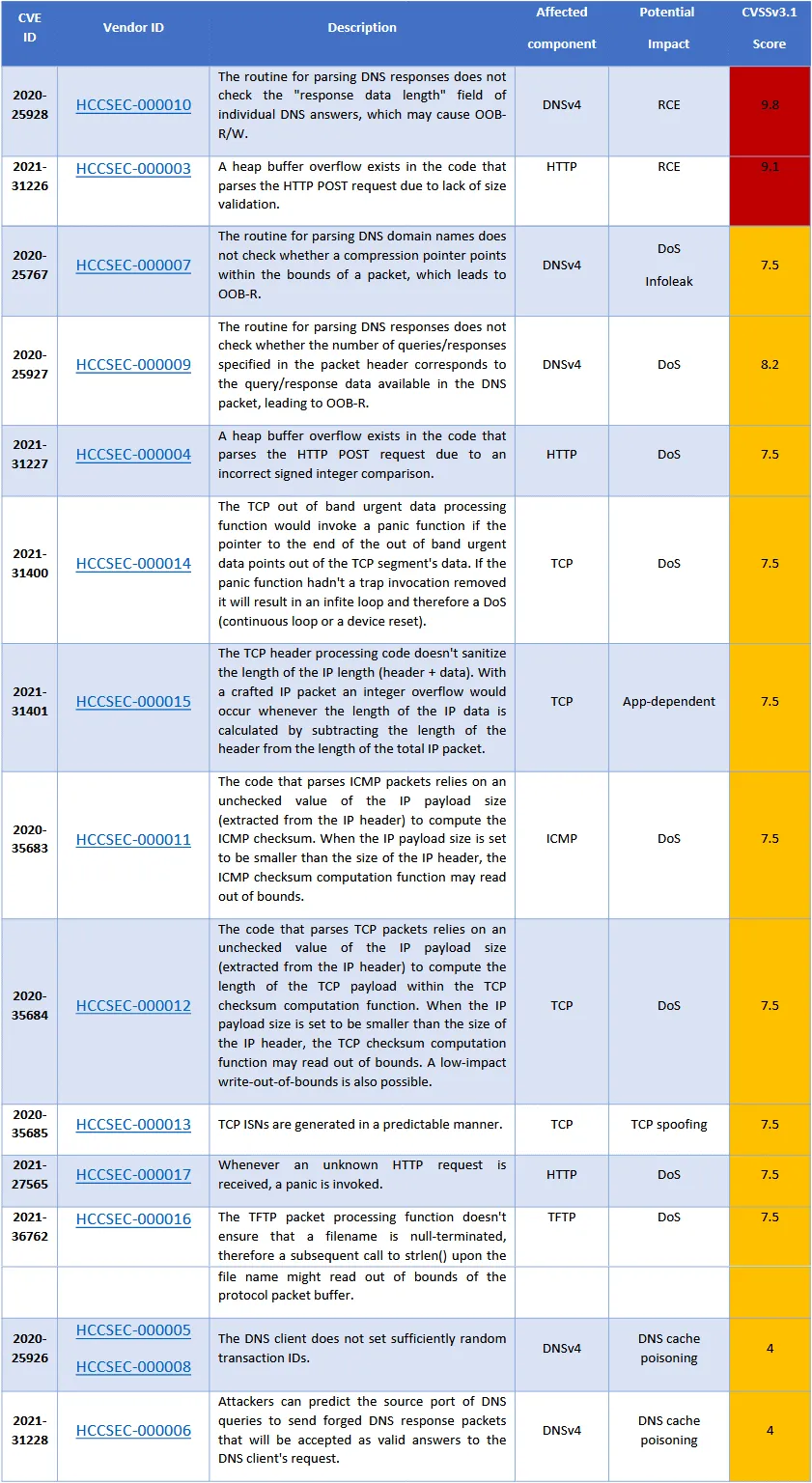
INFRA:HALT vulnerabilities affect OT devices from more than 200 vendors
Security researchers have disclosed today 14 vulnerabilities that impact a popular TCP/IP library commonly used in industrial equipment and Operational Technology (OT) devices manufactured by more than 200 vendors.
Collectively referred to as INFRA:HALT, the 14 vulnerabilities have been found as part of a joint research effort by the security teams at Forescout and JFrog.
Project Memoria, phase III
According to a report published today, the vulnerabilities affect NicheStack, a small C library provided by HCC Embedded that can be added to a device's firmware and allow it to support internet connectivity and other networking functions.
Also known as a "TCP/IP stack," these types of libraries are common in almost all devices; however, their code has hardly been reviewed in decades for security flaws.
In 2019, after the discovery of the URGENT/11 and Ripple20 vulnerabilities impacting common TCP/IP stacks, the Forescout team launched Project Memoria as a dedicated research operation to look into the security of all of today's most popular TCP/IP stacks.
The INFRA:HALT bugs announced today are the project's third set of bugs after Amnesia:33 and NUMBER:JACK.
But while the previous two research efforts focused on more common TCP/IP stacks used with routers, IoT devices, or web servers, this time around, the Forescout and JFrog teams had their sights on a library used for adding internet connectivity to industrial equipment typically found in factories, mines, pipelines, water treatment facilities, and other critical infrastructure working points.
"The new vulnerabilities allow for remote code execution, denial of service, information leak, TCP spoofing, or DNS cache poisoning," researchers explained.
A full list of the bugs, along with descriptions, is available below:
More than 6,400 OT devices are exposed online
To exploit any of the INFRA:HALT vulnerabilities, a threat actor would first need to gain access to a company's internal network and not just its office network but its OT section, a separate network where all industrial equipment is recommended to be installed.
However, while the bulk of companies typically know how to safeguard their OT networks, this doesn't mean that some don't intentionally or accidentally expose industrial equipment online.
Around 6,400 OT devices were found connected to the internet in March this year when the Forescout and JFrog teams discovered the INFRA:HALT vulnerabilities.
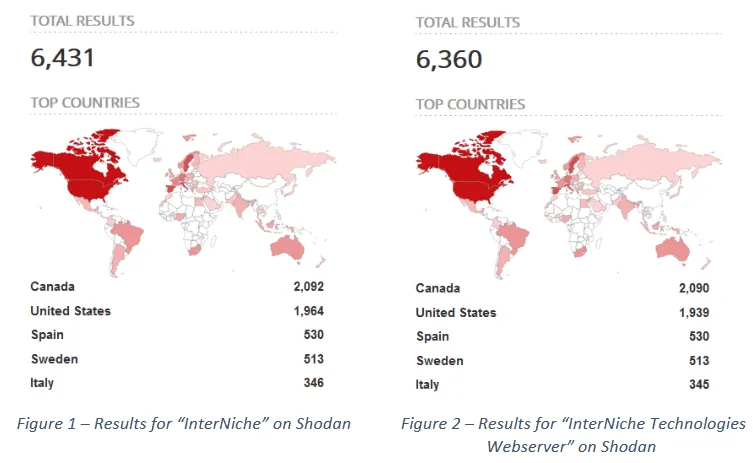
These devices are now vulnerable to attacks, and especially to attacks exploiting the CVE-2020-25928 and CVE-2021-31226 bugs that could allow attackers to take full control over a device remotely.
The good news for the more than 200 device vendors that use NicheStack is that HCC Embedded has prepared patches to address all issues.
The bad news is that by the time these patches make it into a firmware update and then the firmware is deployed on devices in the field, threat actors could have already exploited the INFRA:HALT issues to damage devices or even hinder OT operations.
Companies interested in finding if they use devices that run on the NicheStack TCP/IP stack, or other TCP/IP stacks previously identified as vulnerable in earlier research, can use Forescout's Project Amnesia scanner, available on GitHub.
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.



