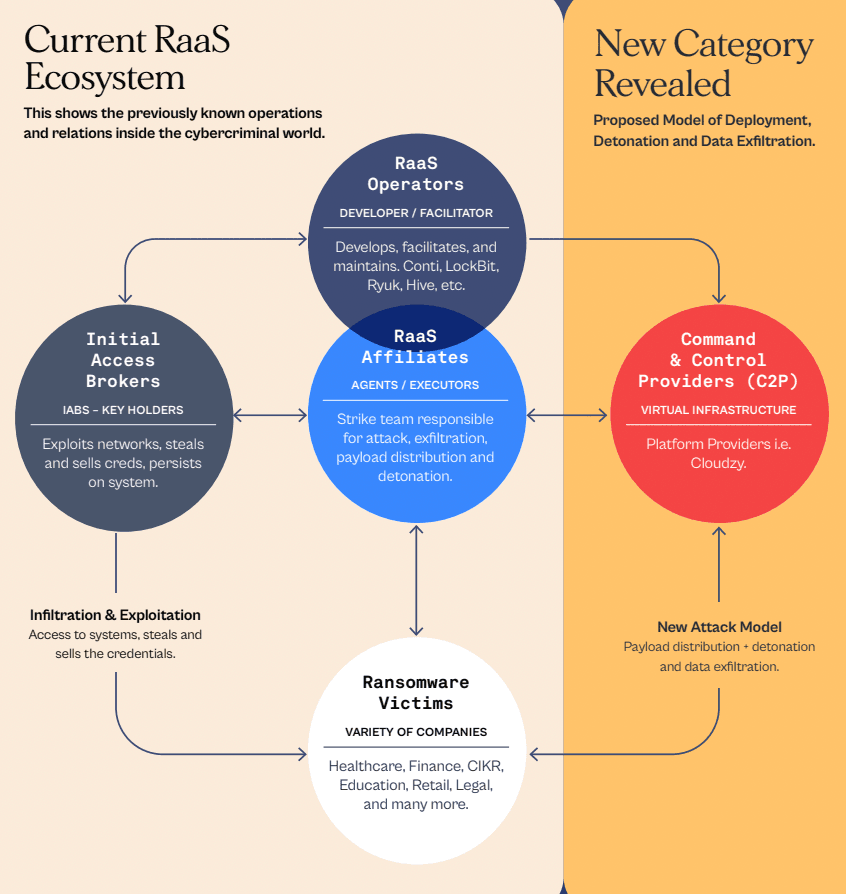
ISPs like Cloudzy are called “Command-and-Control Providers” (C2P), which Halcyon described as a “relatively unknown dimension of the ransomware economy.”
“What stood out most to us is the fact that we have ostensibly legitimate ISPs providing attack infrastructure to nation-state threat actors, ransomware operators, and other possibly sanctioned entities while under no obligation to take any action whatsoever to stem the illicit activity,” Ryan Smith, CTO and co-founder at Halcyon, told Recorded Future News.
“In fact, they are profiting from it… These Command and Control Providers — knowingly or unknowingly — are essentially another pillar in the global attack ecosystem, and a major player in the ransomware economy.”
On its face, Cloudzy operates as a legitimate business, with Twitter and LinkedIn profiles. The company’s CEO, Hannan Nozari, is active on several social media sites but did not respond to requests for comment about the report’s findings. The company claims to be located in the U.S. but according to researchers is actually based in Tehran.
Cloudzy, according to Halcyon researchers, provides Remote Desktop Protocol (RDP) and Virtual Private Server (VPS) services and more without asking customers what they are being used for.
Criminal and state-sponsored hackers use the technology to not only muddy the waters for those trying to track down where malicious activity originates but also to provide hosting platforms for tools used during attacks.
Ghost Clown and Space Kook
The researchers began their investigation with an examination of the actions of two ransomware affiliates they call “Ghost Clown” and “Space Kook,” which use the BlackBasta and Royal ransomware strains, respectively.
After gaining initial entry into a system, the hackers used an IP address through Cloudzy. The researchers noted that Ghost Clown initially used Conti ransomware starting in February 2021 before switching to Black Basta in 2022.
Space Kook used infrastructure tied to an initial access broker known as Exotic Lily by Google’s Threat Analysis Group. Space Kook started out deploying the Quantum Locker ransomware before switching to the Royal ransomware.
Halcyon researchers followed the breadcrumbs left by these two affiliates through a maze of service providers which led them to Cloudzy.
“Initially, Halcyon suspected that the person or entity doing the leasing was a criminal infrastructure broker, a part of the underground ransomware ecosystem, akin to an initial access broker or malware developer,” they wrote.
“To our surprise, Halcyon was able to successfully purchase servers with the identified RDP hostnames from one of the ISPs, and only one: the C2P Cloudzy. More precisely, these hostnames appeared on servers provisioned using their ‘RDP VPS’ service. We had our answer.”
From there, they realized that Cloudzy’s services were being used by several ransomware affiliates and expanded their search, discovering a “staggering array of attack infrastructure which we, and others in the security community, recognized and associated with a wide range of threat actors.”
Halcyon found a web of government-sponsored APT groups, criminal syndicates, and the commercial spyware vendor Candiru all using Cloudzy infrastructure.
They include Chinese government groups like APT10 and Dragon Castling; India’s Sidewinder and Bitter; Iran’s APT34 and APT33; North Korea’s Kimsuky and Konni; Pakistan’s TransparentTribe; Russia’s Nobelium and Turla; and Vietnam’s APT32.
Hackers deploying the Ryuk and Black Cat ransomware strains were also identified using the infrastructure alongside cybercrime organizations like Evil Corp.
 Credit: Halcyon
Credit: Halcyon
“At the time of writing, Halcyon estimated that potentially between 40% - 60% of the total servers currently hosted by the C2P Cloudzy appear to be directly supporting potentially malicious activity,” the researchers wrote.
“Given the significant amount of threat activity assessed to be tied to Cloudzy and the tangible impact that activity has had on society, Halcyon decided to investigate the business itself.”
Wyoming and Nevada
The researchers found that Cloudzy markets itself to both privacy enthusiasts and also threat actors, noting that when they purchased services from the company, it was “cheap, easy, and anonymous.”
The only thing needed was an email and cryptocurrency address. The company’s terms of service bans the use of their technology for various crimes but other parts of the agreement imply that only $250-$1000 fines would be issued if nefarious activity were discovered.
More digging led Halcyon to discover that much of the malicious activity being supported by Cloudzy was done through infrastructure rented by the company through 12 other ISPs in various countries: Combahton, DR-Soft, FranTech Solutions, Hostwinds, Hydra Communications, IPXO, Leaseweb, MB-Ricarta, OVH, Rockion, Velcom, and the Winstri Corporation.
When Halcyon researchers reported the ransomware activity to Cloudzy, the company sent “a series of responses that confused” them, and they were eventually told to contact the ISPs that had registered the IP addresses on their behalf.
Researchers were then able to find the company’s registration under its previous name, Router Hosting. The location: an office building in a strip mall in Sheridan, Wyoming, with registration filed on March 22. That building is currently for sale and Halcyon found that the address listed was “present in the incorporation records of more than 2,000 other companies.”
All of the companies were connected to Cloud Peak Law, a law firm specializing in anonymous company formation services. The researchers then discovered another address connected to the company located in Las Vegas.
That address was connected to Francisco Dias — a man profiled in the New Yorker in 2018 for his work as the web hosting provider for controversial Neo-Nazi websites like The Daily Stormer.
Cloud Peak Law did not respond to requests for comment.
Knife factory woes
Halcyon also examined Cloudzy’s employees through LinkedIn, finding a mix of fake profiles and real people. Almost all of them appear to be based in Tehran and work for another company called abrNOC.
Both Cloudzy and abrNOC have almost identical logos and were both started in 2008. They each claim to have more than 15 locations across the world — all of which are the same.
Nozari, the company’s founder, has a verified Twitter account where he comments mostly on cryptocurrency. While various profiles said he is located in New Zealand or the United Arab Emirates, Halcyon traced him back to Tehran. His profile on the company website says he started Cloudzy in 2008.
Nozari told Reuters that only an estimated 2% of their clients were involved in malicious activity.
“If you are a knife factory, are you responsible if someone misuses the knife? Trust me I hate those criminals and we do everything we can to get rid of them,” he said.
Halcyon urged defenders to watch out for the IP addresses listed in the report. They also warned that anyone doing business in the U.S. with Cloud Peak Law is at risk of violating U.S. sanctions on Iran.
Halcyon’s Smith told Recorded Future News that it is improbable that Cloudzy could have no idea whatsoever that more than half of the activity on its networks is malicious.
“They are providing services to threat actors that are absolutely essential to their attack operations, and they are doing it in plain sight with zero concern there will be any repercussions. Attackers can simply spin up virtual infrastructure anonymously and use it in attacks, then shut it down with a few clicks,” Smith said.
“If these services were not so easy to obtain, threat actors would need to have a significant lift in order to stand up and maintain attack infrastructure, and would have to undertake steps that could possibly make them more susceptible to being identified.”
Jonathan Greig
is a Breaking News Reporter at Recorded Future News. Jonathan has worked across the globe as a journalist since 2014. Before moving back to New York City, he worked for news outlets in South Africa, Jordan and Cambodia. He previously covered cybersecurity at ZDNet and TechRepublic.



